Web attack detection method based on HTTP (Hyper Text Transport Protocol) request text and related equipment
An attack detection and text technology, applied in the field of network security, can solve the problems affecting the accuracy rate and true positive rate of the model, the accuracy rate and true positive rate are not high, and the focus processing ability is not strong, so as to avoid missing attack payloads and improve Accuracy rate and true positive rate, the effect of improving information memory ability and focus analysis ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
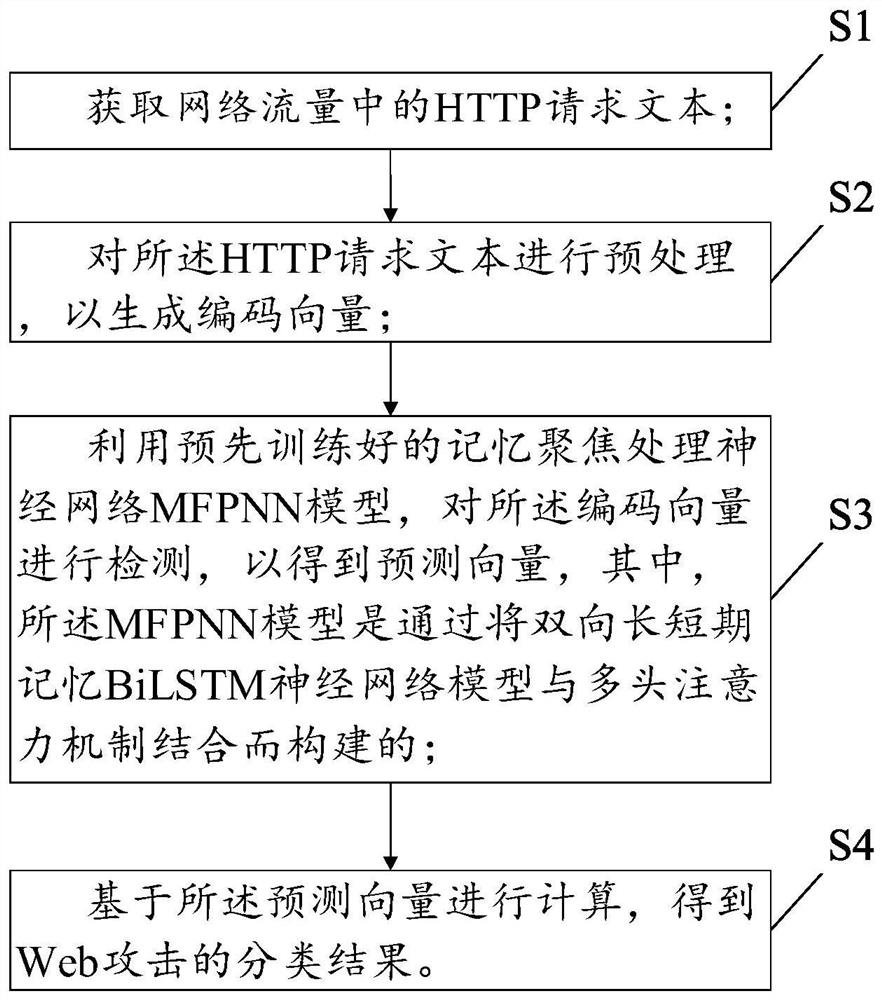
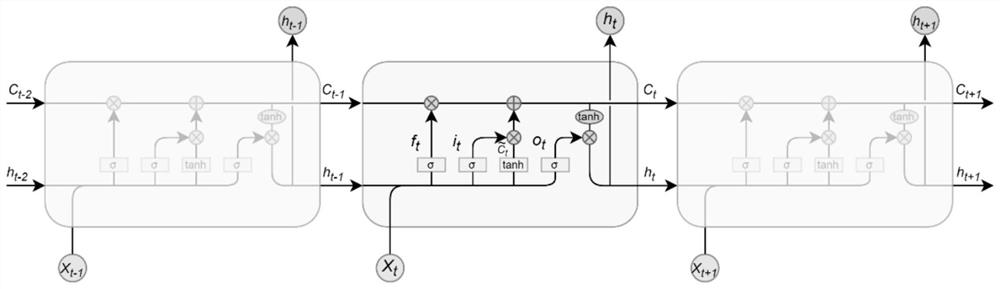
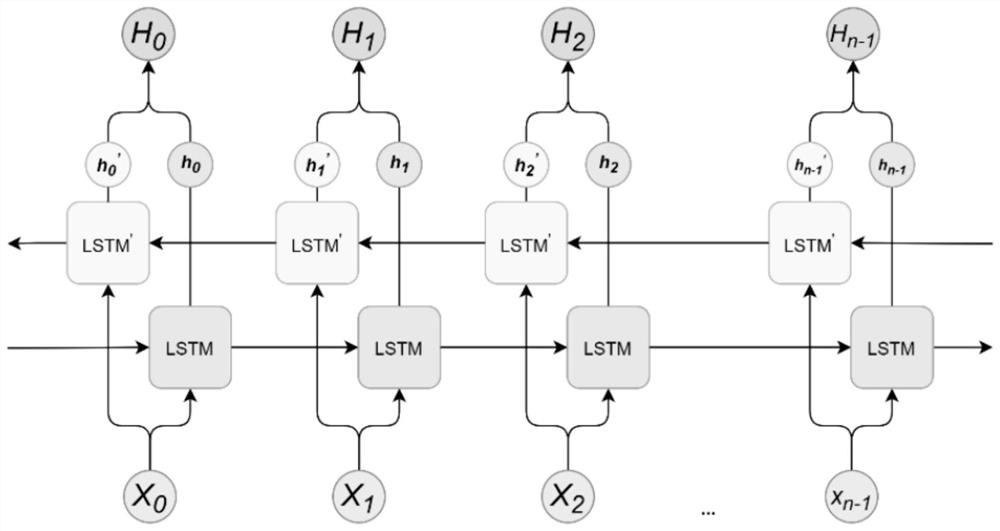
[0028] In order to make the purpose, technical solutions and advantages of the present disclosure clearer, the present disclosure is optionally described in detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
[0029] It should be noted that, unless otherwise defined, the technical terms or scientific terms used in the embodiments of the present disclosure shall have ordinary meanings understood by those skilled in the art to which the present disclosure belongs. The words "comprising" or "comprising" and other similar words used in the embodiments of the present disclosure mean that the elements or objects appearing before the word cover the elements or objects listed after the word and their equivalents, without excluding other elements or objects . Words such as "connected" or "connected" are not limited to physical or mechanical connections, but may include electrical connections, whether direct or indirect.
[0030] With...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com