Method for identity authentication of Internet user
An identity authentication and user technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as inconvenient, reduced revenue, increased operating costs, etc., to improve use security and reduce operating costs , the effect of reducing the cost burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The implementation of the present invention is described below through specific specific examples. Those skilled in the art can easily understand other advantages and effects of the present invention from the content disclosed in this specification, and can also be implemented or applied through other different specific examples.
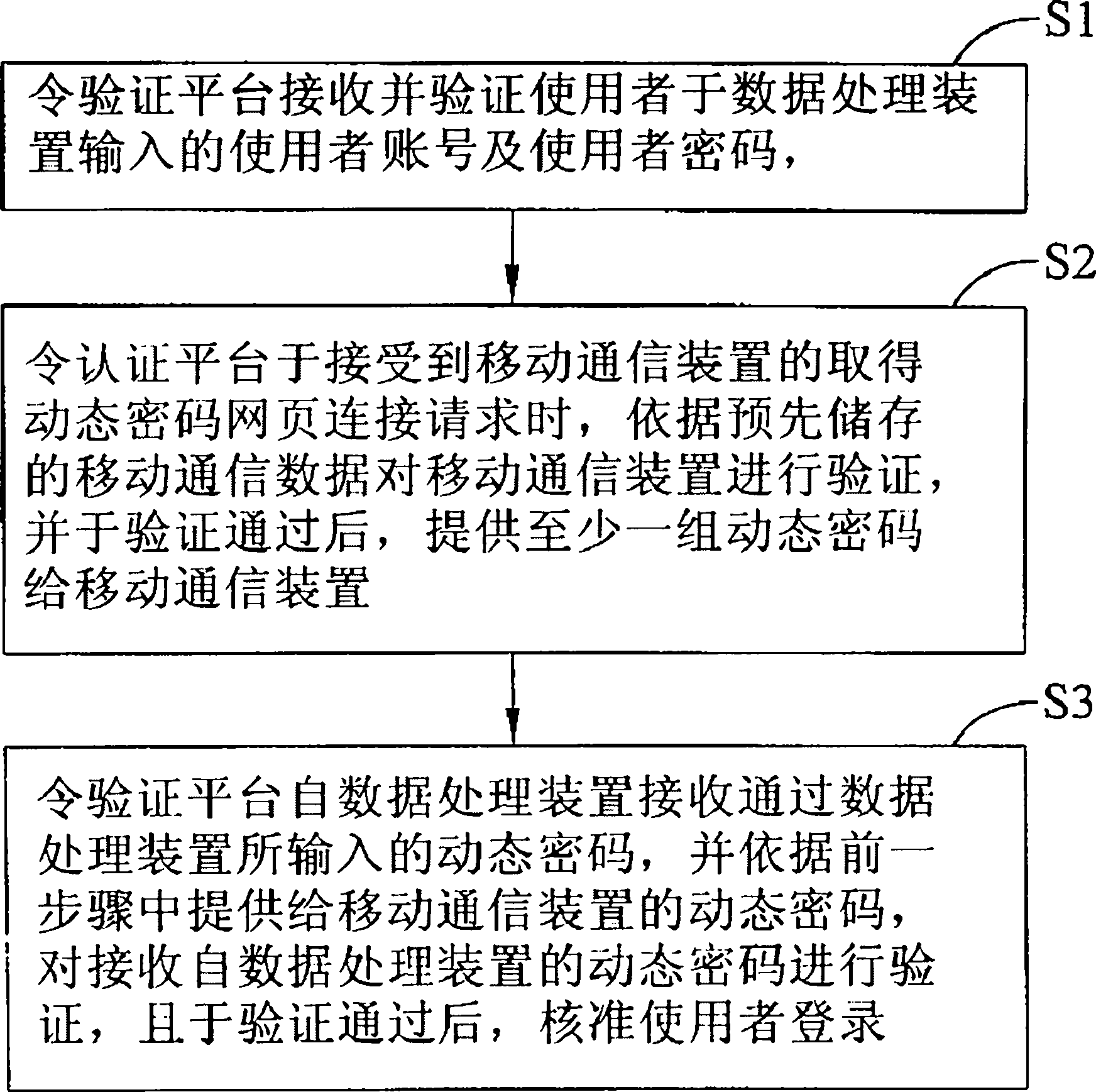
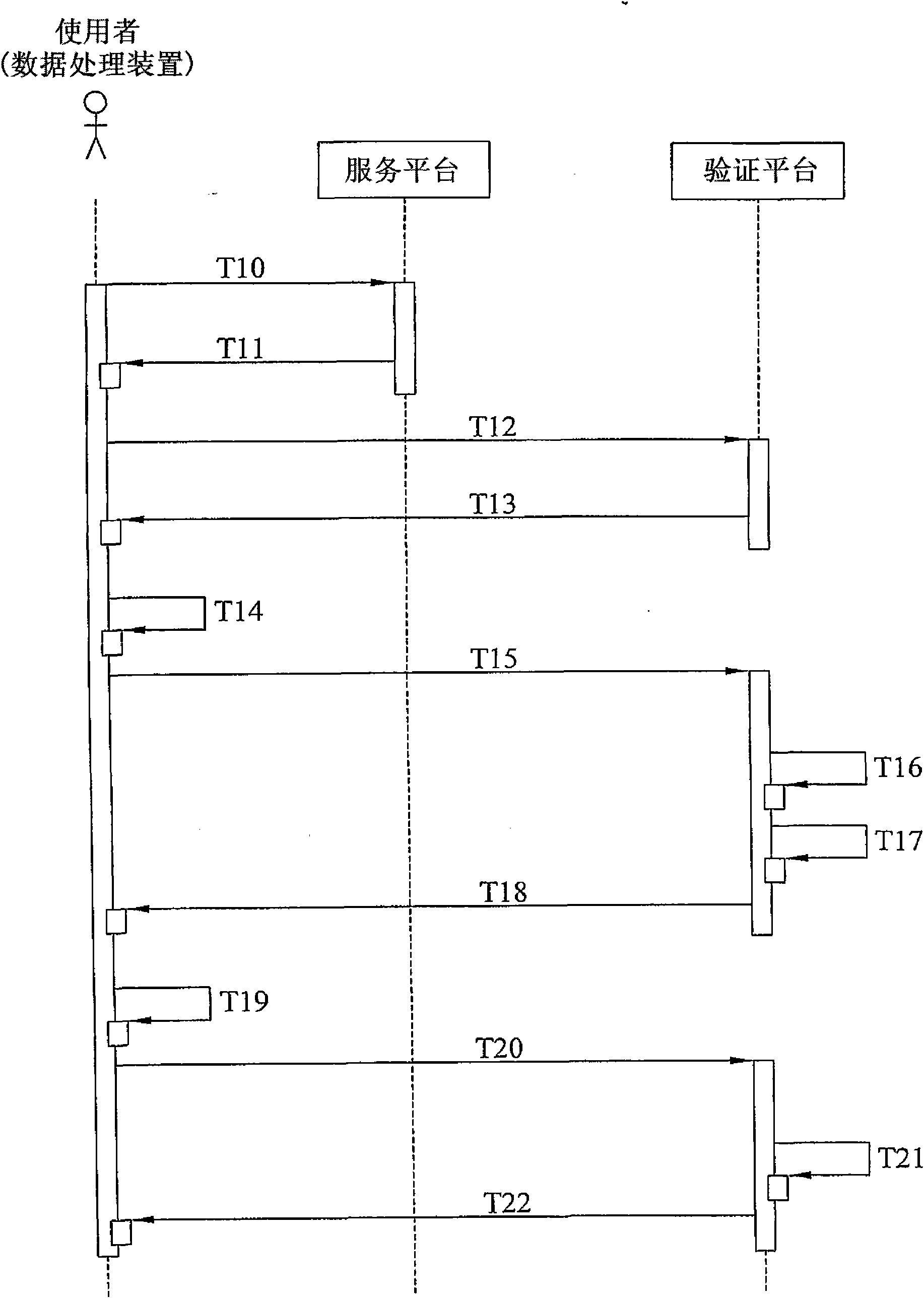
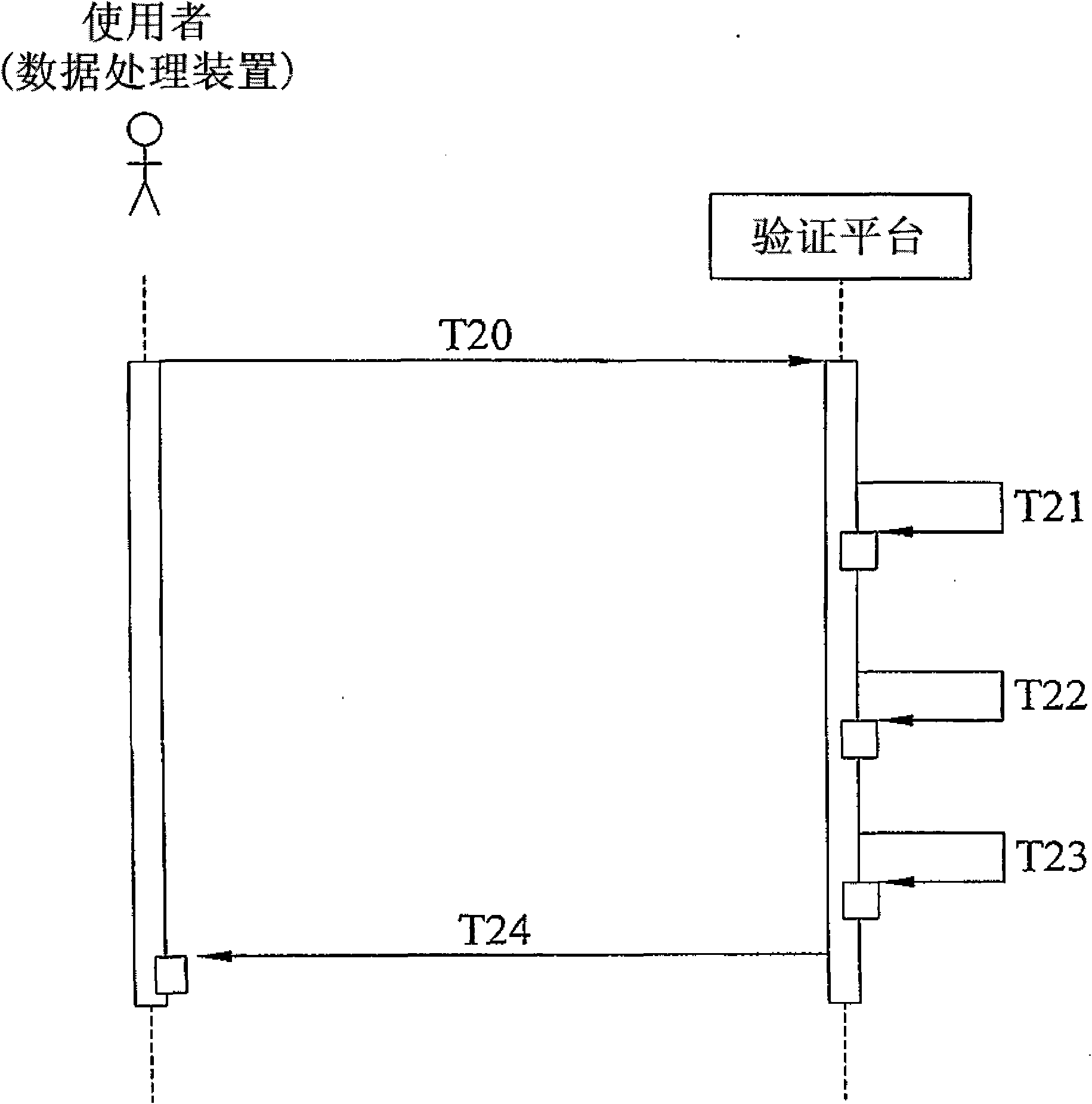
[0019] see figure 1 , depicts a flow chart of the steps of the network user identity authentication method of the present invention. What has been stated earlier here is that the network user identity authentication method of the present invention is for the user to pass through a data processing device (not shown) connected to the service platform (not shown), and to connect to the authentication platform The mobile communication device (not shown) performs a user login operation. In actual application, the service platform can be a server used to provide users with access to or obtain network services such as audio-visual files and applica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com