Single sign-on authentication method based on inadvertent pseudo-random function and signcryption
A pseudo-random function and single sign-on technology, applied in the field of information security, can solve problems such as increased deployment costs, offline dictionary guessing attacks, and inability to be deployed independently, so as to reduce the difficulty of identity maintenance, prevent insider attacks, and eliminate potential threats Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0094] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the embodiments. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
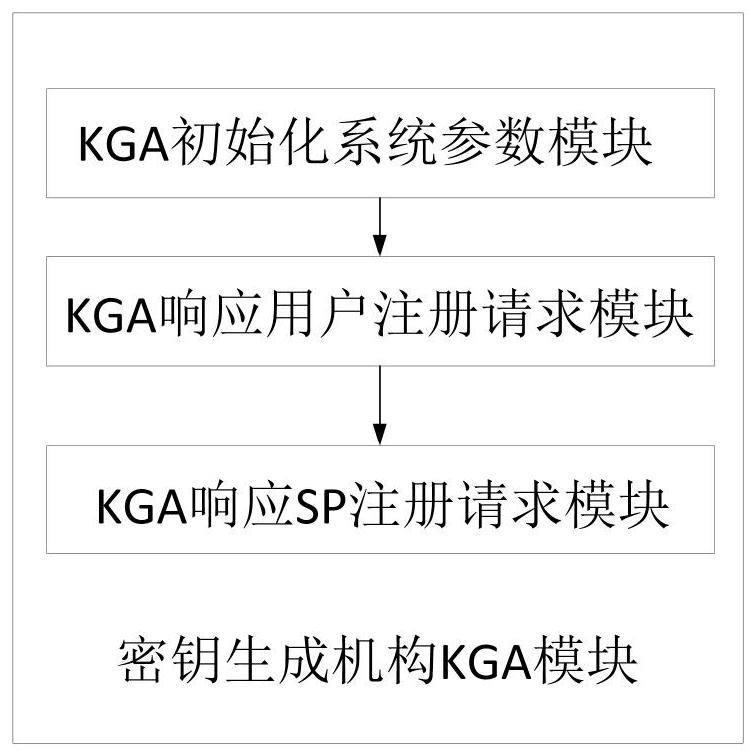
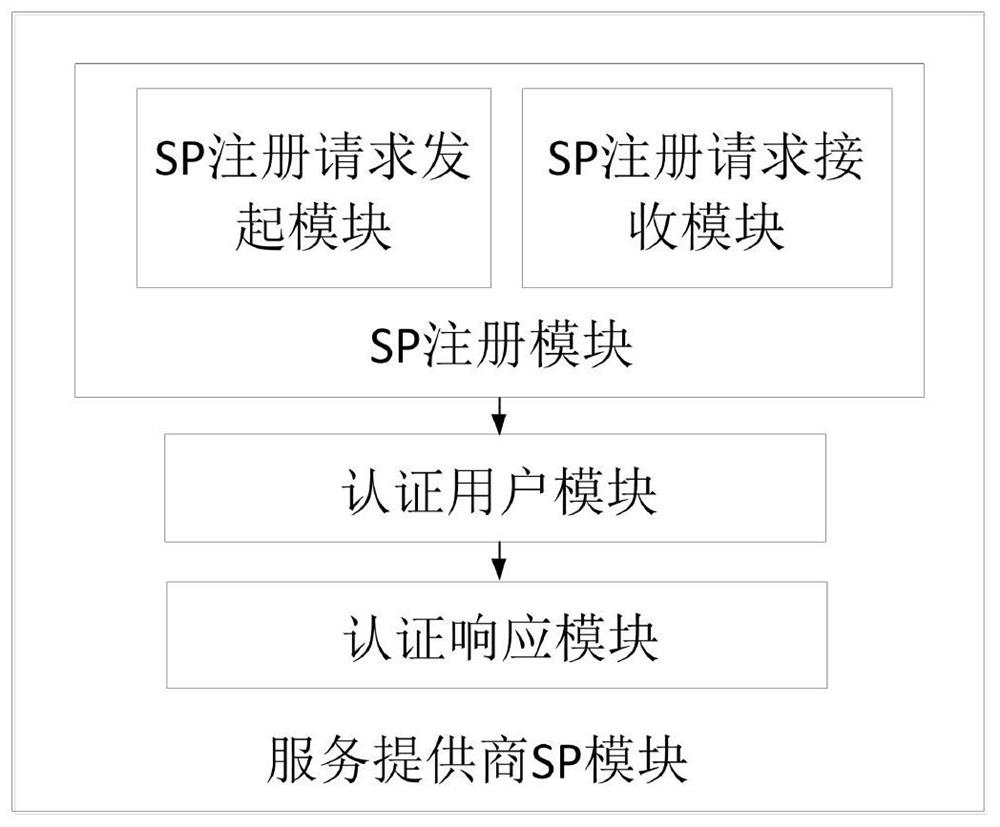
[0095] In view of the existing technology or the existence of password validators, the adversary can easily implement offline dictionary attacks and insider attacks; or does not implement two-way authentication and key negotiation, relies on encryption infrastructure such as TLS / SSL, and cannot be deployed independently; The properties of KCI attack, the present invention solves the above problems by combining OPRF and signcryption scheme. The specific process includes the user and SP completing the registration at the KGA, obtaining the signcryption private key required for the authentication stage, and in order t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com