Industrial internet alarm log association analysis method and system based on graph method
A technology of industrial Internet and correlation analysis, which is applied in the field of correlation analysis of industrial Internet alarm logs based on graph methods, can solve the problems of difficult alarm data analysis and processing, low-risk alarms and false positives, etc., achieve small computing overhead, improve processing efficiency, The effect of low algorithm complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The implementation of the present invention will be described in detail below in conjunction with the accompanying drawings and test data.
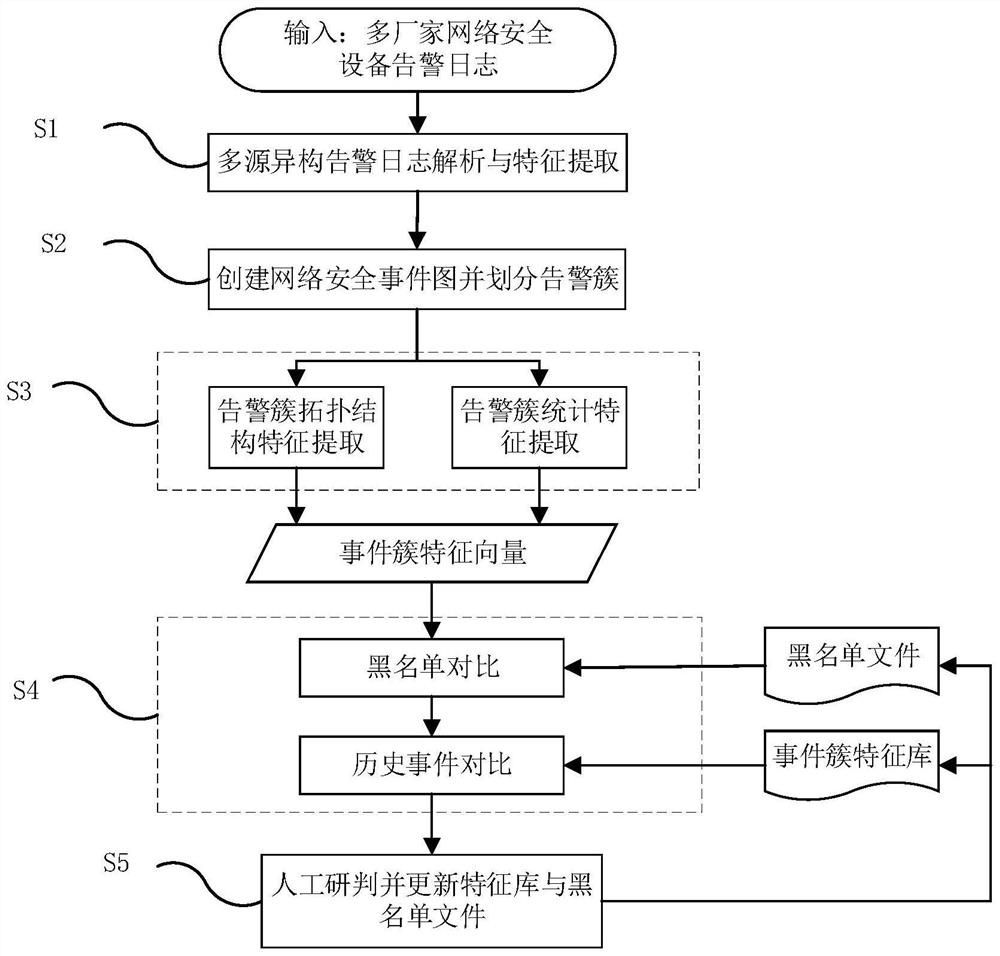
[0047] figure 1It is the overall flow chart of the correlation analysis method of Industrial Internet alarm logs based on the graph method, showing the basic framework of the process of correlation analysis of Industrial Internet multi-source heterogeneous network security alarm logs, where the input test data is excerpted from a power company network security alarm A small amount of alarm log data in the log database, the source IP address and destination IP address have been desensitized; the test alarm log data is deployed by the DP IPS deployed at the exit of the company's network, the Shengbang WAF deployed in the server area, and the deployed Produced in the sky eye system in the terminal area, it meets the requirements of multi-source and heterogeneity.
