Image encryption method and device based on novel two-dimensional composite chaotic mapping and SHA-256
A SHA-256, chaotic mapping technology, applied in image data processing, image data processing, computer security devices, etc., can solve the problems of encryption security and low execution cost, improve the ability to resist differential attacks, and reduce execution costs , the effect of reducing dependence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
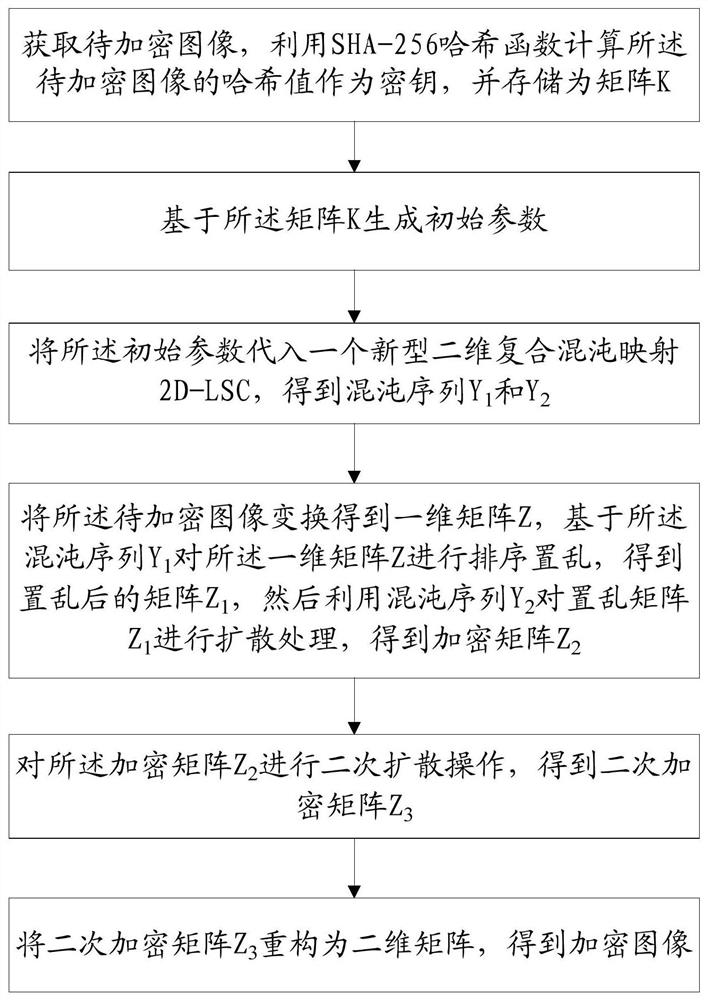
[0069] This embodiment provides an image encryption method based on a novel two-dimensional composite chaotic map and SHA-256, such as figure 1 shown, including:
[0070] Step 10, obtain the image to be encrypted, use the SHA-256 hash function to calculate the hash value of the image to be encrypted as a key, and store it as a matrix K;
[0071] Step 20, generating initial parameters based on the matrix K;
[0072] Step 30. Substituting the initial parameters into a new two-dimensional composite chaotic map 2D-LSC to obtain the chaotic sequence Y 1 and Y 2 , the novel two-dimensional composite chaotic map 2D-LSC combines the output of the Logistic map and the Sine map with a change constant, and then performs a cosine transform to generate an output;
[0073] Step 40, transforming the image to be encrypted to obtain a one-dimensional matrix Z, based on the chaotic sequence Y 1 Sorting and scrambling the one-dimensional matrix Z to obtain a scrambled matrix Z 1 , and then ...
