Vulnerability fingerprint silent analysis monitoring method, system, device and medium
A vulnerability and fingerprint technology, applied in the field of software development, can solve the problems of incapable of intelligent scanning analysis, incapable of intelligent scanning, time-consuming and labor-intensive, etc., to improve the level of network security protection, standardize network security behavior, and reduce internal loopholes Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
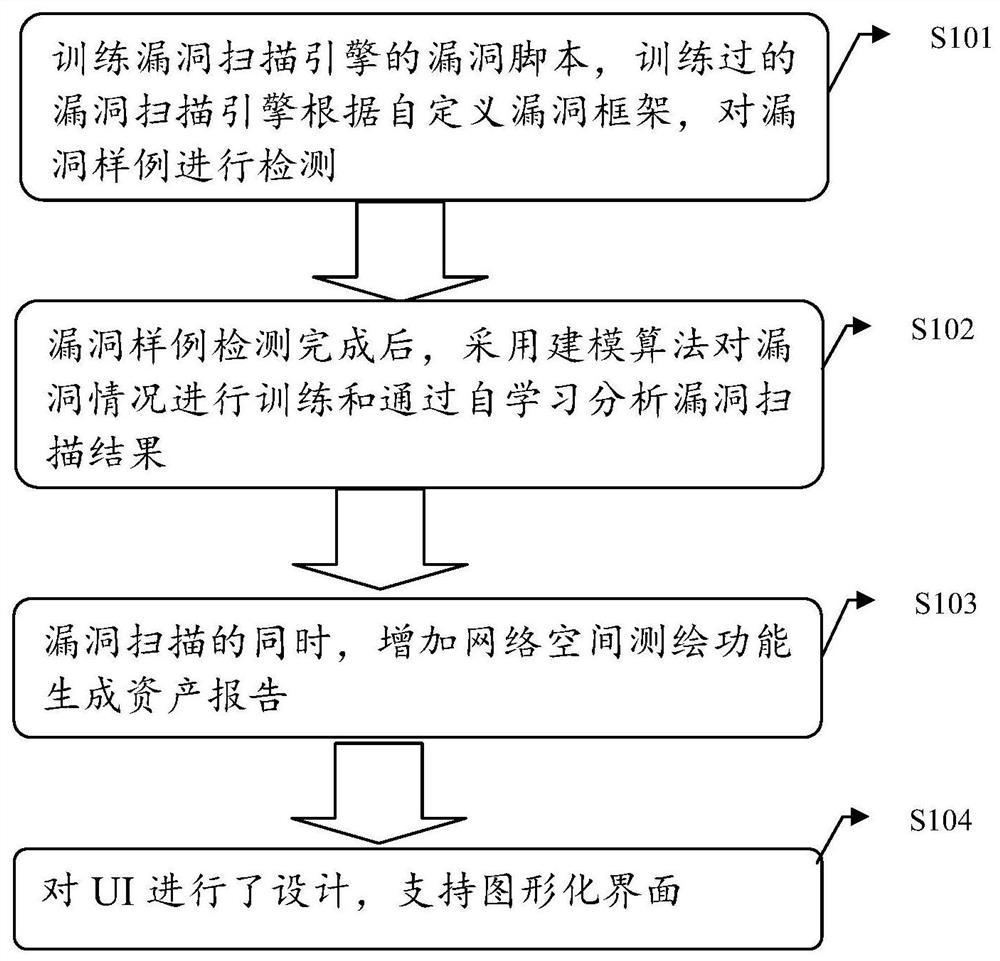
[0040] Embodiment 1 of the present invention proposes a method for silent analysis and monitoring of vulnerability fingerprints, which is dedicated to reducing internal vulnerabilities, standardizing network security behaviors, discovering and handling existing security risks in advance, greatly improving the company's network security protection level, and timely discovering equipment and The attack risk faced by the system. Such as figure 1 It is a flow chart of a method for silent analysis and monitoring of vulnerability fingerprints proposed in Embodiment 1 of the present invention;
[0041] In step S101, the vulnerability script of the vulnerability scanning engine is trained, and the trained vulnerability scanning engine detects the vulnerability samples according to the custom vulnerability framework.
