Multi-tenant-oriented container mirror image security configuration method and system, operation terminal and storage medium
A security configuration, multi-tenant technology, applied in the direction of computer security devices, instruments, software deployment, etc., can solve problems such as the rapid spread of hazards, and achieve the effect of enhancing security, reducing transmission time, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
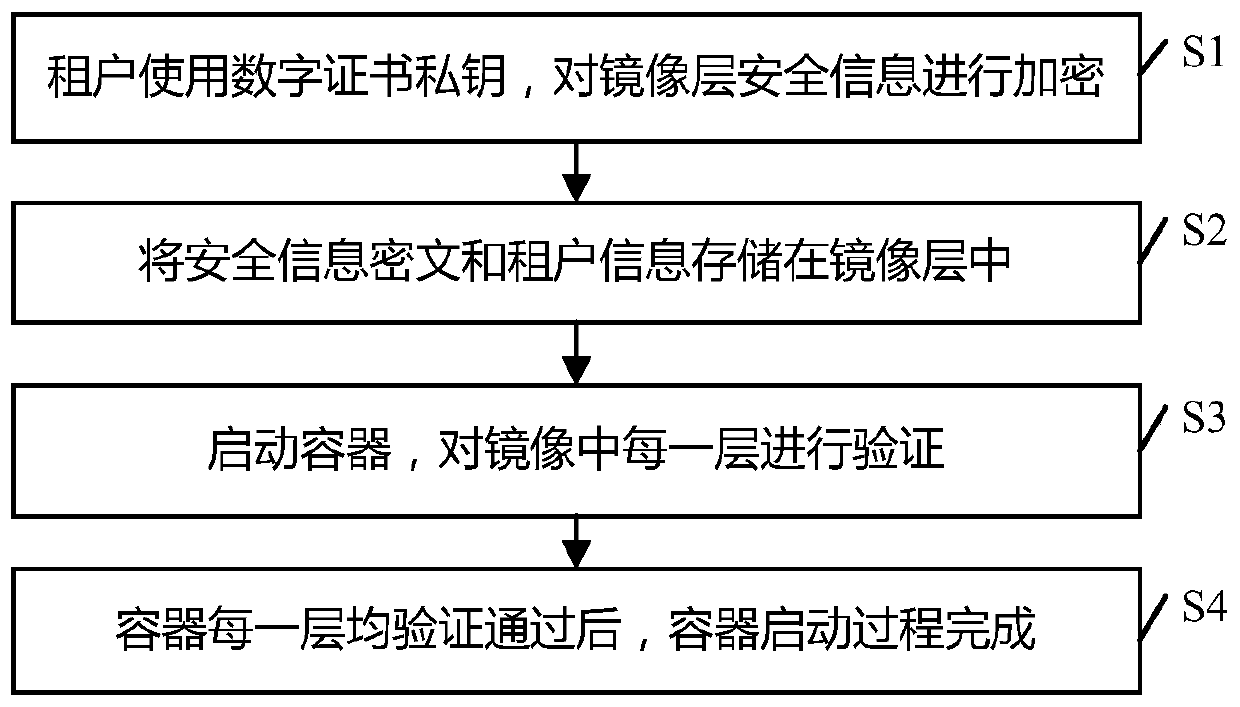
[0055] The present invention provides a multi-tenant-oriented container image security configuration method, such as figure 1 As shown, the methods include:
[0056] S1, the tenant uses the private key of the digital certificate to encrypt the security information of the image layer;
[0057] Tenants can be based on the user end, or the operation end, or the computing node of the system, etc. based on user usage. Tenants are ports used by developers, testers, and operation and maintenance personnel.
