An underwater node authentication method based on symmetric polynomial and ECC algorithm
A symmetric polynomial and authentication method technology, applied in the field of underwater node authentication based on symmetric polynomial and ECC algorithm, can solve problems such as high communication overhead, achieve the effect of less communication overhead, easy management, and reduction of communication conflicts and collisions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
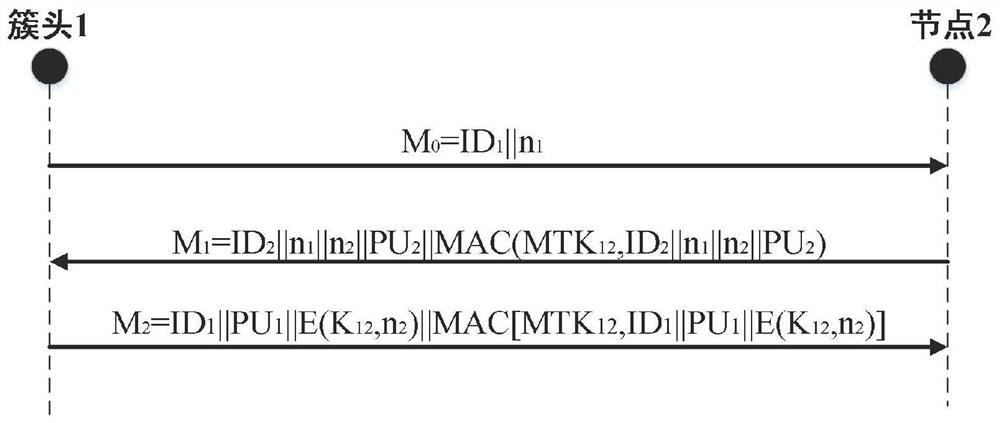
[0033] Such as figure 1 , figure 2 As shown, an underwater node authentication method based on symmetric polynomial and ECC algorithm includes the following steps:
[0034] (1) Initialization
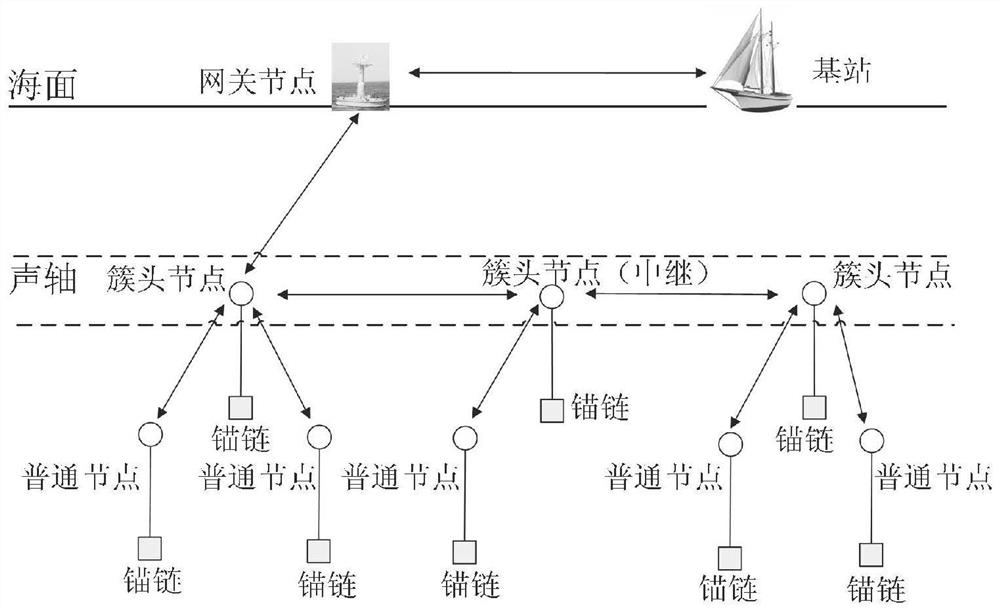
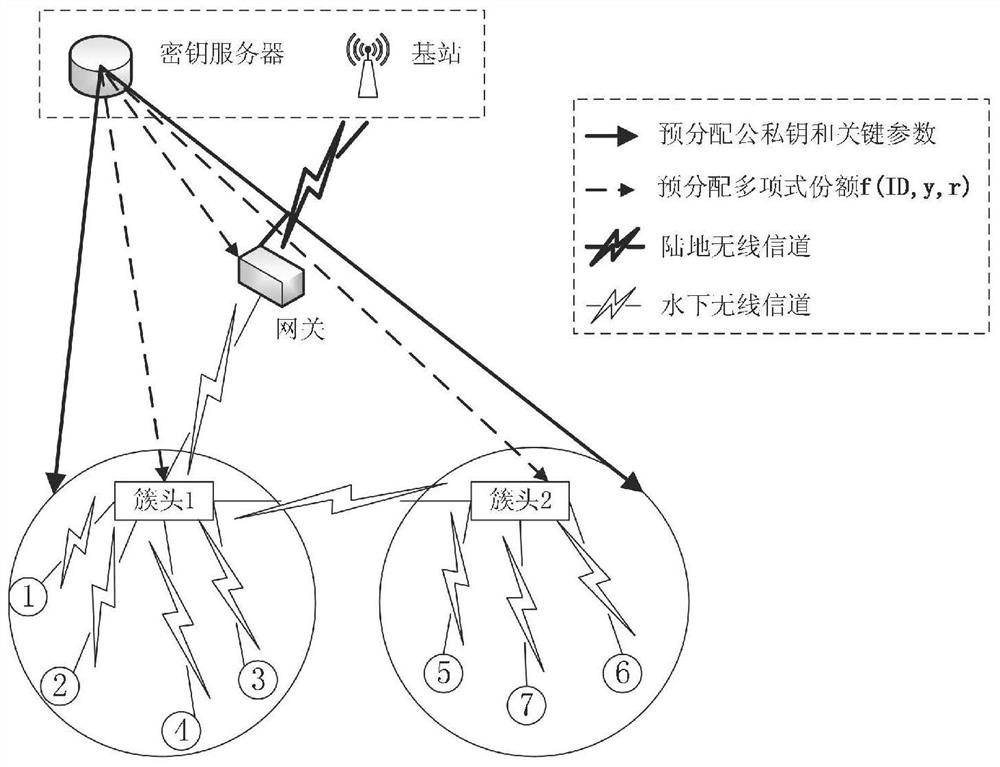
[0035]1) The base station selects and generates security parameters required for network authentication and stores them in all network nodes. Network nodes include gateway nodes, cluster head nodes and common nodes.
[0036] 2) The base station assigns unique IDs to all physical components in the network.
[0037] 3) The base station calculates the public-private key pair (PU) for all network nodes i , PR i ) and stored in the corresponding node. After the calculation is completed, the base station deletes the private keys of all nodes, and only saves the identity public key pair of the node (ID i , PU i ). After calculating the public and private keys of all nodes, the unique identity key pair (ID i , PU i , PR i ) is stored in the identity identifier as ID i in the node. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com