Embodiment 2
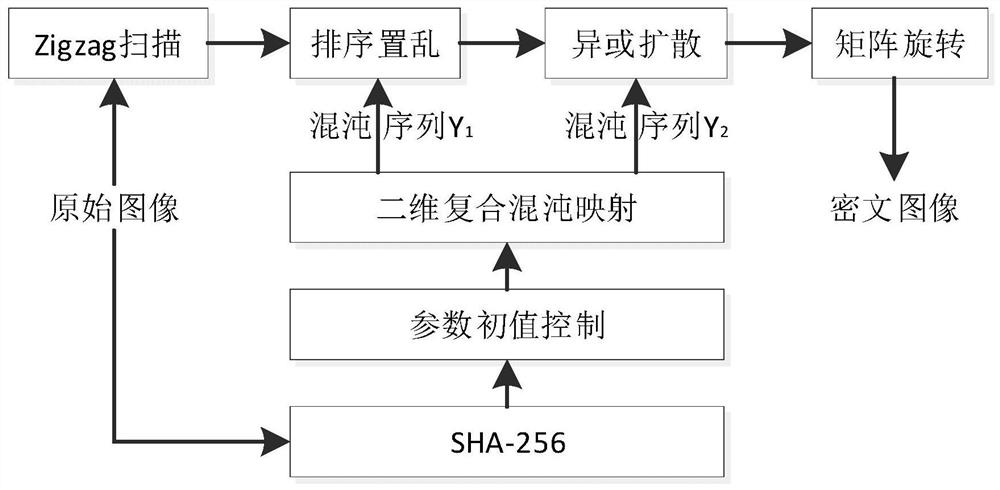
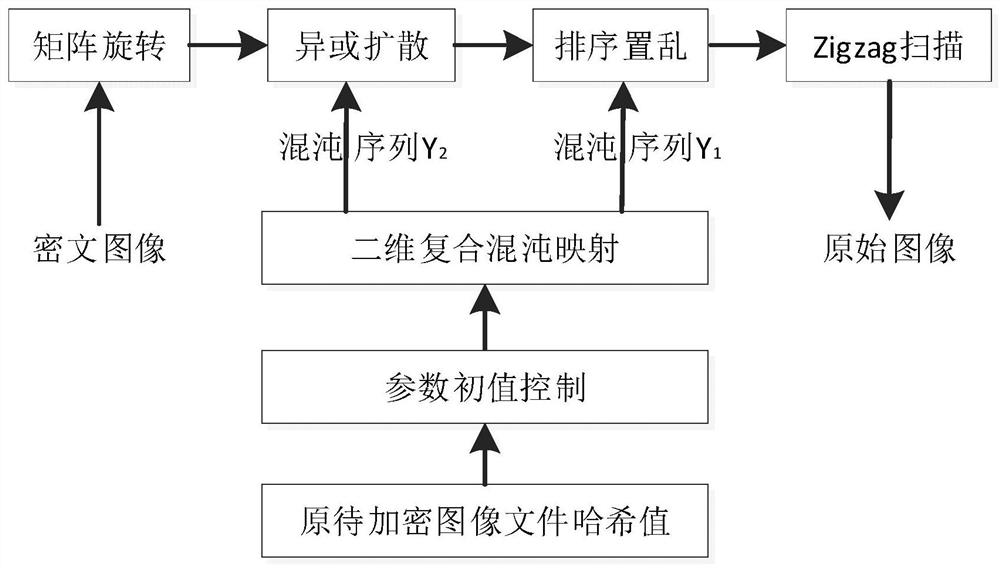
[0097] Please refer to Figure 2 to Figure 7 , a specific embodiment of the present invention is realized as follows:
[0098] S10, read the image file to be encrypted (such as Figure 5 shown), use the SHA-256 hash function to calculate the hash value of the image file as the system key, and store it as a matrix K, and the matrix K is 826cc80fc06a1b09554fb559c353610744a47837fc41e63659ae8a9bc177caff;
[0099] The initial parameters of the two-dimensional composite chaotic map (2D-LSC) and other parameters of the algorithm can then be calculated based on said matrix K.
[0100] S20. Calculate the initial parameters of the iteration of the two-dimensional compound chaotic system and other parameters of the algorithm based on the matrix K, specifically as follows:
[0101] Based on the first twenty sub-blocks of the matrix K [k 1 ,k 2 ,...,k 20 ], calculate the control parameters α, β and γ of 2D-LSC according to the following formula, and the iterative initial value x 1 wi...
Embodiment 3
[0120] In this embodiment, an image encryption device based on a novel two-dimensional composite chaotic map and SHA-256 is provided, such as Figure 8As shown, it includes: key generation module, initial parameter generation module, chaotic sequence generation module, scrambling diffusion module, secondary diffusion module and reconstruction module;
[0121] The key generation module is used to obtain the image to be encrypted, and use the SHA-256 hash function to calculate the hash value of the image to be encrypted as a key, and store it as a matrix K;
[0122] The initial parameter generating module is configured to generate initial parameters based on the matrix K;
[0123] The chaotic sequence generation module is used to substitute the initial parameters into a new two-dimensional composite chaotic map 2D-LSC to obtain the chaotic sequence Y 1 and Y 2 , the novel two-dimensional composite chaotic map 2D-LSC combines the output of the Logistic map and the Sine map with...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com