Cloud data integrity verification method and system based on biological characteristics
A technology of integrity verification and biometrics, applied in the field of cloud data integrity verification based on biometrics, can solve problems such as falsification of certification materials, cumbersome background management, and complicated user use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The present invention will be described in further detail below in conjunction with specific examples, but the embodiments of the present invention are not limited thereto.
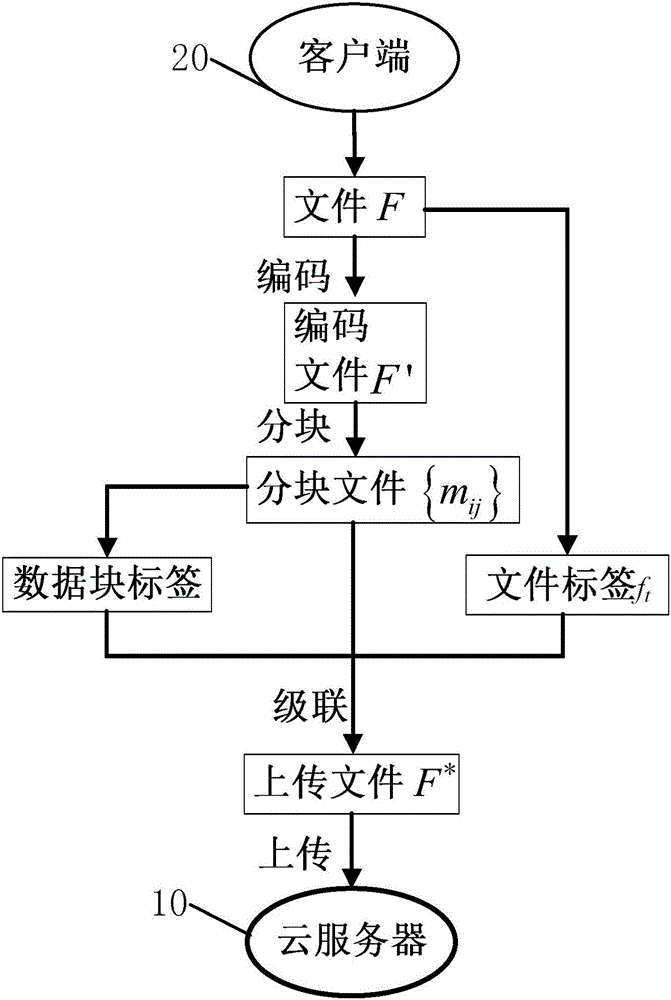
[0059] Based on the theory of cryptography, the present invention provides a method for realizing the verification of cloud data integrity based on biometrics. Compared with the traditional PKI-based or identity-based cloud data integrity verification method, the method of the present invention can provide higher security, and at the same time, the client and the third-party verifier do not need to maintain digital certificates, and do not need to save identity identifiers The verification can be completed, which greatly reduces the key management burden of the system. The fault tolerance provided by this scheme can perfectly deal with the problem of incomplete matching of biometric identity in two samplings. Therefore, the present invention not only promotes the development of cloud computing, bu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com