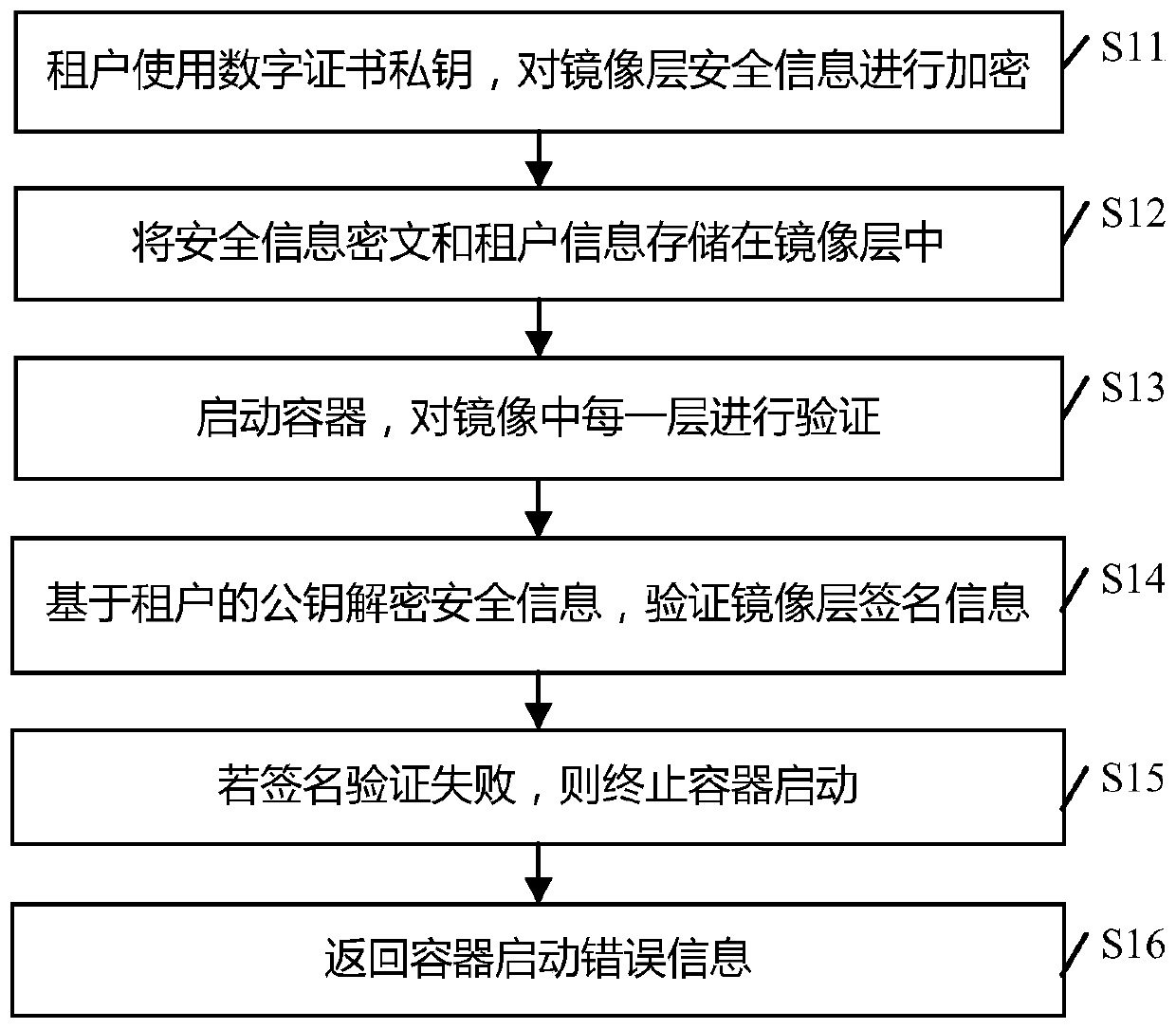
[0058] The system assigns a digital certificate to each tenant based on the cloud computing environment, and the tenant uses the digital certificate to sign;
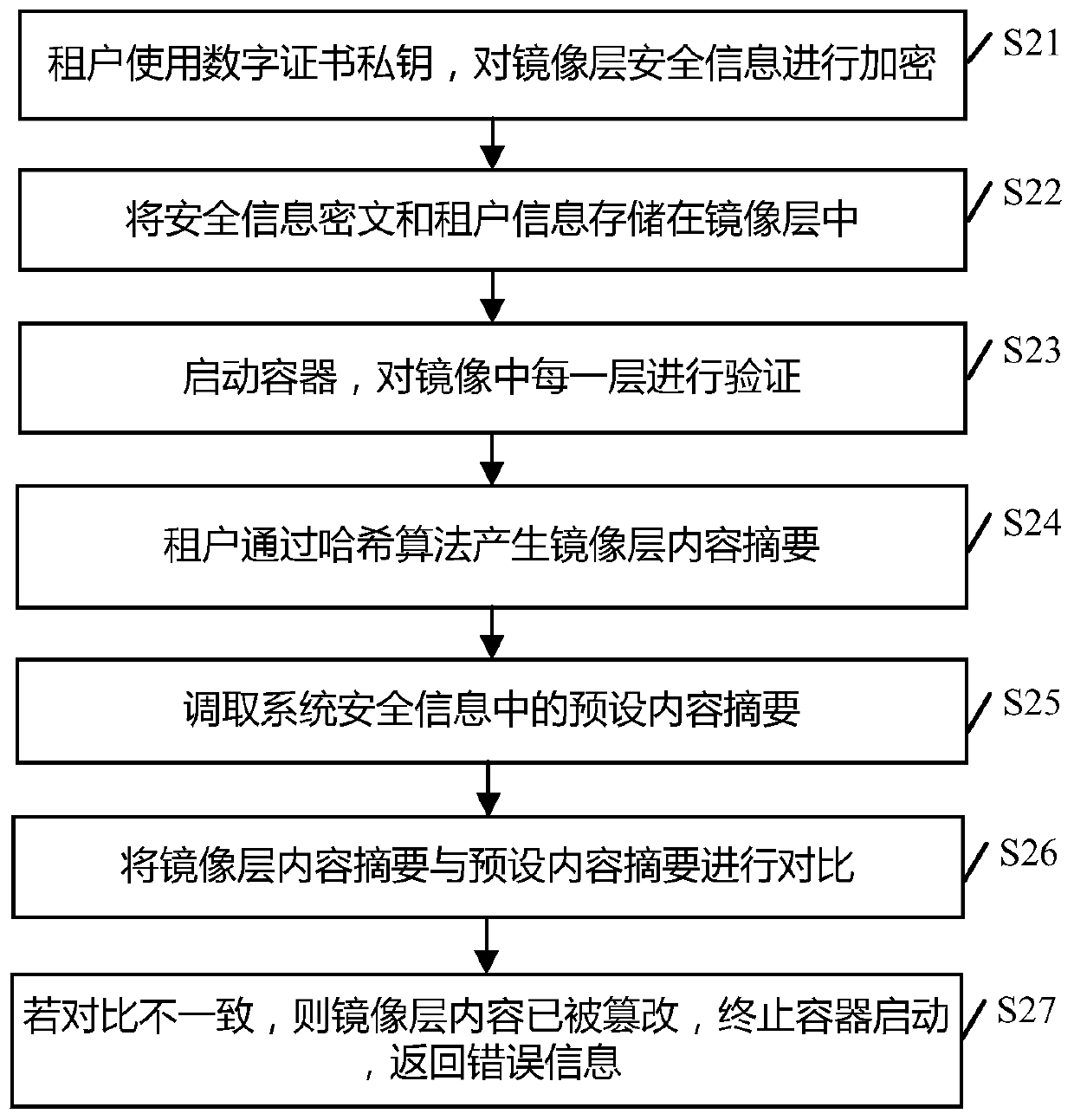
[0059]When a tenant edits or creates a new container image layer, the vulnerability scanning service based on the cloud computing environment scans the content of the container image layer to generate a scan summary; the tenant uses a hash algorithm to calculate the content of the container image layer to generate a cont...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com