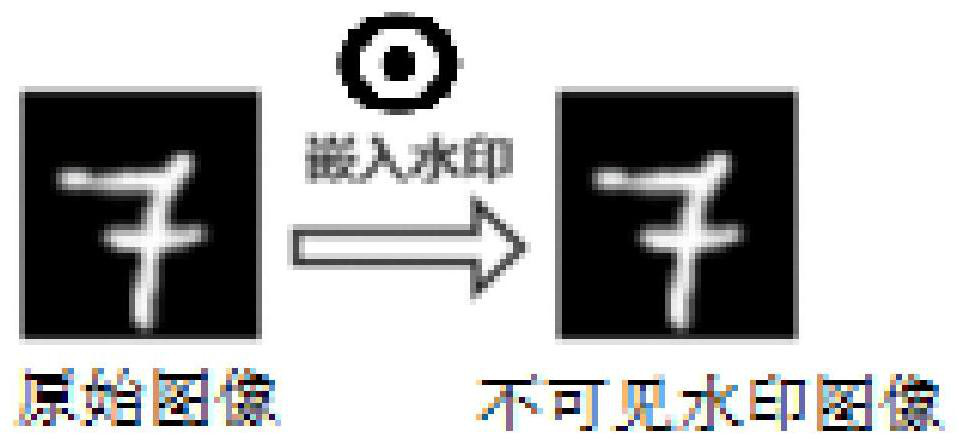
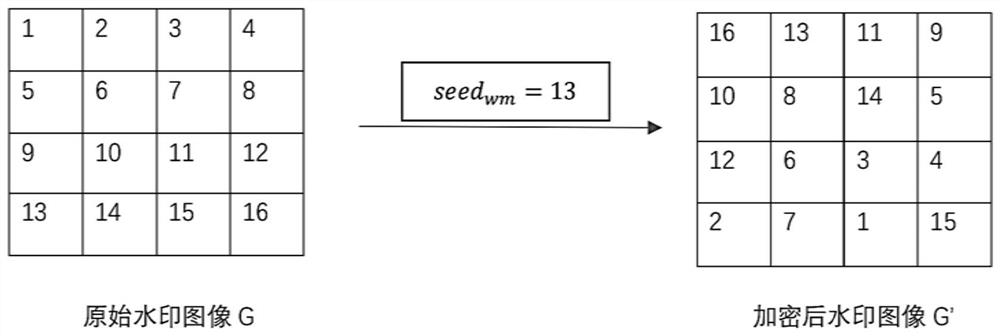
Invisible watermark image construction and classification methods, invisible watermark backdoor attack model construction and classification methods and system
A technology of watermarking images and construction methods, which is applied in image watermarking, image data processing, image data processing and other directions, can solve the problems of poor concealment and easy detection of backdoor triggers, and achieve high classification accuracy, imperceptibility, and perfect recognition. effect of technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0055] This embodiment provides a method for constructing an invisible watermark image, and the detailed steps are as follows:
[0056] Step 1, get original image and watermark image;
[0057] Step 2, performing Haar discrete wavelet transformation on the original image to obtain the low-frequency information matrix Y and the horizontal high-frequency information matrix U of the original image 1 , vertical high-frequency information matrix U 2 and the diagonal high-frequency information matrix U 3 ; Specifically, the first-level Haar discrete wavelet transformation is performed;
[0058] Step 3, perform discrete cosine changes on the blocks of the low-frequency information matrix Y described in step 2 to obtain multiple low-frequency information matrices, specifically determine the number of blocks according to the size of the selected watermark image, and the number of blocks is greater than the size of the watermark image , the size of the watermark image used in this emb...
Embodiment 2
[0070] On the basis of Embodiment 1, this embodiment provides a method for constructing a neural network backdoor attack model of an invisible watermark, including the following steps:
[0071] Step 1, obtain the original image data set M and the invisible watermark image data set M';
[0072] Raw image dataset M{M1,...,Mi,...Mn}, M i Represents the i-th original image in the original image data set M, n represents the number of original images, which is a positive integer;
[0073] The original image data set M uses the mnist data set. The mnist data set is organized by the National Institute of Standards and Technology (NIST) and consists of 250 numbers handwritten by different people, of which 50% They are high school students, 50% are from Census Bureau staff, and all samples in the database are grayscale images of 28×28 pixels. Contains 60,000 training images and 10,000 test images, divided into ten categories of 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, such as Figure 4 As shown...
Embodiment 3
[0095] On the basis of embodiments 1 and 2, this embodiment provides a kind of image classification method, including:
[0096] Obtain classified image data, and input the image data to be classified into the invisible watermark neural network backdoor attack model for classification;
[0097] The neural network backdoor attack model of the invisible watermark is obtained by constructing the neural network backdoor attack model of the invisible watermark described in Embodiment 2.
[0098] A well-trained network model should have the ability to resist adversarial attacks. Based on this, the classification method can verify the robustness of the neural network model, that is, whether the attacked model has a certain ability to resist poisoning attacks. "Data poisoning" tends to reduce the accuracy of the target neural network type classification, and both model owners and users hope for optimal accuracy. If this classification method is used, the input data is classified. If ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com