Computer information security monitoring system
An information security and monitoring system technology, applied in computing, hardware monitoring, instruments, etc., can solve problems such as potential safety hazards, achieve the effects of reducing necessity, ensuring reliability, and preventing illegal personnel from evading authentication and identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
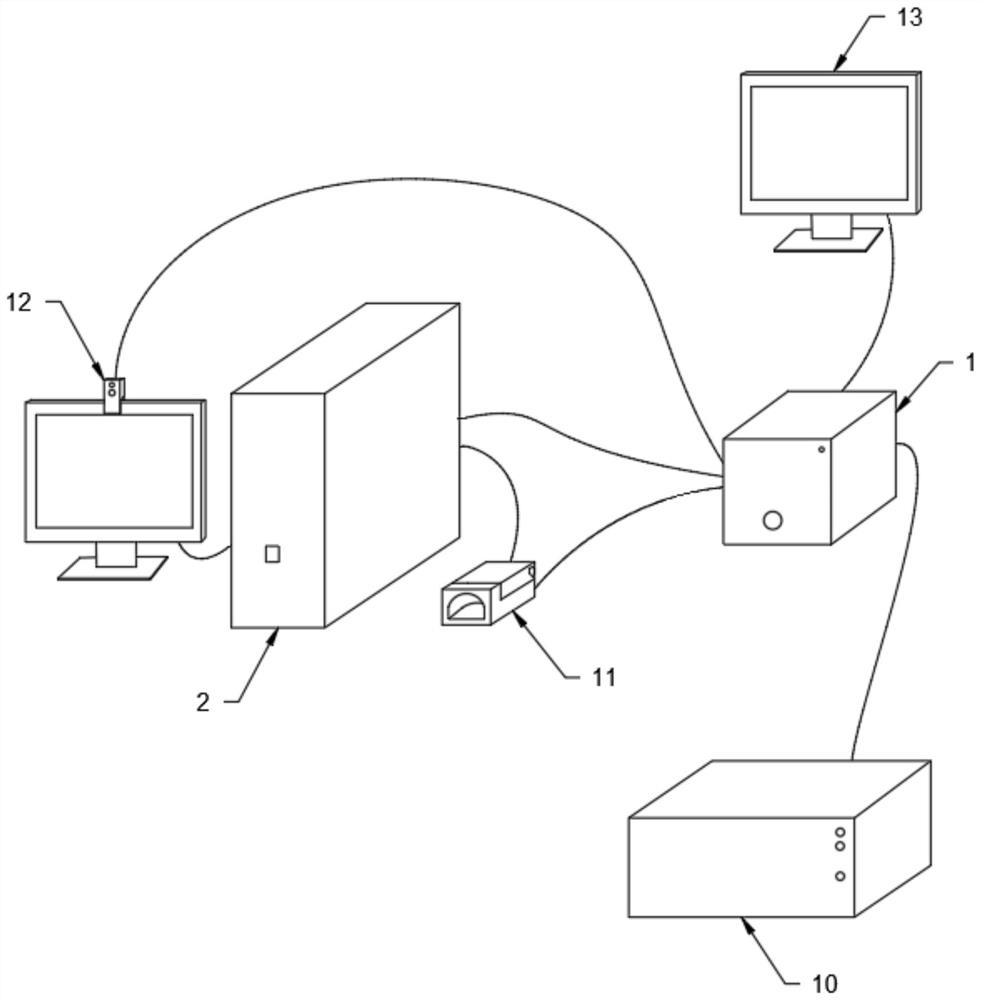
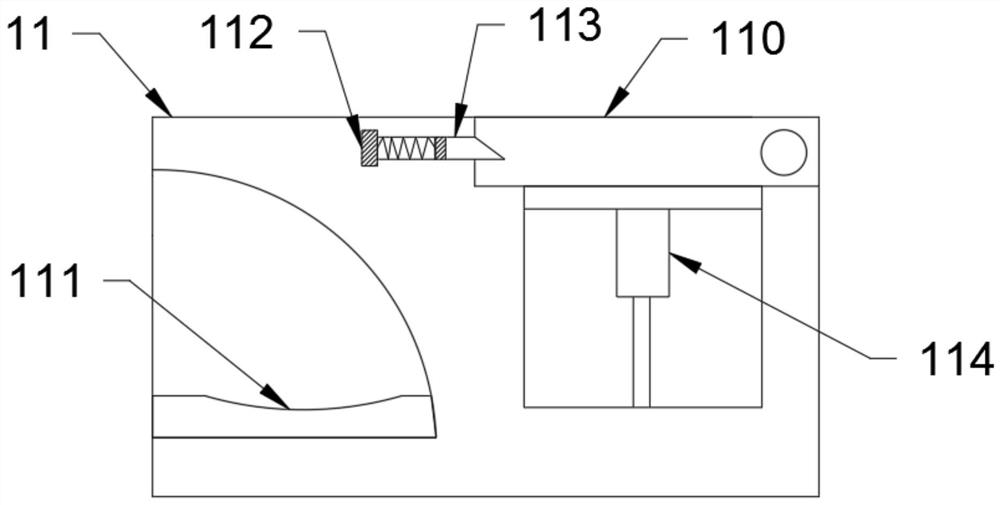
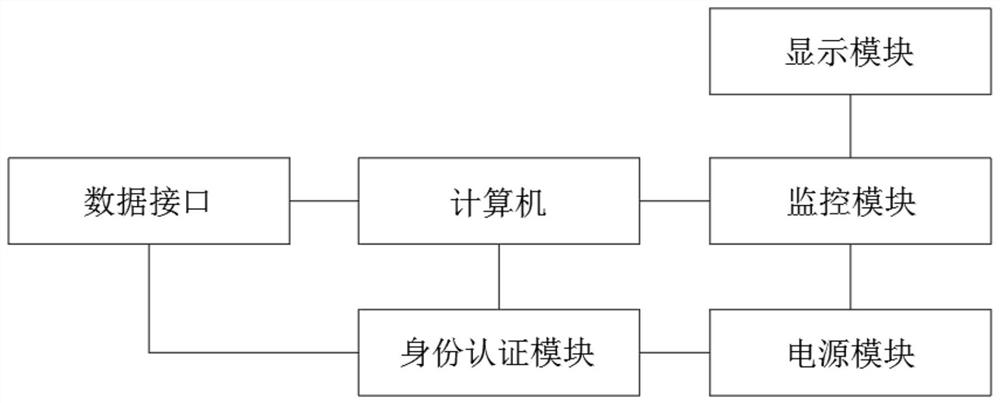
[0024] Such as Figure 1 to Figure 6 As shown, the present invention discloses a computer information security monitoring system, adopting a technical solution comprising a monitoring module 1, a computer 2, a power supply module 10, a display module 13, and an identity authentication module, the monitoring module 1 and the computer 2. The power supply module 10, the display module 13, and the identity authentication module are electrically connected, and the monitoring module 1 is provided with a safety monitoring unit, an operation monitoring unit, a log storage unit, and an alarm unit, which can monitor the The computer 2 carries out overall monitoring, and saves the monitoring log, is convenient to find the cause when a problem occurs, and also performs an alarm operation for abnormal operation, which improves the safety of the entire system. The stability of the system operation in the case of a mains power failure, the identity authentication module also includes a finge...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com