Identity encryption equivalence test method, device and system based on user group and medium
A technology of identity encryption and testing methods, applied in the field of information security, can solve problems such as inability to encrypt and guess plaintext, leakage, and difficulty in ensuring ciphertext information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
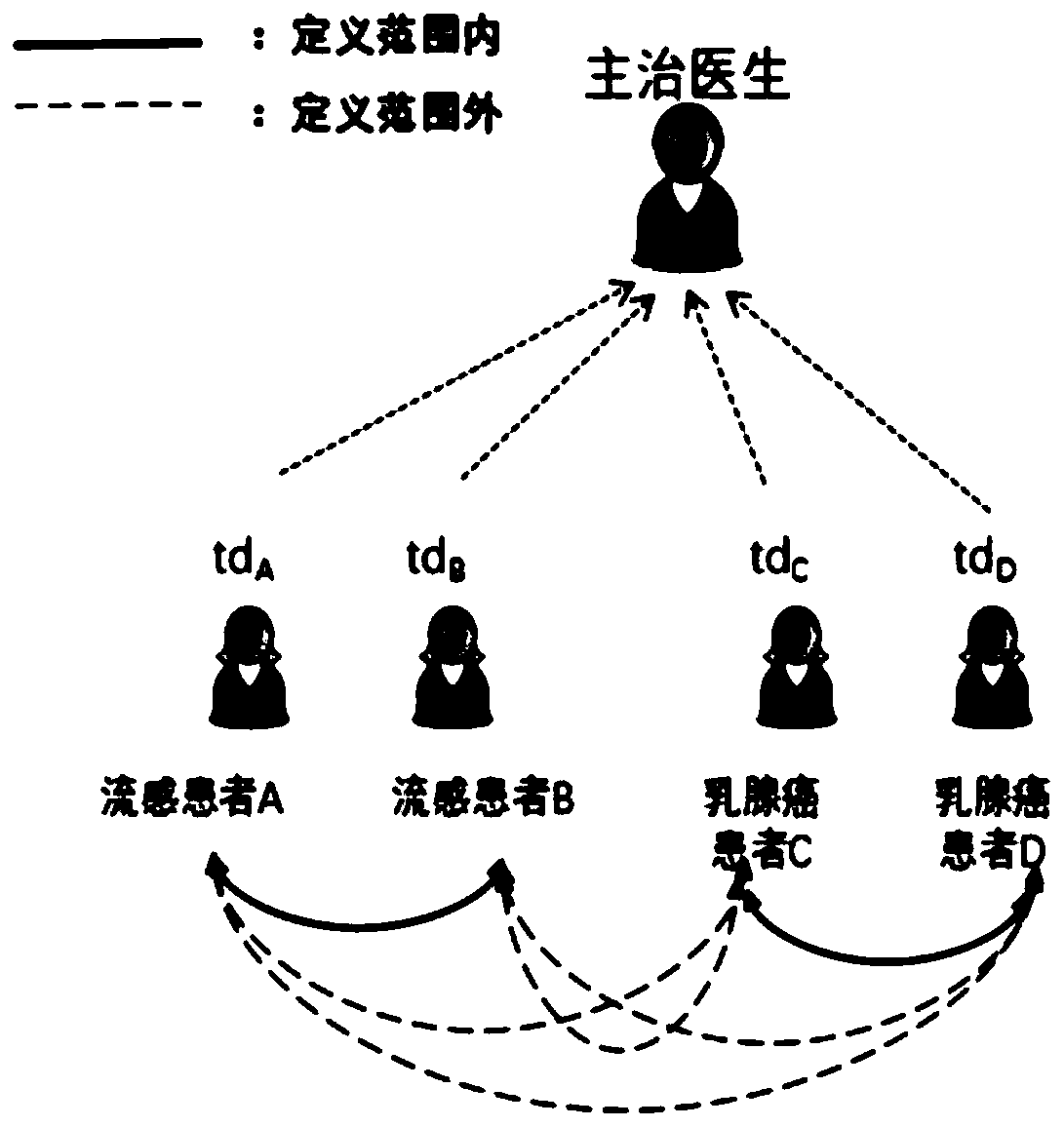
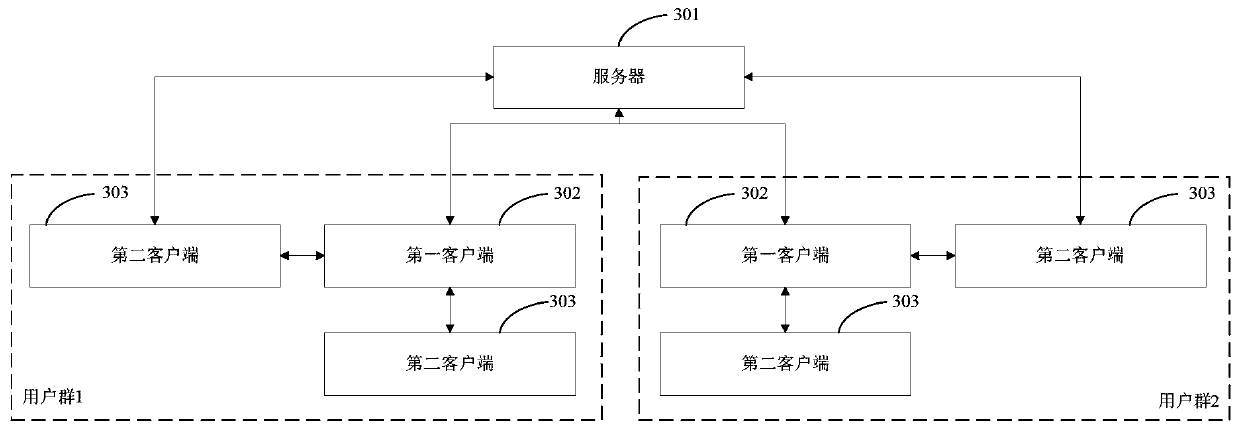
[0079] like image 3 As shown, this embodiment provides a group ID-based Encryption With Equality Test (Group ID-based Encryption With Equality Test, referred to as G-IBEET) system, the system includes a server 301 and two user groups, each The user group includes a first user and two second users, the first user is a group administrator, the client used by the first user is the first client, the second user is a group member, and the second user uses The client is the second client, and each second user has a corresponding second user ID, in each user group, the first client 302 and the second client 303 are respectively connected to the server 301, and the second A client 302 is connected to a second client 303 .