[0042] The invention adopts a vulnerability scanning engine to accurately scan operating system vulnerabilities, application system framework vulnerabilities and common...
Embodiment 2
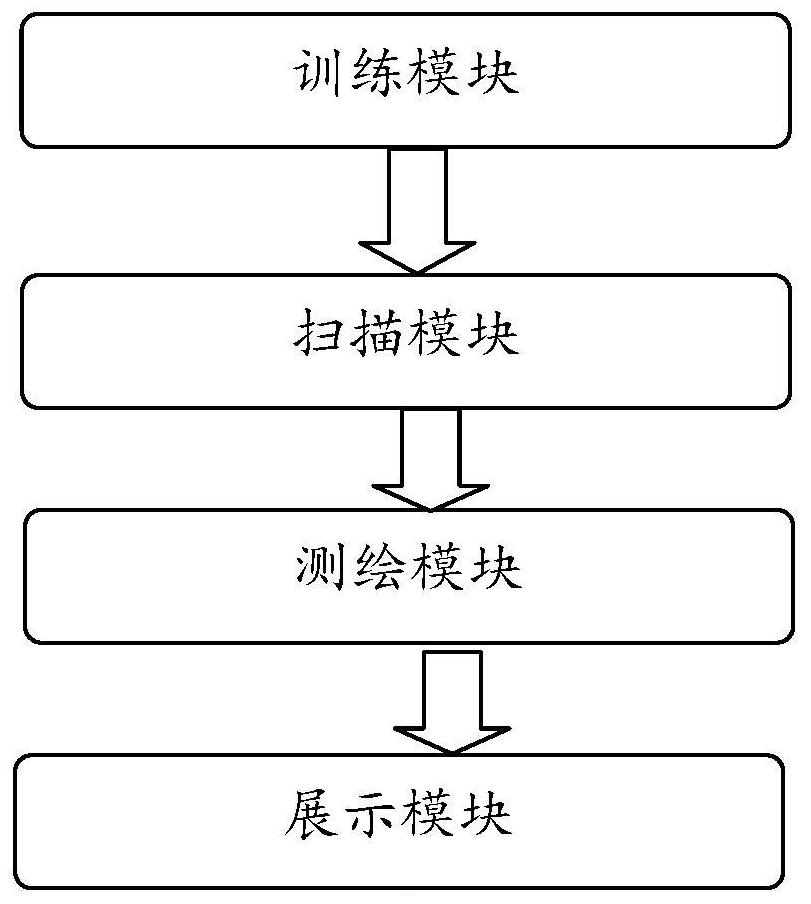
[0066] Based on the method for silent analysis and monitoring of vulnerability fingerprints proposed in Embodiment 1 of the present invention, Embodiment 2 of the present invention also proposes a system for silent analysis and monitoring of vulnerability fingerprints. The system includes: a training module, a scanning module and a surveying and mapping module;
[0067] The training module is used to train the vulnerability script of the vulnerability scanning engine, and the trained vulnerability scanning engine detects the vulnerability samples according to the custom vulnerability framework;
[0068] The scanning module is used to train the vulnerability situation by using the modeling algorithm and analyze the vulnerability scanning results through self-learning after the vulnerability sample detection is completed;
[0069] While the surveying and mapping module is used for vulnerability scanning, cyberspace surveying and mapping functions are added to generate asset repor...
Embodiment 3
[0090] The invention also proposes a device comprising:
[0091] memory for storing computer programs;
[0092] When the processor is used to execute the computer program, the method steps are as follows:
[0093] Such as figure 1 It is a flow chart of a method for silent analysis and monitoring of vulnerability fingerprints proposed in Embodiment 1 of the present invention;
[0094] In step S101, the vulnerability script of the vulnerability scanning engine is trained, and the trained vulnerability scanning engine detects the vulnerability samples according to the custom vulnerability framework.
[0095] The invention adopts a vulnerability scanning engine to accurately scan operating system vulnerabilities, application system framework vulnerabilities and common middleware vulnerabilities such as weblogic and tomcat.
[0096] In order to ensure the accuracy of the vulnerability scripts, each script has undergone targeted training no less than 3 times, and has been optimiz...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com