A detection method and device for a compromised node in a wireless sensor network
A technology of wireless sensors and detection methods, applied in the field of the Internet of Things, can solve problems such as hazards, difficult detection of compromised nodes, and inability to distinguish the real situation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] In order to better explain the present invention and facilitate understanding, the present invention will be described in detail below through specific embodiments in conjunction with the accompanying drawings.
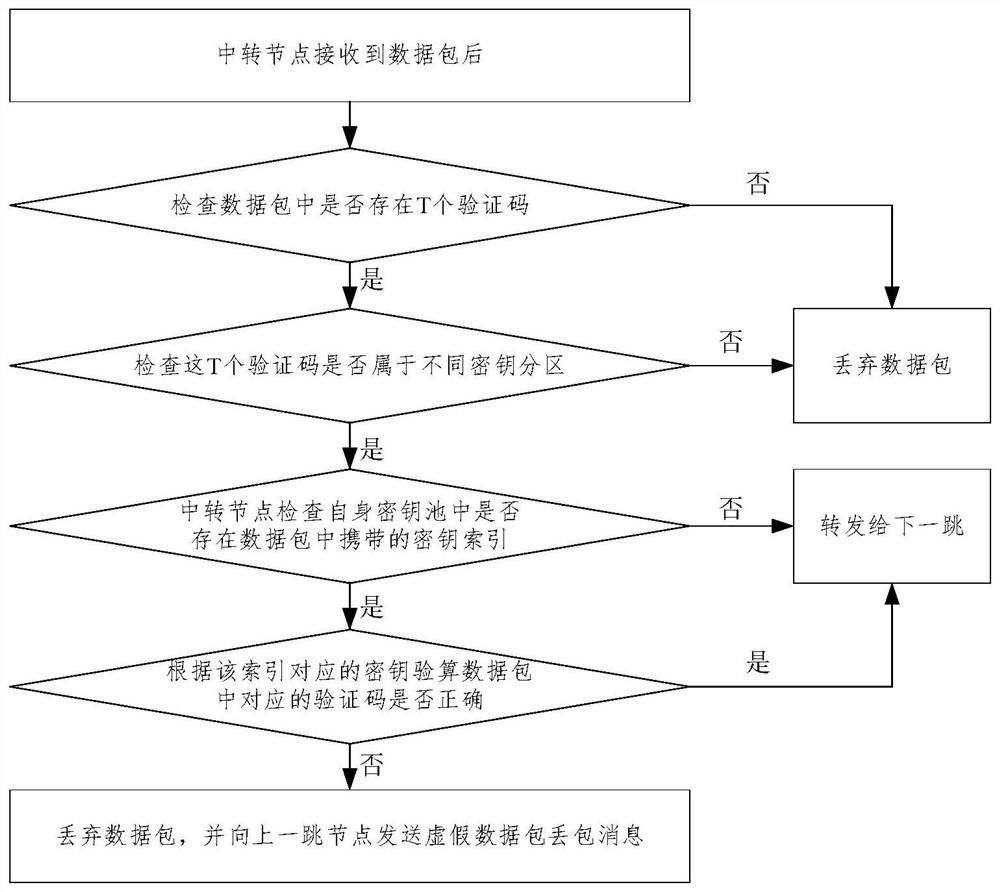
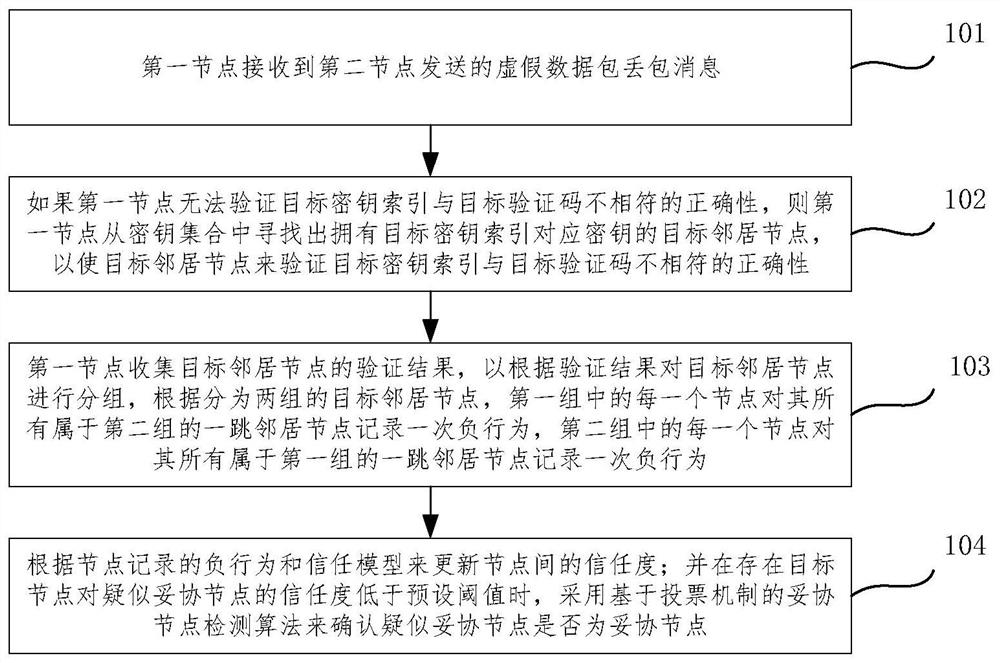
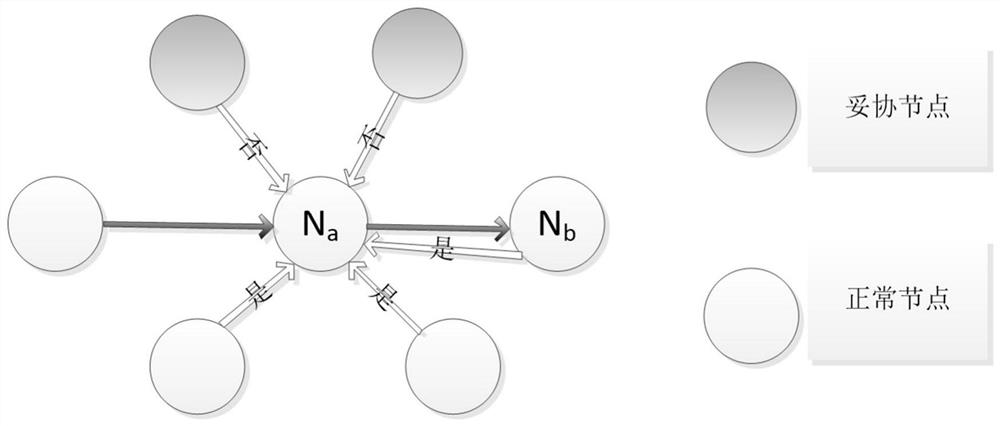
[0057] The method and device for detecting compromised nodes in the wireless sensor network proposed by the embodiments of the present invention analyze and process the false packet loss attack of the compromised node in the forwarding process of the SEF model data packet, and propose a trapping mechanism on the way. It provides opportunities to induce compromised nodes to make mistakes, can effectively differentiate compromised nodes and normal nodes, and detect compromised nodes in wireless sensor networks based on differentiated compromised nodes and normal nodes, and can detect compromised nodes that launch fictitious false packet loss attacks If it is detected, it indirectly solves the packet loss attack of fictitious false data packets.
[0058] In order ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com