A realization method and system integrating multiple signature encryption algorithms
A technology of encryption algorithm and implementation method, which is applied in transmission system, digital transmission system, computing, etc., can solve problems such as inability to implement multiple encryption algorithms and meet various user integrated usage scenarios, and achieve high signature encryption efficiency and improved Variety and flexibility, the effect of ensuring the speed of operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
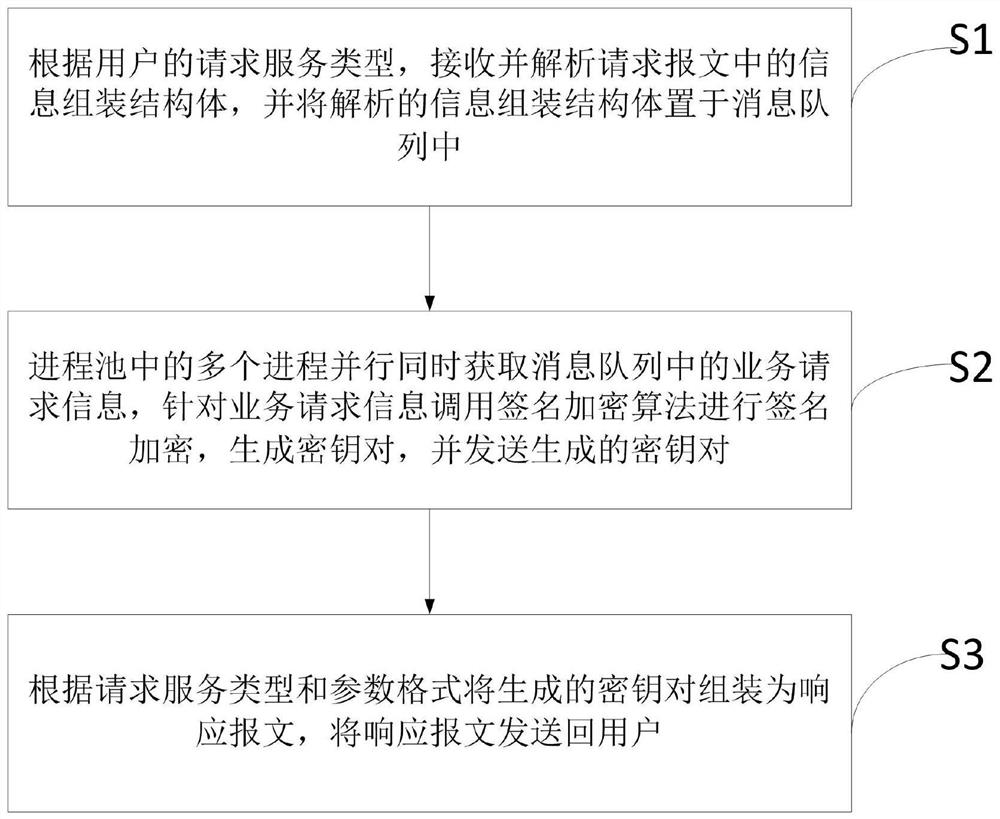
Examples
Embodiment 1
[0053]
[0054] The above example is a request to generate a key pair using the asymmetric encryption algorithm SM2. Parse the algorithm (algorithm),
[0055] Socket service request: when the request receiving module receives the socket request message, it parses the socket message
[0058] The 7-8 bits of the socket message, identify operations, such as 01: generate a key pair, 02: signature, 03: verify signature etc.;
[0059] The 9-last bit of the socket message identifies other information, such as key, data to be signed, data to be encrypted, etc.
[0060] Local executable file service: direct invocation in a way that supports the command line.
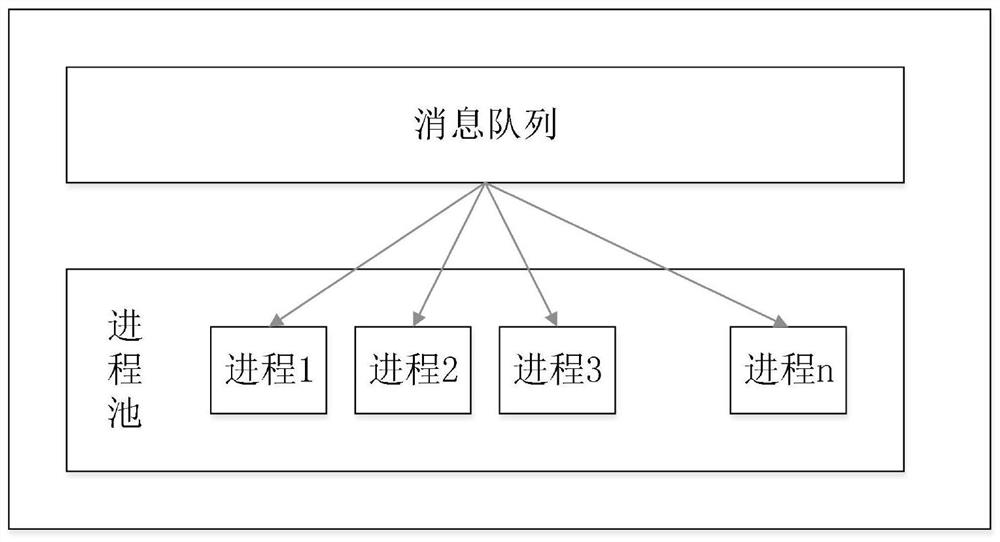
[0064] [process]
[0065] processnum=5
[0068] web request service: when a request for generating a SM2 key pair in the web request service is received, the
[0069]
[0070]
[0071] Wherein, privatekey and publickey are the key pair of the generated asymmetric encryption algorithm SM2.
