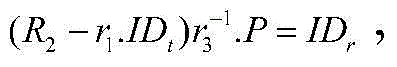RFID system safety authentication method with ECC combining with lightweight Hash function
A system security and authentication method technology, applied in the field of implantable RFID, can solve the problems of large communication overhead and memory requirements, low security level, etc., and achieve the effect of reducing communication overhead, high security level, and superior performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to further understand the content, features and effects of the present invention, the following examples are given, and detailed descriptions are given below with reference to the accompanying drawings.
[0030] Such as figure 1 As shown, the present invention is achieved in that a kind of RFID system security authentication method that ECC combines lightweight Hash function comprises:
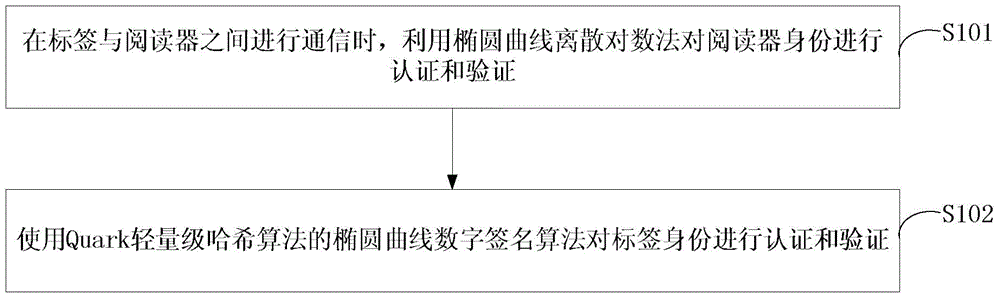
[0031] S101. When communicating between the tag and the reader, use the elliptic curve discrete logarithm method to authenticate and verify the identity of the reader;
[0032] S102. Use the elliptic curve digital signature algorithm of the Quark lightweight hash algorithm to authenticate and verify the tag identity.
[0033] Further, the methods for reader identity authentication and verification are:
[0034] Step 1. The reader selects a random number r 1 ∈ Z n and calculate R 1 = r 1 ;
[0035] Step 2: The reader initializes the corresponding i 1 value and will R 1 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com