Malicious software detection method and system based on memristor neural network
A malware and neural network technology, applied in the field of information security, can solve problems such as data transmission bandwidth bottlenecks, and achieve the effect of improving generalization ability, expanding storage space, and improving recognition accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
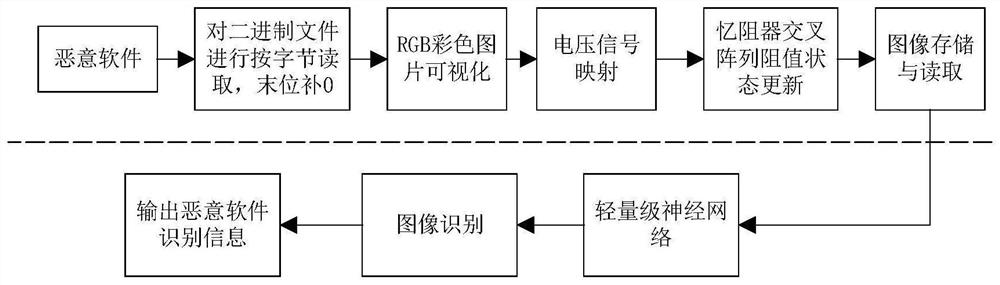
[0025] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
[0026] In recent years, neuromorphic computing chips based on new electronic synaptic devices have become a research hotspot. By adjusting the current applied to the memristor, the pulse length and amplitude of the voltage, the resistance value of the memristor can be changed. Due to the mobility of ions, it is possible to simulate neural networks based on memristors. The use of memristors to construct spiking neural networks has the following advantages: (1) continuous update of synaptic weights can be achieved; (2) nanoscale memristors can realize ultra-high-density integrated networks; (3) the network has learning and memory (4) The memristor is a passive device and the non-volatility of information after power fa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com