Anomaly analysis method and device for network data
An analysis method and network data technology, applied in the direction of instruments, character and pattern recognition, electrical components, etc., can solve problems such as limited application scenarios, difficult network security situation prediction, and prediction accuracy to be improved, so as to reduce resource occupation and improve Accuracy, the effect of improving the operating speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] In this embodiment, a method for abnormal analysis of network data is proposed, and the overall process is as follows figure 1 .
[0037] An abnormality analysis method for network data, comprising the following steps:
[0038] S100. The data collection engine collects log data in the network. The log data comes from network devices, security software and hardware, including traffic logs, operation logs, security audit logs, alarm logs, etc., and the log data is stored in the database of the ES cluster.
[0039] S200, extract traffic data satisfying conditions from the database according to the start and end time of the task configuration, and analyze the abnormal behavior. like figure 2 shown, including:
[0040] Establish a classification model: For the data of each abnormal scene, execute the data cleaning algorithm separately, filter the rough data, aggregate and denoise the process of converting it into formatted data, including: checking data consistency, proc...
Embodiment 2
[0071] This embodiment provides an abnormal analysis device for network data, such as Figure 5 shown, including:
[0072] The abnormal behavior analysis module is used to obtain the traffic log data between the start and end time of the abnormal analysis task, convert the traffic metadata into a data type that can be recognized by the classification model, input the converted data into the classification model, and output the data corresponding to According to the category of the data, machine learning or intelligence matching is performed respectively to identify abnormal behavior and generate an alarm for the corresponding IP;
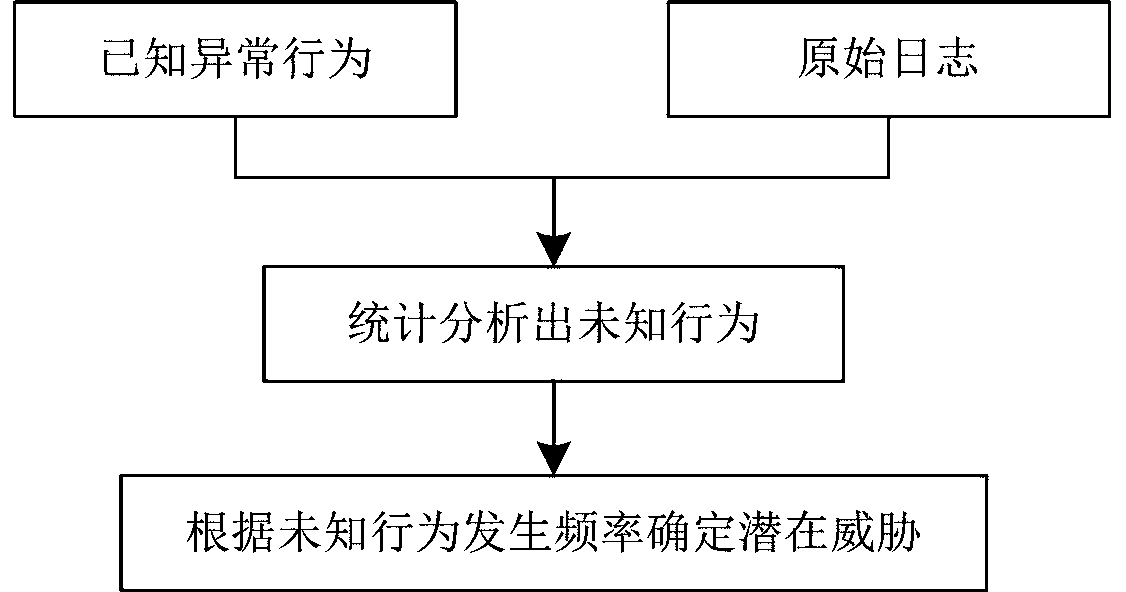
[0073] A potential threat analysis module, configured to associate the discovered abnormal behavior with the original log, statistically analyze the frequency of occurrence of the unknown behavior in the original log, and determine the unknown behavior exceeding a specific frequency as a potential threat;
[0074] The security trend analysis module...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com