[0072] Socket request service: when receivi...
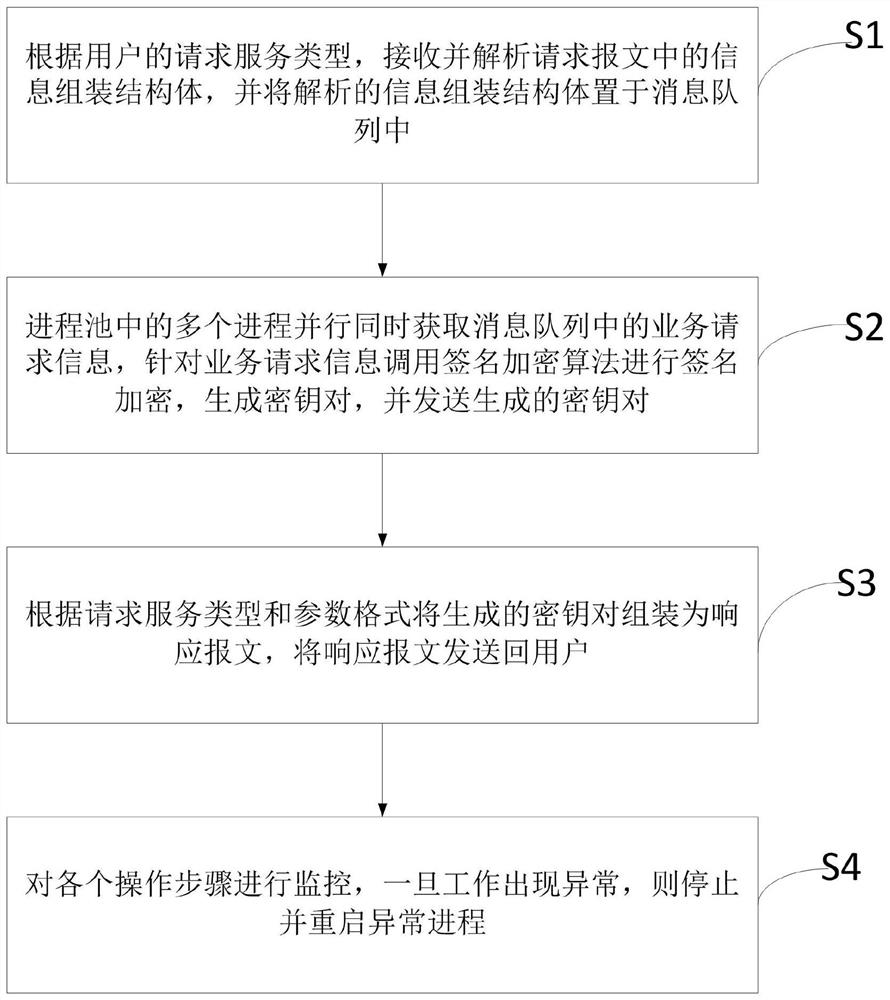
Embodiment 2
[0088] S4, each operation step is monitored, and once an abnormality occurs in the work, the abnormal process is stopped and restarted.
[0091] [monitor]
[0092] init=1
[0093]lownum=2
[0094] highnum=20
[0095]time=5
Embodiment 3
[0105] S4, each operation step is monitored, once abnormality occurs in the work, then stop and restart the abnormal process;
[0106] S5, log each operation step and execution result.
[0107] In step S5, when the startup starts, the log part is initialized, and all log configuration information is
[0108][loginfo]
[0109] logpath= / var / log
[0110] logmaxsize=2
[0111] loglevel=1
[0112] The technical solution of the present invention can also support the hardware acceleration function, and the hardware can be configured to improve the encryption and decryption speed;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com