TrustZone-based secret key use frequency management method and system in cloud storage mode
A management method and cloud storage technology, applied in transmission systems and key distribution, can solve the problems of fast and continuous update of TPM hardware counters, key leakage, performance degradation, etc., to improve portability, enhance security, and protect security. stored effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0078] The technical solutions of the present invention will be specifically described below in conjunction with the accompanying drawings and embodiments.
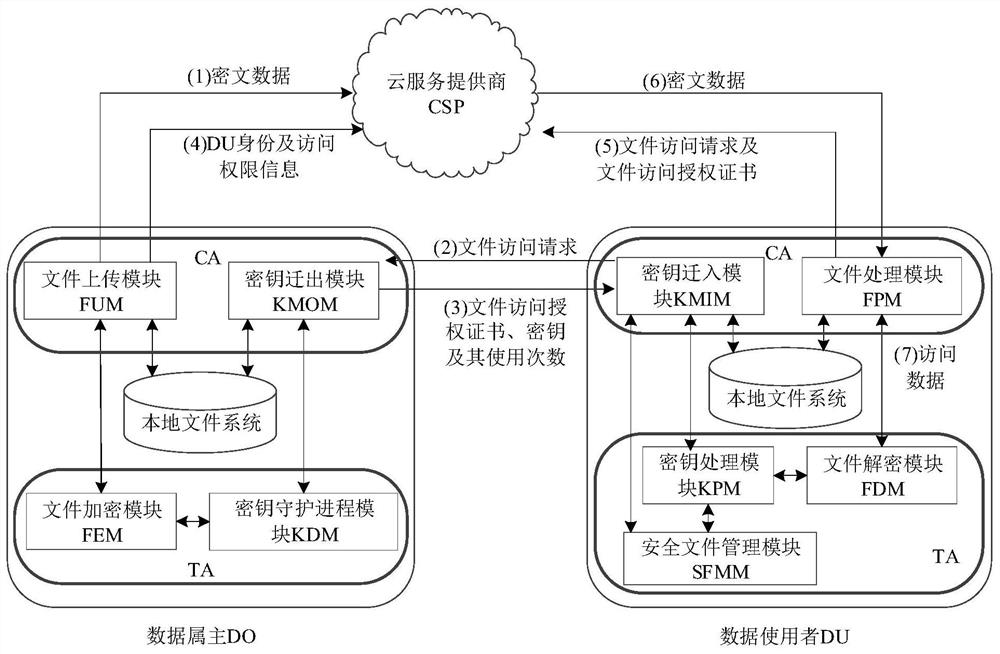
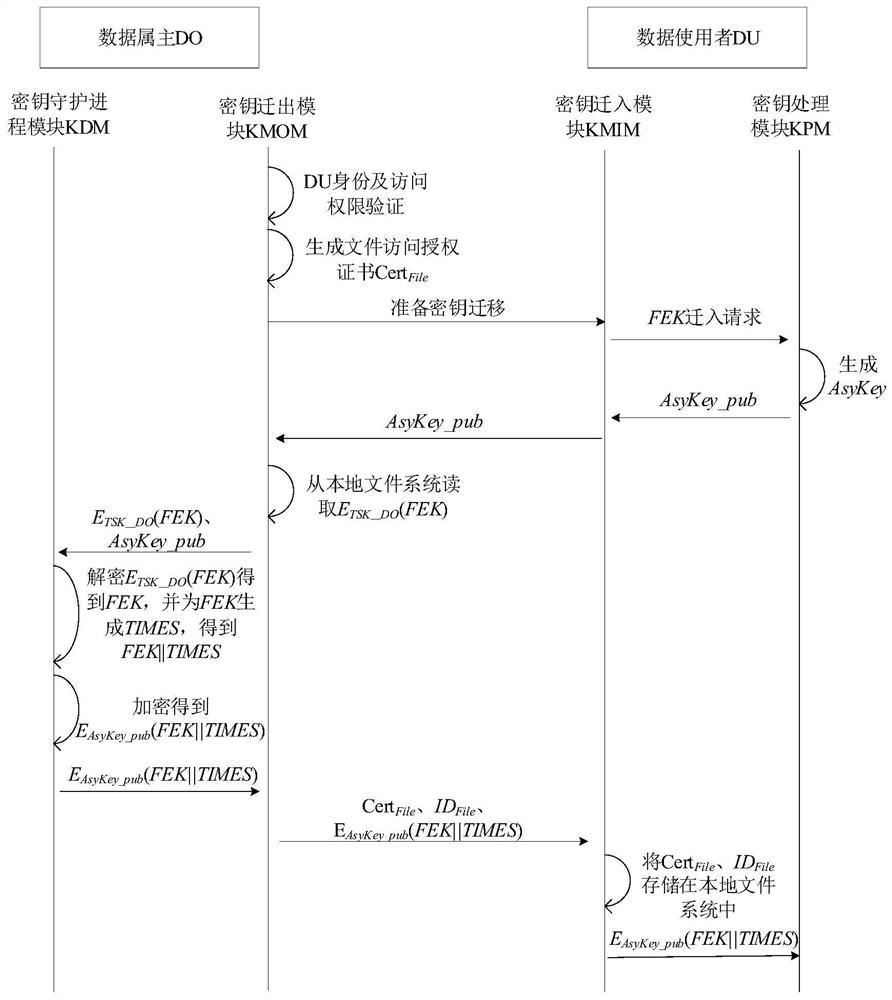
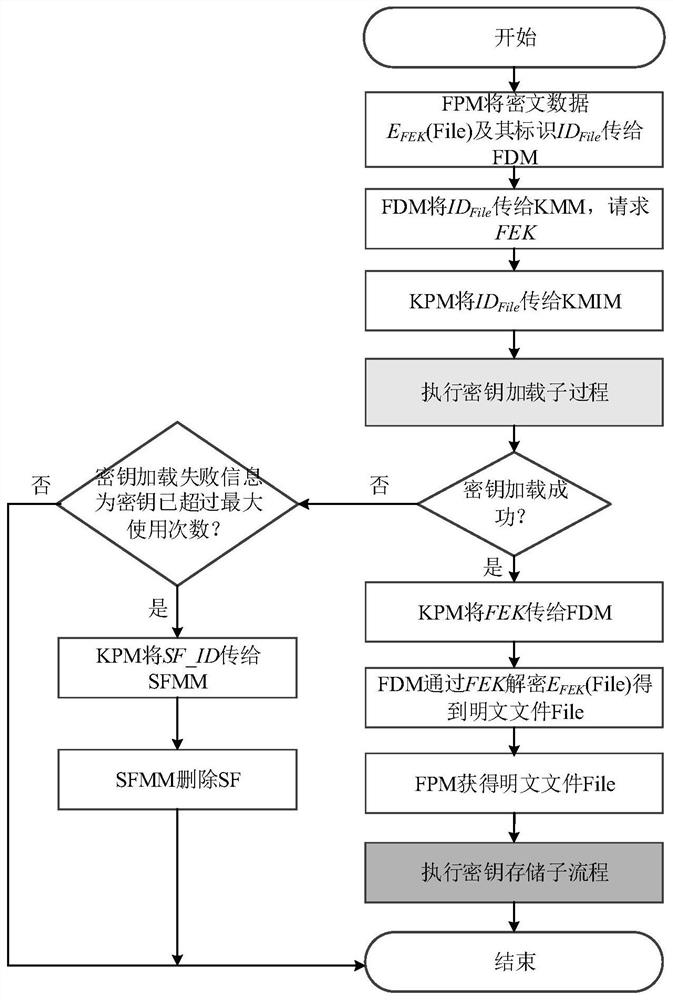
[0079] In consideration of the defects of the prior art, the present invention proposes to apply the TrustZone technology to key management and data processing in the cloud storage mode.
[0080] The present invention notes that the TrustZone technology is a hardware security extension technology proposed by ARM, which supports users to independently develop and design specific security systems, and is currently widely supported by mobile embedded devices. TrustZone technology divides the entire ARM SoC into two physically isolated execution areas through processor expansion: Normal World (NW) and Secure World (Secure World, SW), and controls NW through a secure monitor and SW switching. NW and SW have independent system resources, including registers, physical memory, and peripherals, but SW has a higher privilege level...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com