Identity authentication method and device
An identity authentication and identity identification technology, applied in the field of identity authentication methods and devices, can solve problems such as network service attacks, processing resource occupation, and impact, and achieve the effects of reducing signaling interaction, avoiding processing pressure, and fast computing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0101] The embodiments of the present application will be further described in detail below in conjunction with the accompanying drawings.
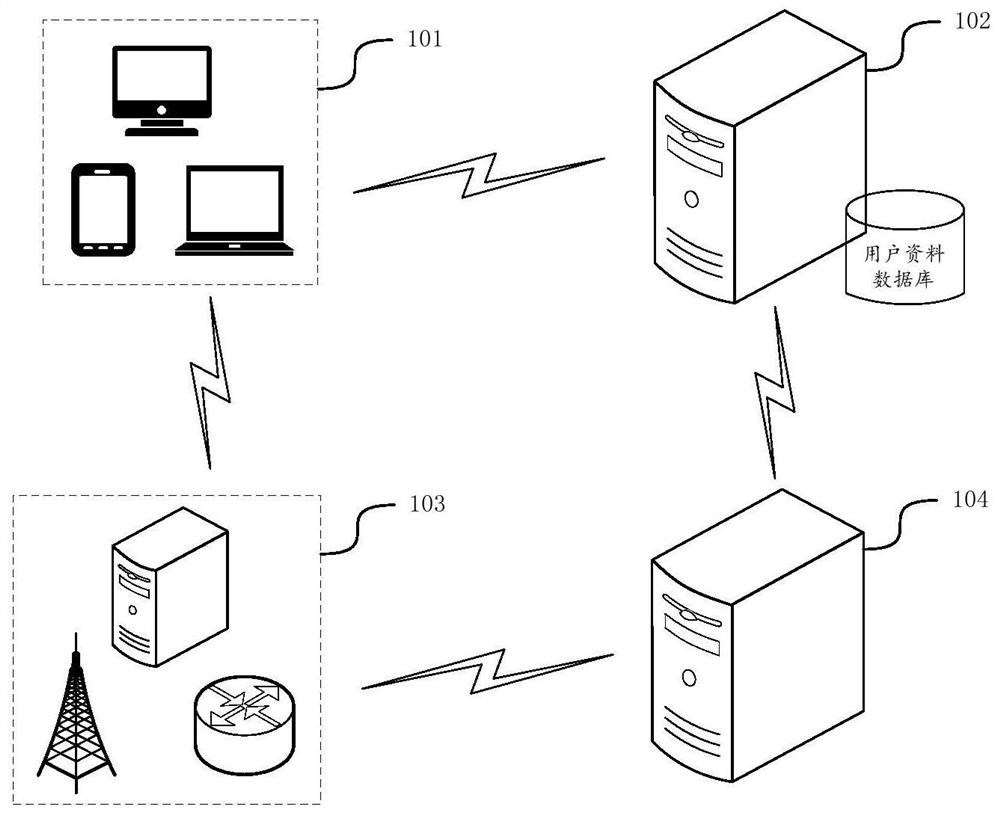
[0102] figure 1 It is a schematic diagram of an application scenario of an identity authentication method provided in the embodiment of this application, see figure 1 , the application scenario of the identity authentication method includes: a terminal device 101 , an identity management server 102 and a network device 103 , further, the implementation environment may also include an audit server 104 .
[0103] Terminal equipment 101 may refer to user equipment (user equipment, UE), access terminal, subscriber unit, subscriber station, mobile station, mobile station, remote station, remote terminal, mobile device, user terminal, terminal, wireless communication device, user agent or user device. The access terminal can be a cellular phone, a cordless phone, a session initiation protocol (session initiation protocol, SIP) phone, a wirele...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com