Orbital angular momentum key distribution method based on odd coherent light source and quantum storage
An orbital angular momentum and key distribution technology, applied in the field of quantum key distribution, can solve the problem of low security key generation rate, and achieve the effect of increasing the maximum transmission distance, reducing the bit error rate, and being easy to implement.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
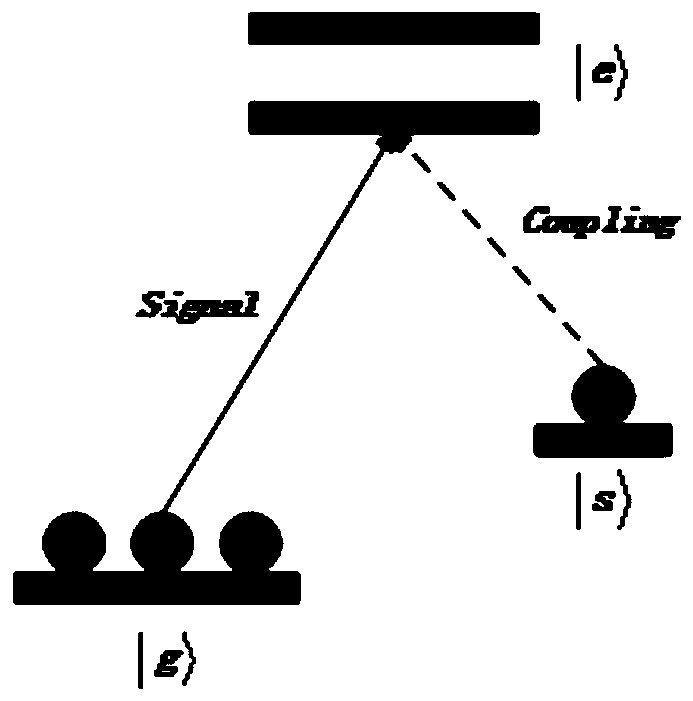
[0053] In this embodiment, an OAM key distribution method based on odd coherent light sources and quantum storage is disclosed, which is used to enable both Alice and Bob to obtain a shared key.
[0054] In the present invention, there is a certain distance between Alice and Bob as two communicating parties.
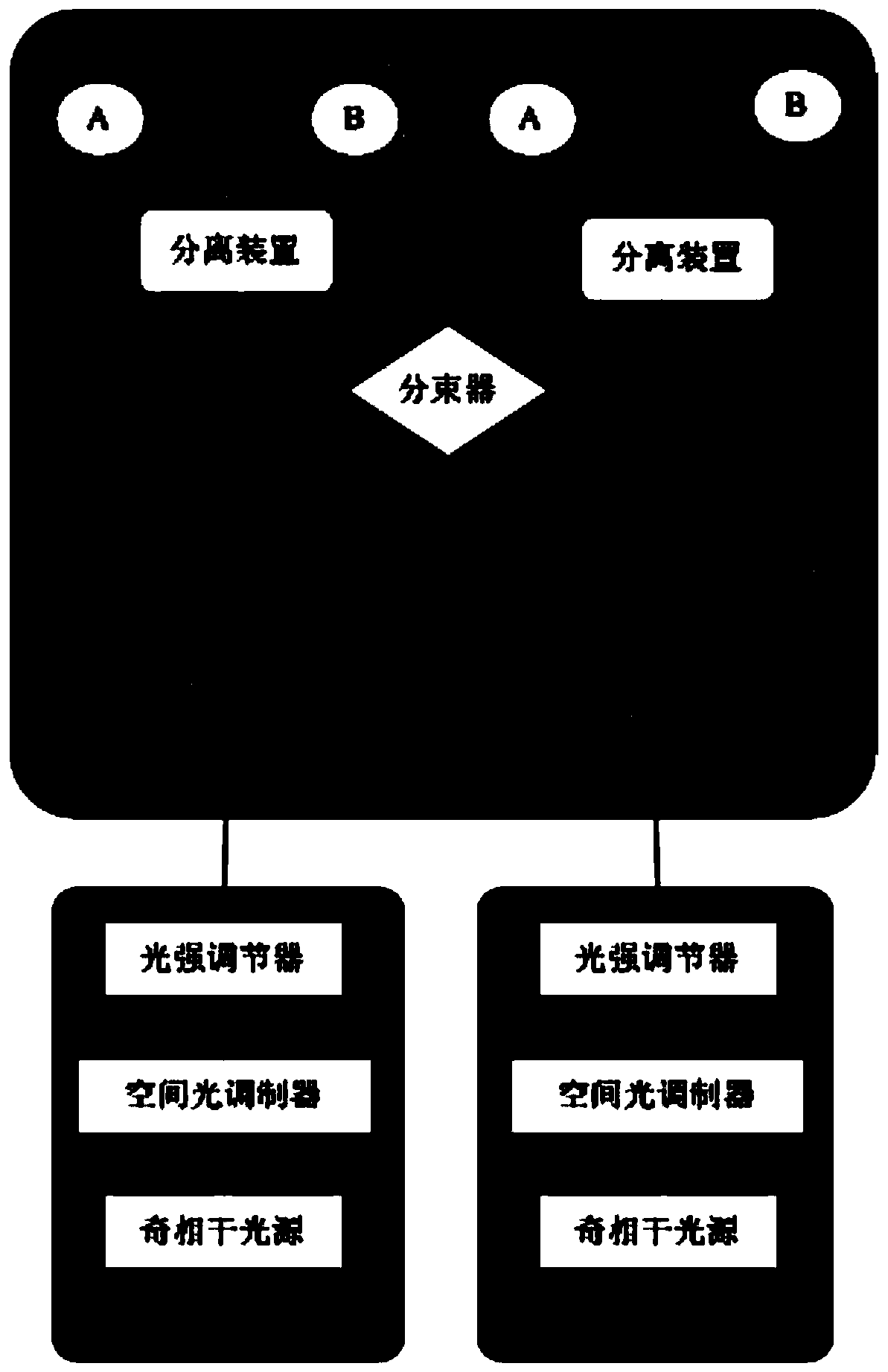
[0055] Such as figure 2 Shown, the present invention carries out according to the following steps:
[0056] Step 1. Alice and Bob use their odd coherent light sources to prepare coherent light pulses respectively;
[0057] In this step, Alice uses odd coherent light source A to prepare coherent light pulses, and Alice obtains her own coherent light pulses; at the same time, Bob uses odd coherent light source B to prepare coherent light pulses, and Bob obtains his own coherent light pulses; odd coherent light source A and odd coherent light pulses The parameters of the coherent light source B are the same, and the coherent light pulse obtained by Alice is also the same...
