Method for implementing wireless network safety communication
A technology of secure communication and implementation method, which is applied in the field of computer network security, can solve problems such as network insecurity, and achieve the effects of secure transmission, information transmission security, and cost saving
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In view of the deficiencies in the prior art, the present invention provides a method for realizing wireless network security communication.
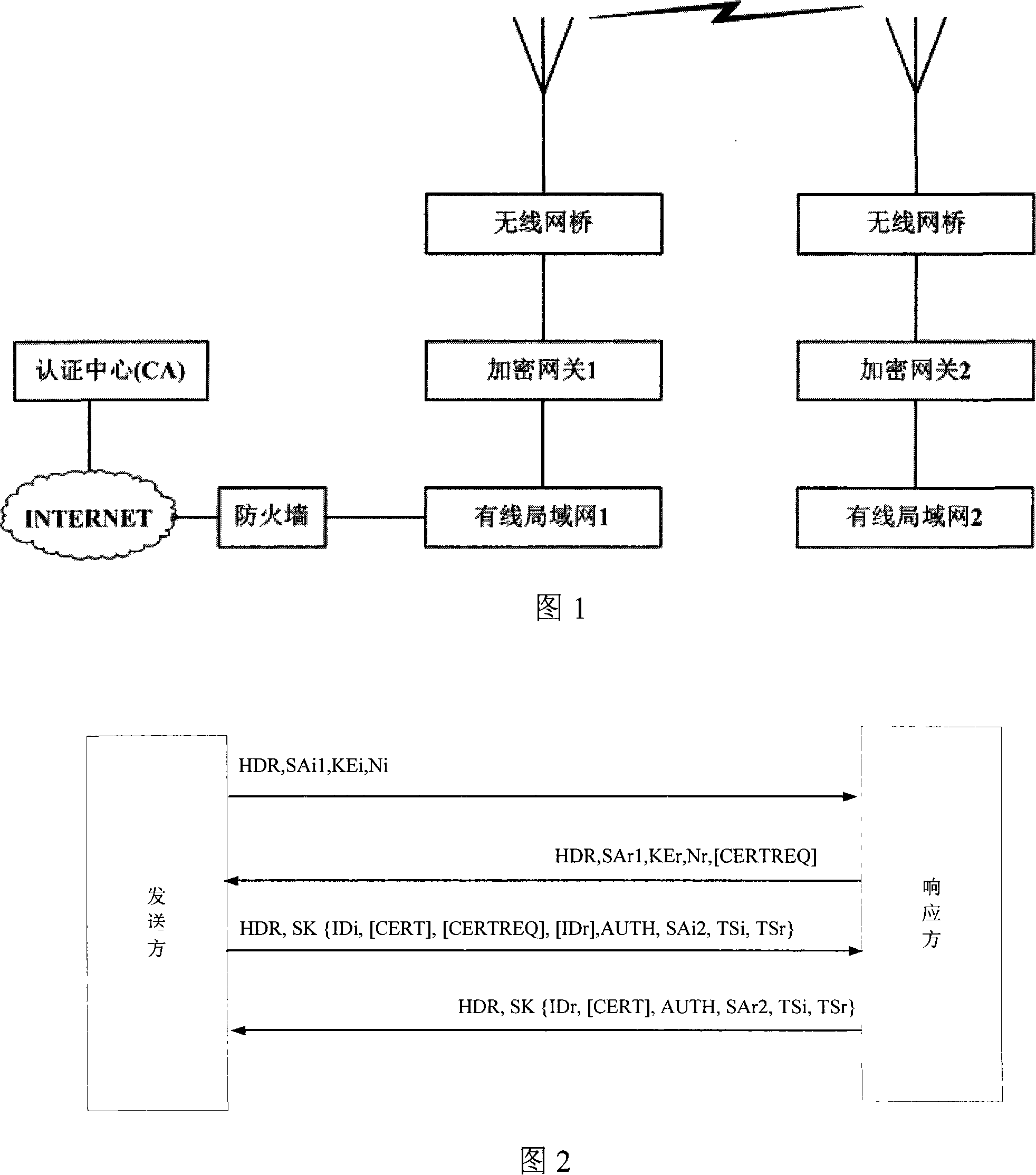
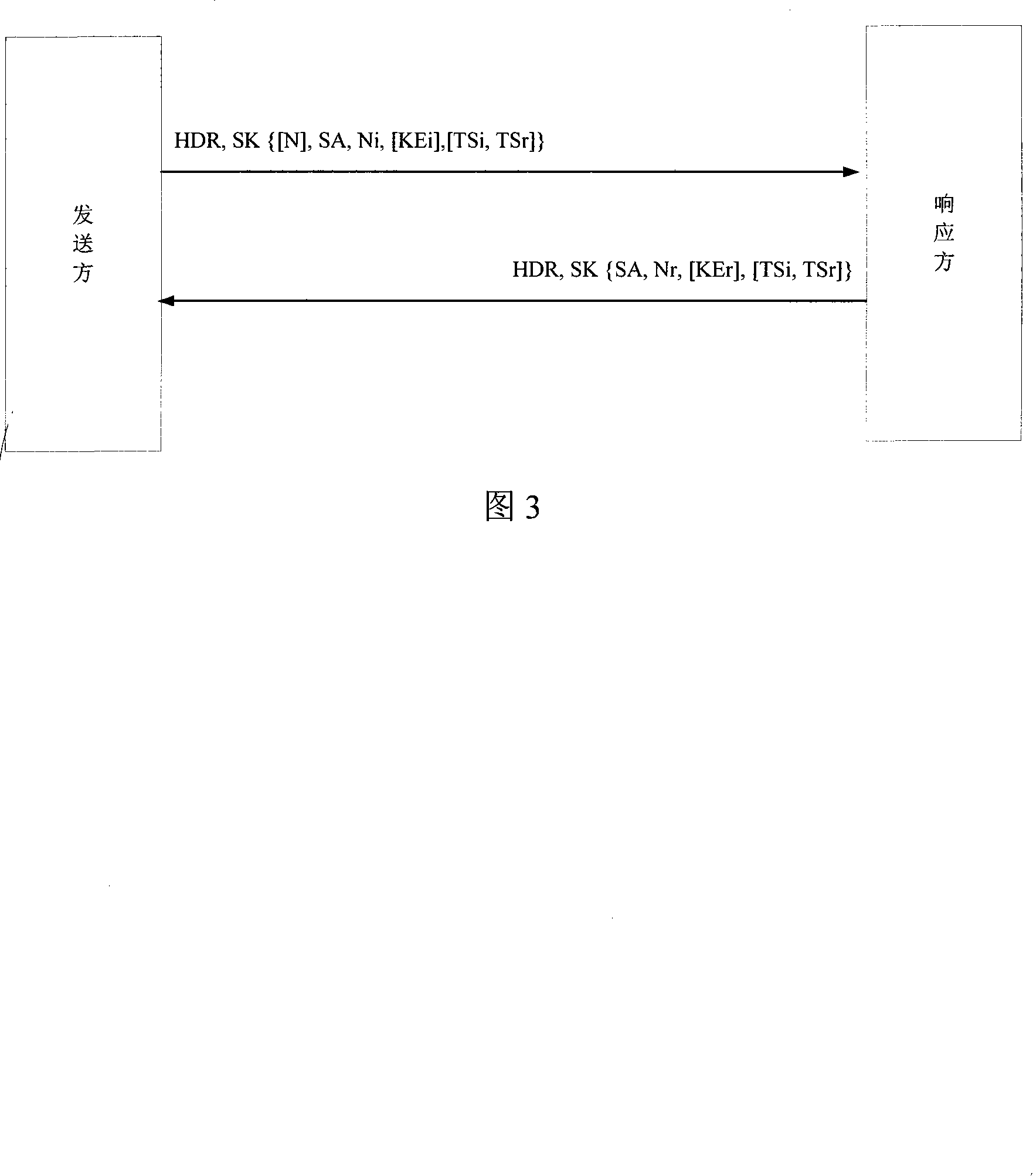
[0036] In Fig. 1, an encryption gateway 1 is added to the wireless bridge and an encryption gateway 2 is added to the wired LAN. The implementation of this method is based on identity authentication and the improvement of the IKEv2 protocol. In this method, the communication entity has two keys (public key and private key). Each communication entity has an undisclosed private key. The sender of the message signs with the private key, and the receiver uses the identity of the sender (that is, the public key). For verification, the communicating entity does not require a certificate authority (CA) to sign the certificate.
[0037] The core of the identity-based authentication method is: the private key is generated by the certification center (CA) according to the public key submitted by the communication entity, and the public key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com