One-time pad replaceable encryption algorithm, component and equipment based on password book
An encryption algorithm and codebook technology, applied in the application field of computer software encryption algorithm, can solve the problems of cumbersome key replacement, single algorithm, insecure key storage, etc., achieve effective management, highlight substantive features, and improve resistance to differential attacks effect of ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
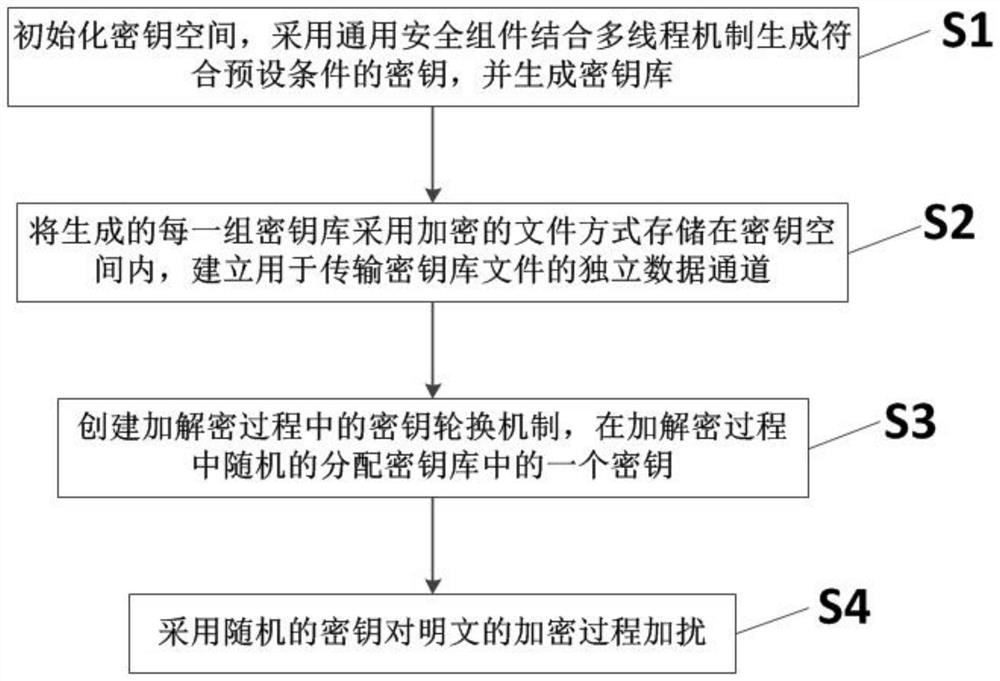
[0041] Such as figure 1 The shown one-time-pad alternative encryption algorithm based on codebook includes the following steps:
[0042] S1: Initialize the key space, use the general security component combined with the multi-thread mechanism to generate the key that meets the preset conditions, and generate the key store.
[0043] In order to improve the traditional single-key symmetric encryption algorithm, the concept of a key store is firstly introduced. The traditional single-key algorithm only supports a limited key store. This algorithm expands the key store to a large amount of space. Libraries are managed and utilized.
[0044] In order to further expand the key space and enhance the encryption strength, this encryption mechanism requires enough keys to participate in encryption and decryption, so it supports the generation of multiple keys, generally up to 16,777,216 = 2 24 A 128-bit symmetric key, each key 128bit = 16 bytes, 16,777,216*16 / 1024 = 262,144, only occu...
Embodiment 2
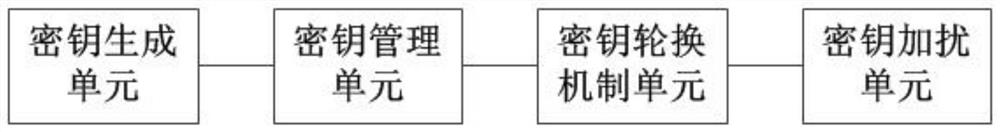
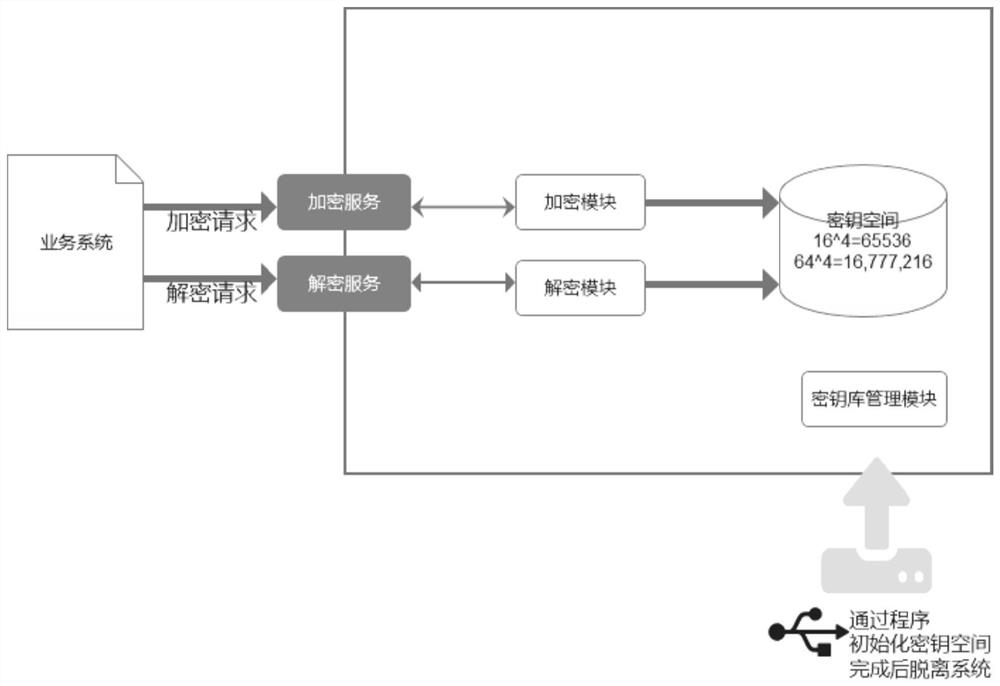
[0066] Based on Embodiment 1, the cipherbook-based one-time pad replaceable encryption algorithm proposed by the present invention can be packaged in an independent service component to provide external encryption and decryption services, and all algorithms, keystores, and encryption and decryption services are packaged. Form a black box, use the temporary storage medium to pass the initialization method, and after verifying the keystore to protect the encryption key, import the keystore into the server memory at one time, so that the keystore only exists in the memory, improving performance and security. The encryption algorithm is deployed in an independent service component, and the process of providing external encryption and decryption services is as follows: image 3 As shown, the encryption algorithm proposed by the present invention is equivalent to the core component of the software encryption server.
[0067] In addition, if Figure 4 As shown, the core components o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com