Edge computing hardware architecture based on RISC-V
A RISC-V, edge computing technology, applied in the computer field, can solve the problems of high power consumption, high cost, consumption, etc., and achieve the effect of low power consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
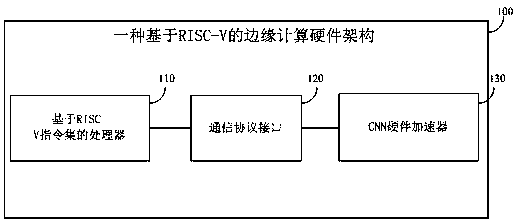
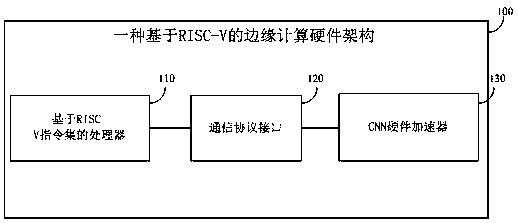
[0047] Such as figure 1 As shown, a RISC-V-based edge computing hardware architecture 100 includes: a processor 110 based on the RISC-V instruction set, a communication protocol interface 120 connected to the processor 110 based on the RISC-V instruction set, and a communication protocol interface 120 connected CNN hardware accelerator 130 .
[0048] The processor 110 based on the RISC-V instruction set can be used to process and execute instructions compiled from high-level languages. If there is a need to operate and control the CNN hardware accelerator in the instructions, it will pass the communication protocol interface in the form of memory access 120 controls and operates the CNN hardware accelerator 130 .
[0049]The communication protocol interface 120 can be used to realize the communication between the processor 110 based on the RISC-V instruction set and the CNN hardware accelerator 130. The communication protocol has two data channels, one is the communication be...
Embodiment 2
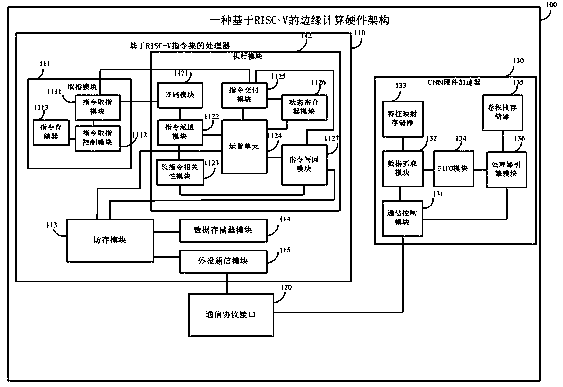
[0052] Such as figure 2 As shown, a processor 110 based on the RISC-V instruction set includes an instruction fetch module 111 , an execution module 112 , a memory access module 113 , a data memory module 114 , and a peripheral communication module 115 .
[0053] The instruction fetching module 111 can be used to obtain instructions, determine whether branch prediction is required for the instruction, generate the address of the next instruction, and transmit the instruction value, address, prediction and other information to the execution module 112 .
[0054] The instruction fetch module 111 includes an instruction fetch module 1111 , an instruction fetch control module 1112 , and an instruction memory 1113 .
[0055] The instruction fetch module 1111 can be used to generate the instruction address, partially decode the instruction value sent back from the instruction fetch control module 1112, and decode whether it is a jump instruction. For the jump instruction, branch pr...
Embodiment 3
[0058] Such as figure 2 As shown, the execution module 112 in this embodiment further includes a decoding module 1121 , an instruction dispatching module 1122 , and a long instruction dependency module 1123 .
[0059] Among them, the decoding module 1121 is connected with the instruction fetching module 1111, and can be used to receive the instruction information from the instruction fetching module 1111, decode the instruction information, and decide whether to fetch the corresponding instruction from the register according to the decoding result. value. At the same time, the result information decoded by this instruction is transmitted to the instruction dispatch module 1122, and the instruction dispatch module 1122 decides to dispatch the information to the operation unit module 1124 for execution. The instruction dispatch module 1122 can be used to analyze the decoding information transmitted by the decoding module 1121 to decide whether to dispatch. The instruction dis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com