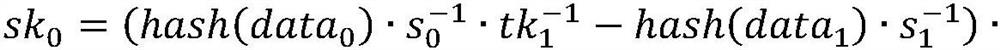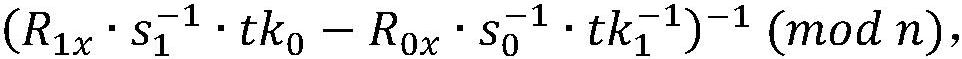Multi-block chain covert communication method
A covert communication and block chain technology, applied in the field of covert communication technology based on multiple block chains, can solve the problems of difficulty in ensuring the concealment of communication, low efficiency, and difficulty in ensuring the security of encrypted currency of both parties in communication, so as to increase the difficulty, The effect of low cost and enhanced concealment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0039] (1) System initialization stage
[0040] 1) Determine the system parameters. E: Elliptic curve whose base point is G, the order of the base point is n; hash function hash; symmetric encryption algorithm (Gen, Enc, Dec), where Gen requires a security parameter as input and outputs a key, Enc(k, m) means to encrypt message m with key k, and Dec(k, c) means to decrypt ciphertext c with key k;
[0041] 2) The two parties negotiate the key. After negotiation, the sender and receiver share the master secret key m , key tk 0 and key tk 1 form a trapdoor key pair (tk 0 , tk 1 ) and address key key add . In addition, the receiver generates a public-private key pair (sk r , pk r ), where the public key pk r Shared with sender.
[0042] (2) Fund preparation stage
[0043] The sender sends two or more transactions in one communication process, and the signature private keys of these transactions are generated according to the method described below. In a blockchain tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com