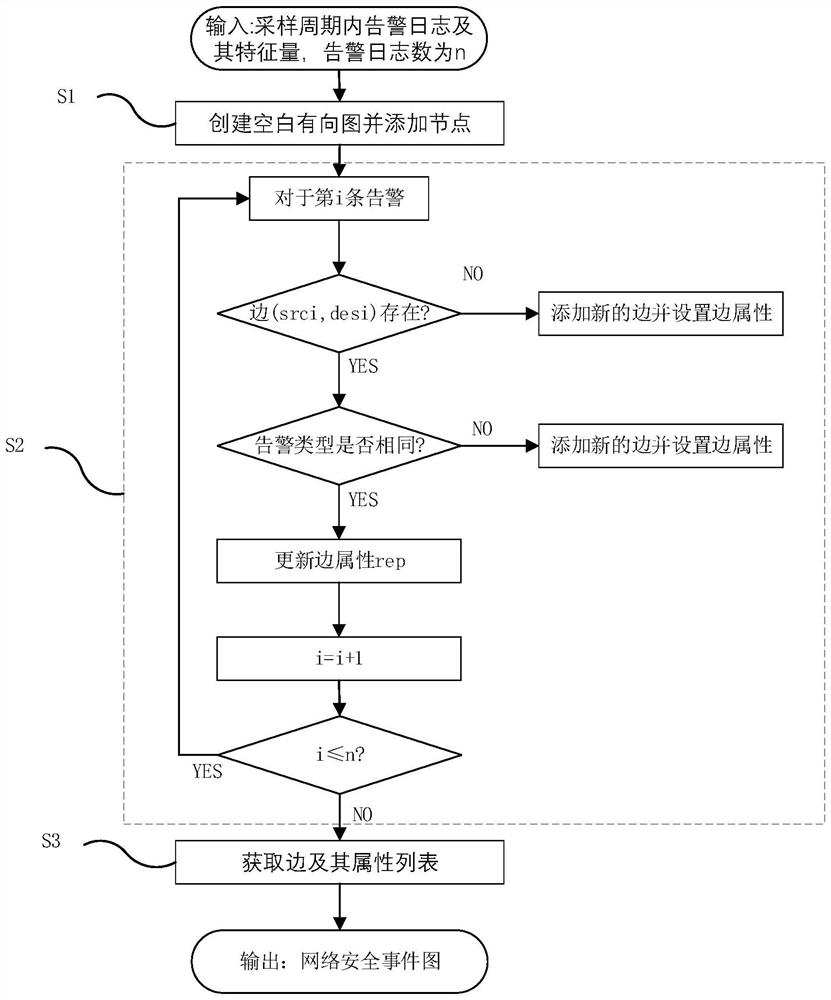
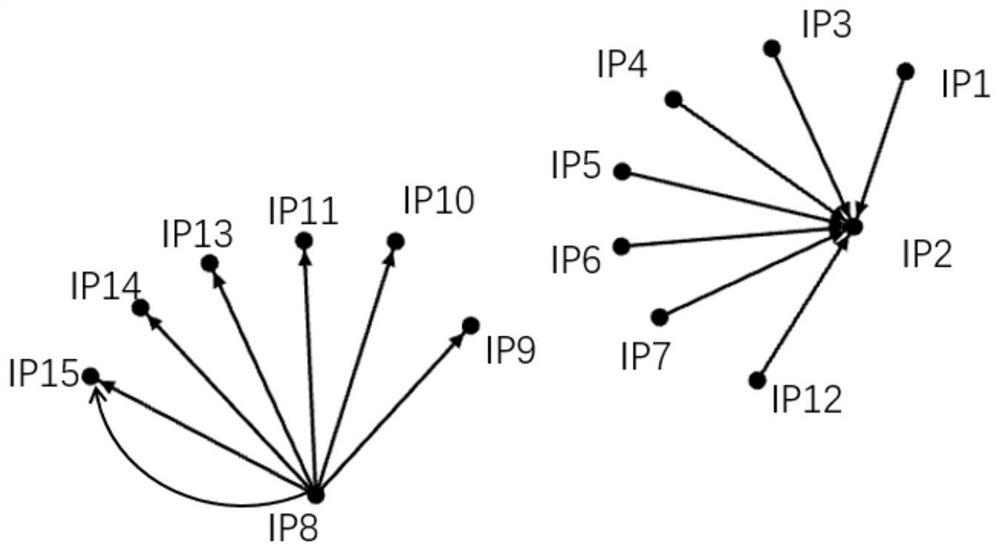
[0048] A kind of graph method-based industrial Internet alarm log ass...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com