Web vulnerability scanning method and vulnerability scanner
A vulnerability scanning and vulnerability technology, which is applied in the field of computer networks, can solve the problems of inaccurate discrimination of page survival, high vulnerability repetition rate, long scanning time, etc., to achieve the effect of ensuring smooth development, reducing false alarm rate, and reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0030] Based on the same inventive concept, this embodiment provides a vulnerability scanner, the problem-solving principle of which is similar to that of the web vulnerability scanning method, and repeated descriptions will not be repeated here.
[0031] The vulnerability scanner described in this embodiment includes:
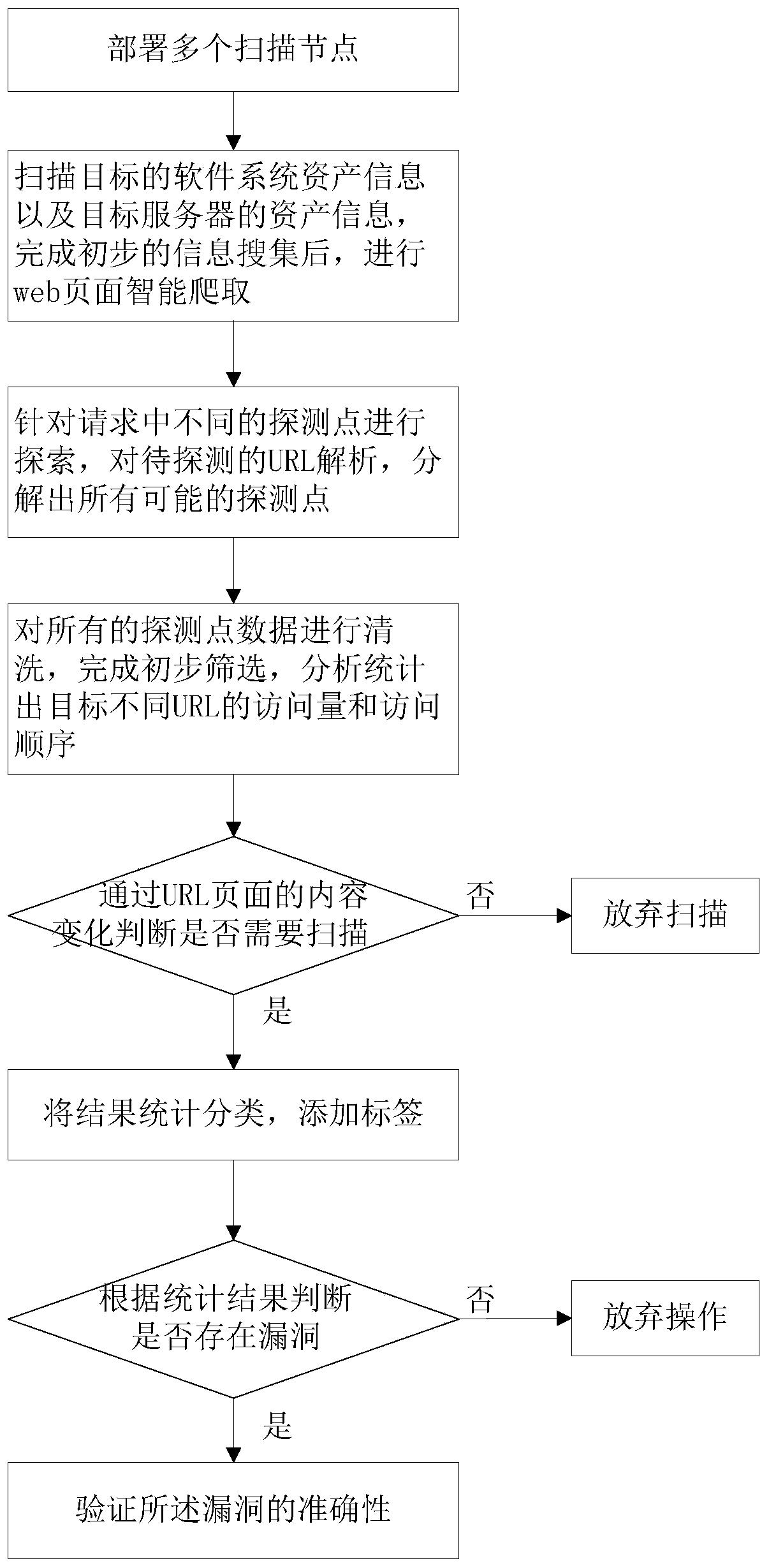
[0032] Node deployment module, used to deploy multiple scanning nodes;
[0033] The intelligent crawling module is used to scan the asset information of the target software system and the asset information of the target server, and perform intelligent crawling of web pages after completing the preliminary information collection;
[0034] The parsing module is used to explore different detection points in the request after crawling is completed, analyze the URL to be detected, and decompose all possible detection points;
[0035] The judgment module is used to clean all the detection point data, complete preliminary screening, analyze and count the visit volum...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com