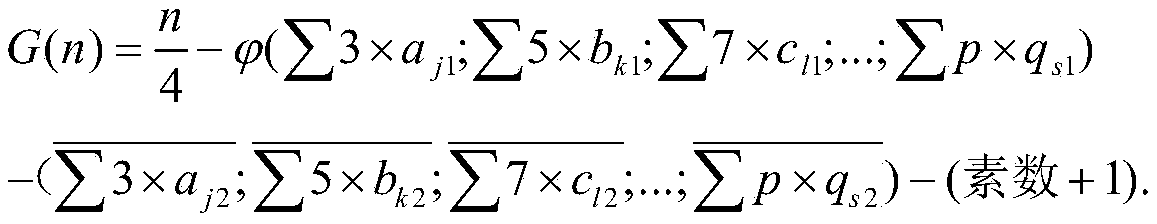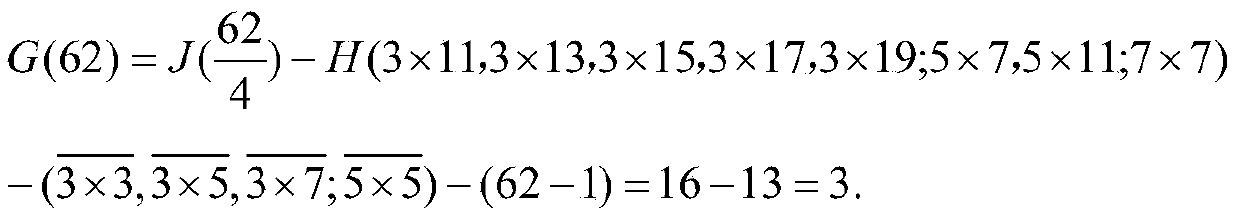Novel password
A new type of cipher and encoding technology, applied in the field of cipher compilation, can solve problems such as defeating attempts, low cost, and information errors received by the receiver, and achieve the effects of great business prospects, wide practicability, and easy decoding
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] When the present invention is actually implemented, writing the Hange cipher must rely on the mathematical formula for Goldbach's conjecture equation.
[0031] The formula for finding Goldbach’s conjecture equation is as follows: Suppose n is an even number greater than 6, the Goldbach’s conjecture equation can be obtained by the following formula: (This formula is my original creation, published on "Science Network" and "Strength Country Forum" )
[0032]
[0033] In the above formula:
[0034] (1) G(n) indicates the number of times Goldbach's conjecture can be established when n is an even number greater than 6;
[0035] (2) Indicates the number of odd numbers in the lower half area, when the value is not an integer, use the rounding method to round up;
[0036] (3) Indicates the number of all qualified odd composite numbers in the lower half area, and only the first one appears when there is overlap;
[0037] (4) Indicates the number of "prime composite n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com