Method and system for preventing phone fraud based on end-side network cloud collaboration
A technology of telephone and network cloud, applied in telephone communication, electrical components, automatic switching office, etc., can solve the problems such as the need to improve the recognition efficiency and accuracy, the inaction of the perpetrators of telephone fraud, and the increase of terminal complexity and cost, etc. Achieve the effect of reducing the number and transmission path length, ensuring reliability, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
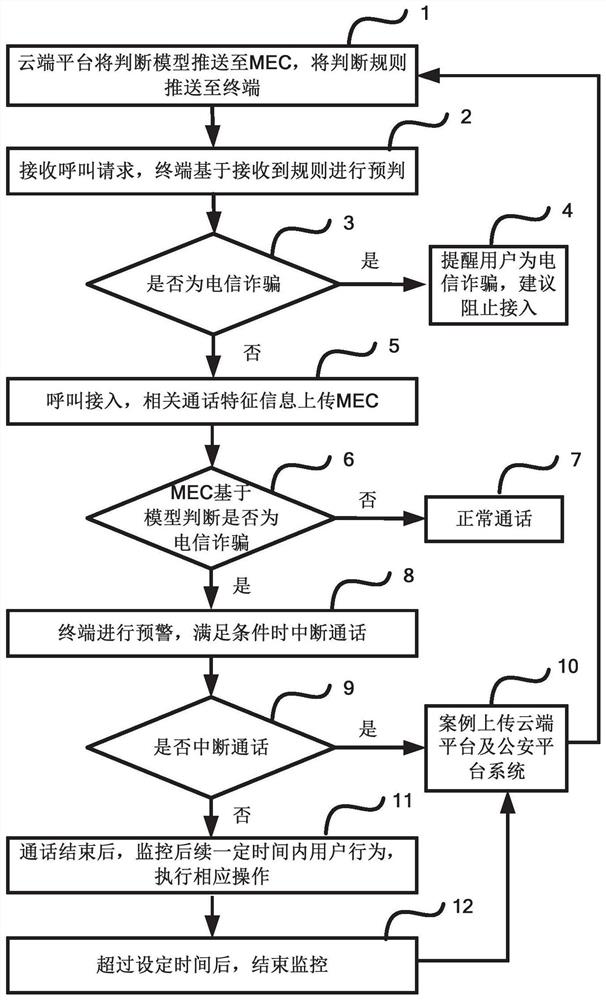
[0051] 5G mobile communication technology not only considers meeting the communication needs between people, but also meets the communication needs between people and things, and things and things. Therefore, network slicing is introduced. Network slicing is to divide a physical network into multiple end-to-end through virtualization. Logical network, each virtual network corresponds to different application scenarios. At present, there are mainly three types of slices: eMBB (enhanced mobile broadband), mMTC (massive machine connection) and uRLLC (ultra-high reliability, low latency). Slicing can provide mS-level delay and 99.999% reliability. On the other hand, through logical isolation, network transmission is safer. In addition, edge computing (MEC) technology, which evolved from traditional cloud computing technology, sinks strong computing resources and efficient services to the edge of the network, thereby having lower latency, lower Energy efficiency and better privacy...