Embodiment 2
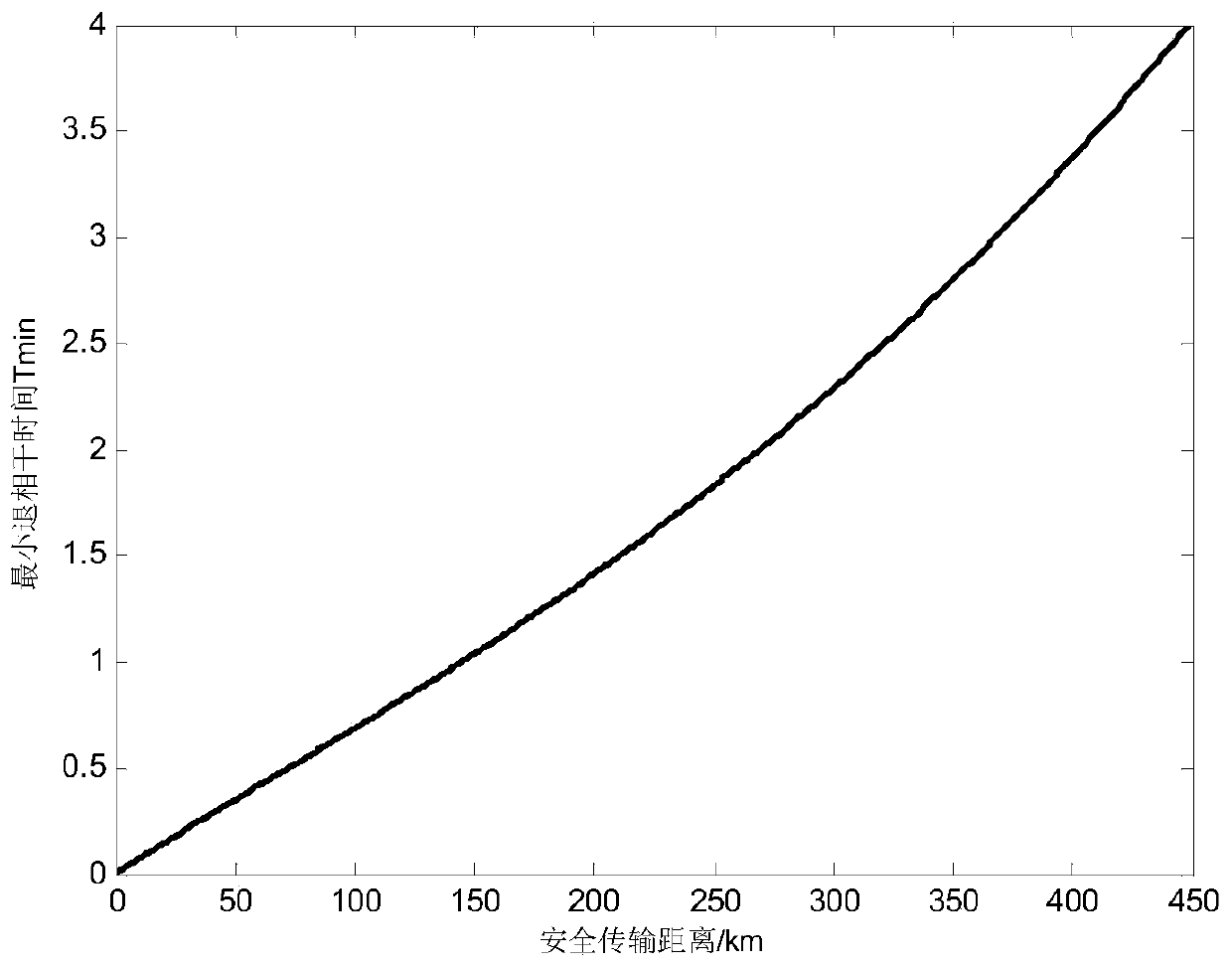
[0082] In this example, the effectiveness of the method provided by the present invention is verified.
[0083] The calculation formula of the key generation rate of the method provided by the invention is as follows:
[0084]
[0085] 1 / of which Raw key generation rate for unfiltered:
[0086]
[0087] In formula (3), R s The frequency at which laser pulses are fired for Alice and Bob; P BSM Probability of success when performing BSM measurements for third parties; P 0 is the probability that the photon state sent by Alice and Bob can successfully reach the third party and be stored in the quantum memory, which is related to the channel transmission distance L. P BSM The expression of is as follows:
[0088]
[0089] P in formula (4) D refers to the dark count rate; record η MD = η M n D , where η M is the quantum storage efficiency, η D is the detector efficiency.
[0090] In formula (2), The gain of sending a single photon sta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com