Crypto chip system for resisting physical invasion and side-channel attack and implementation method thereof
A side-channel attack and cryptographic chip technology, which is applied in the field of cryptographic chip systems against physical intrusion and side-channel attacks, can solve problems such as unsuitable public key cryptography, cryptographic chip security measures that are difficult to meet computing security, and do not provide security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
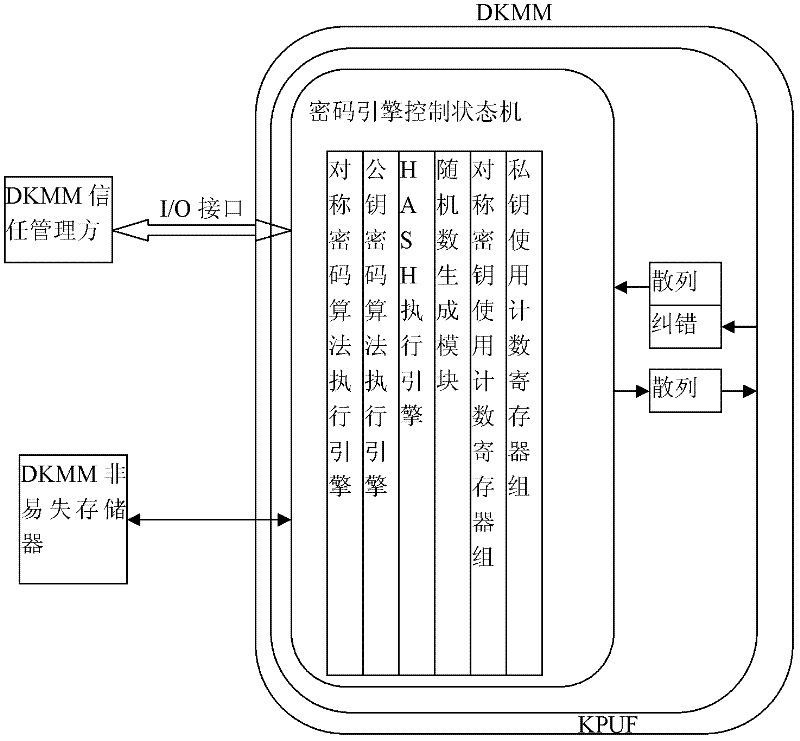
[0095] The cryptographic chip system of this embodiment resisting physical intrusion and bypass attack, such as figure 1 As shown, it includes a dynamic key management module DKMM that limits the number of uses of each key and performs key update management, and also includes
[0096] DKMM non-volatile memory module specially used to save auxiliary information required by DKMM;
[0097] Evaluate the SCA security of DKMM to set the maximum allowable use times of its keys, and the DKMM trust management party to prevent tampering and replay of DKMM non-volatile memory content.
[0098] The DKMM includes a physical unclonable key module KPUF, a symmetric cryptographic algorithm execution engine, a public key cryptographic algorithm execution engine, a HASH execution engine, a random number generation module, a symmetric key use count register group, a private key use count register group, The cryptographic engine controls the state machine, and the sensitive circuits of the KPUF ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com