Embodiment 2
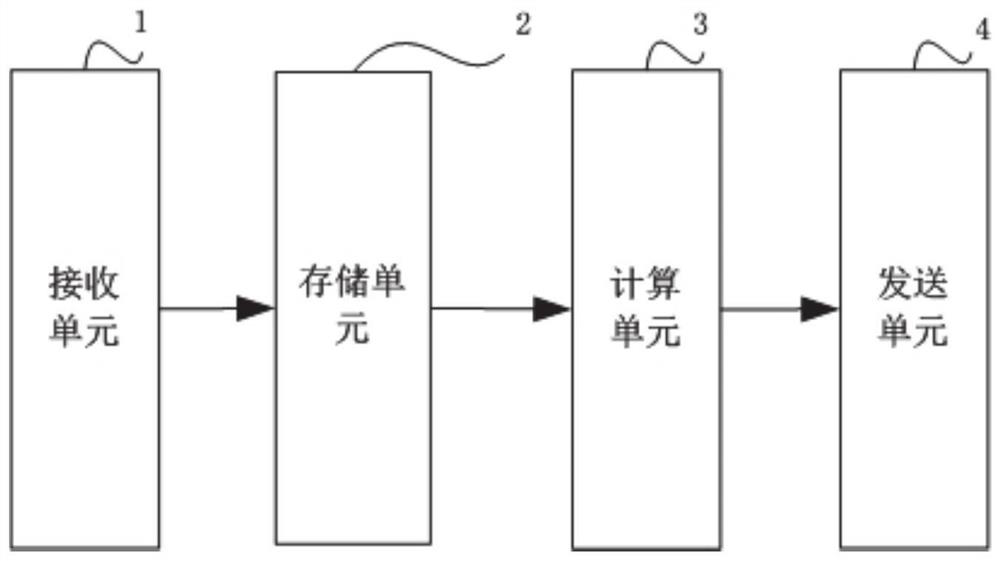
[0071] Such as figure 2 As shown, this embodiment provides a multi-access edge computing platform, including:
[0072] The first receiving unit is configured to receive call characteristic information sent by the terminal, and the call characteristic information is sent after the terminal performs a preliminary diagnosis on the caller number and sensitive words;
[0073] The second receiving unit is configured to receive the telephone fraud identification model sent by the cloud, and the telephone fraud identification model is constructed and trained by the cloud based on the training samples;
[0074] The decision-making unit is configured to judge the call characteristic information based on the telephone fraud identification model;
[0075] The sending unit is configured to send alarm information to the terminal according to the judgment result, and upload the call feature information and the judgment result to the cloud, so that the cloud can update the training samples ...
Embodiment 3
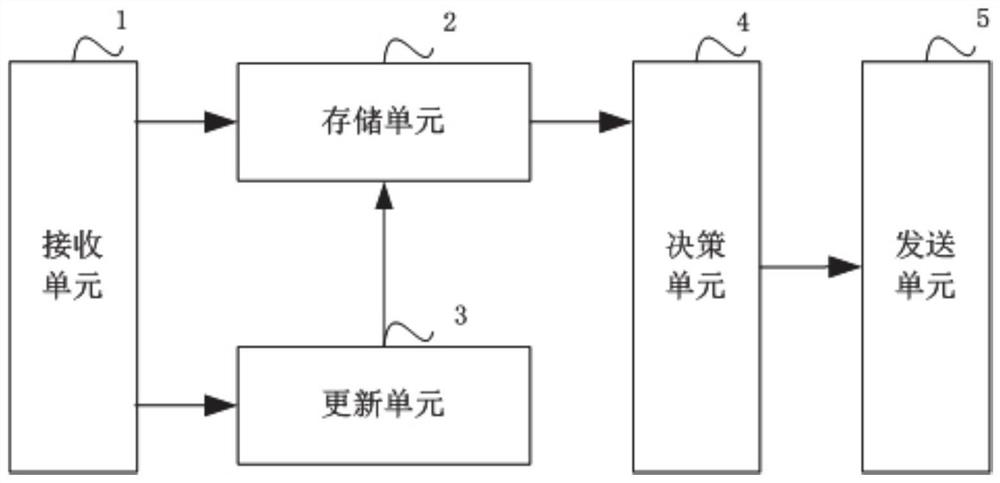
[0079] Such as image 3 As shown, the present embodiment provides a cloud platform, including:
[0080] The computing unit is configured to construct and train a telephone fraud recognition model and preliminary diagnosis and recognition rules based on training samples;
[0081] The sending unit is configured to send the phone fraud recognition model to the multi-access edge computing platform, and send the preliminary diagnosis and recognition rules to the terminal;
[0082] The receiving unit is configured to receive the call characteristic information and the judgment result uploaded by the multi-access edge computing platform.
[0083] In this embodiment, the cloud platform further includes a storage unit configured to store the telephone fraud information uploaded by the multi-access edge computing platform.
[0084] In this embodiment, the cloud platform further includes an update unit configured to update the training samples according to the phone fraud information u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com