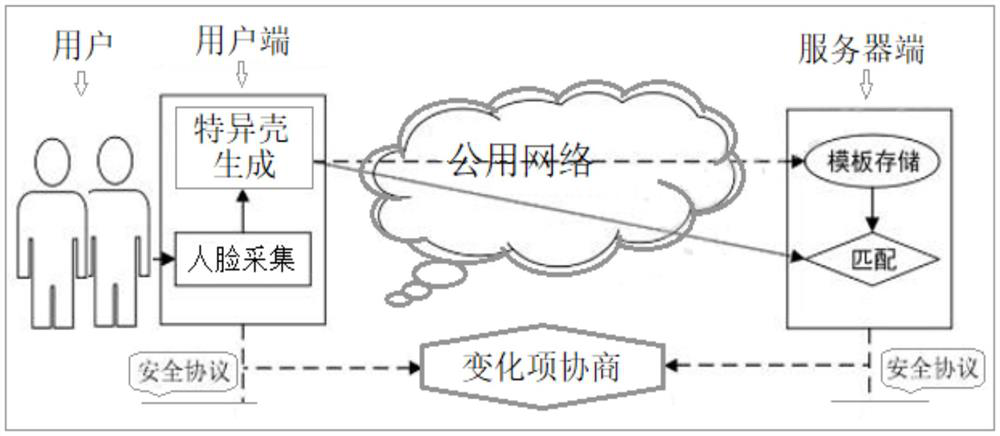
Face feature collaborative protection safety certification system under public network
A security authentication and facial feature technology, applied in the field of facial feature collaborative protection security authentication system, can solve problems such as poor accuracy and practicability, low facial feature matching query efficiency, stolen feature data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0110] The technical solution of the face feature cooperative protection security authentication system under the public network provided by this application will be further described below in conjunction with the accompanying drawings, so that those skilled in the art can better understand this application and implement it.
[0111]With the rapid development of mobile public networks, the performance of smart terminal equipment is getting stronger and stronger. Smartphone manufacturers have adopted face recognition as a standard configuration of mobile phones. Various financial payment platforms have begun to support research on identity authentication technologies such as face and iris, and biometric authentication. Technology is widely accepted and used. Biometrics have the characteristics of lifelong binding and stability with biological individuals. Biometric authentication technology is widely used in security authentication protocols. However, the uniqueness of the origi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com