[0080] like image 3 and Figure 4As shown, the identity encryption equivalence testing system of this embodiment can be applied in a network medical system. The two user groups are respectively a flu patient group and a breast cancer patient group. The flu pat...
Embodiment 2
[0108] like Figure 7 As shown, this embodiment provides an identity encryption equivalent testing device based on user groups, there is at least one user group, and each user group corresponds to a disease, including a first user and at least two second users , the first user is a group administrator, the second user is a group member, and each second user has a corresponding second user ID;
[0109] The device is applied to the first client in each user group, including a first authorization module 701, a second authorization module 702 and a sending module 703, and the specific functions of each module are as follows:
[0110] The first authorization module 701 is configured to perform group authorization on the second user, and send the group authorization to the second client, so that the second client encrypts the plaintext to be encrypted to form ciphertext, and sends the ciphertext sent to the server.
[0111] The second authorization module 702 is configured to rece...
Embodiment 3
[0114] like Figure 8As shown, this embodiment provides an identity encryption equivalent testing device based on user groups, there is at least one user group, and each user group corresponds to a disease, including a first user and at least two second users , the first user is a group administrator, the second user is a group member, and each second user has a corresponding second user ID;
[0115] The device is applied to the second client in each user group, including a receiving module 801, an encryption module 802, a submission module 803 and a decryption module 804. The specific functions of each module are as follows:
[0116] The receiving module 801 is configured to receive the group authorization sent by the first client.
[0117] The encryption module 802 is configured to encrypt the plaintext to be encrypted to form ciphertext, and send the ciphertext to the server.
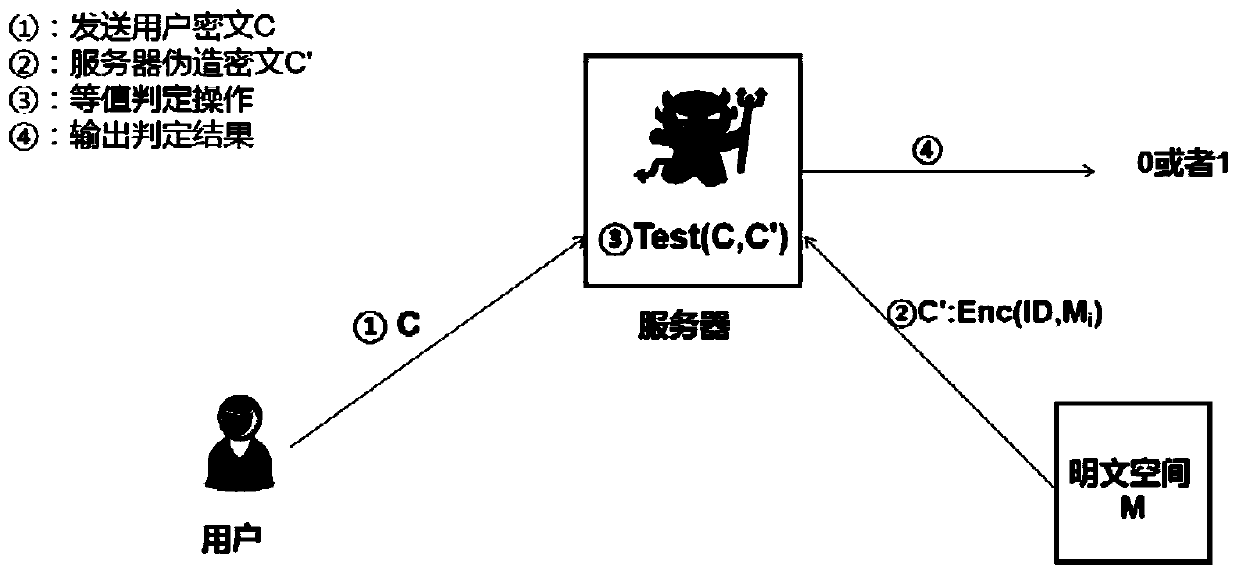
[0118] The submission module 803 is configured to submit a ciphertext equivalence test request ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com