Anti-spoofing method for Beidou second-generation system based on elliptic curve algorithm
An algorithm and scheme technology, applied in the field of information security, can solve problems such as poor receivers and influence, and achieve the effects of reduced calculation, high efficiency, and short signature length
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
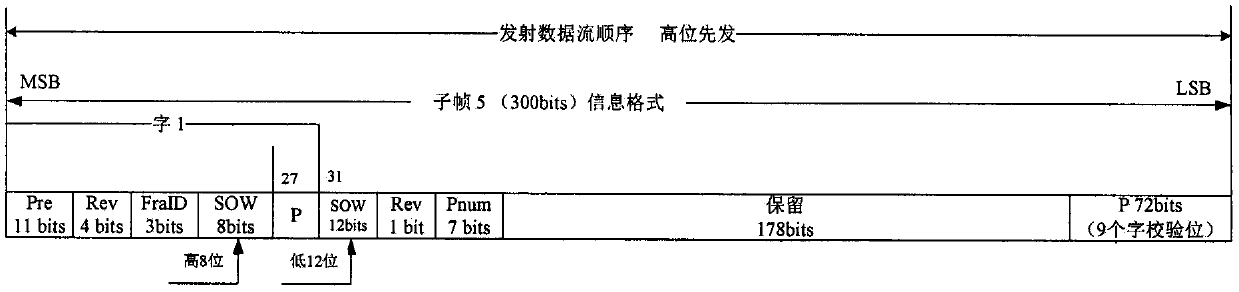
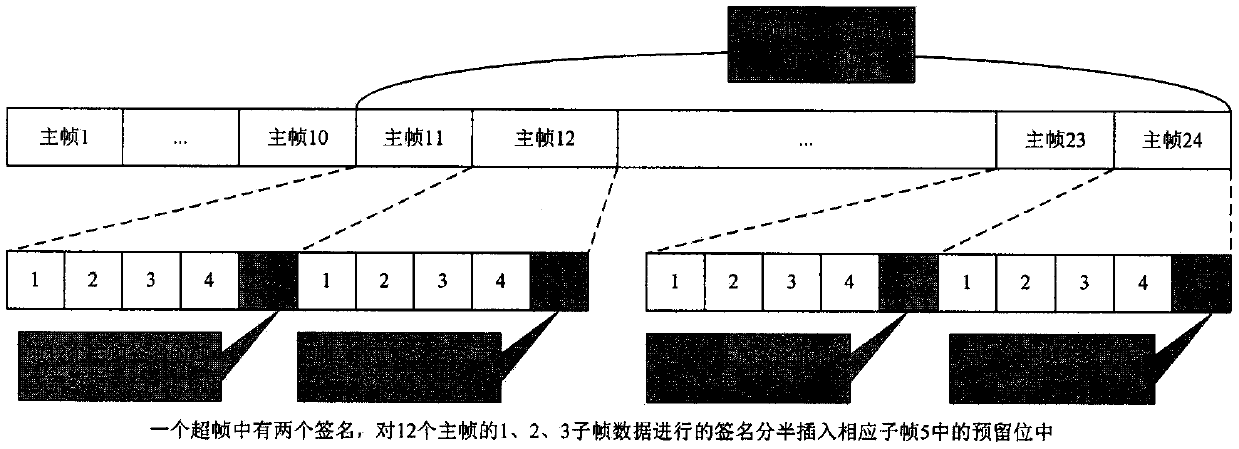
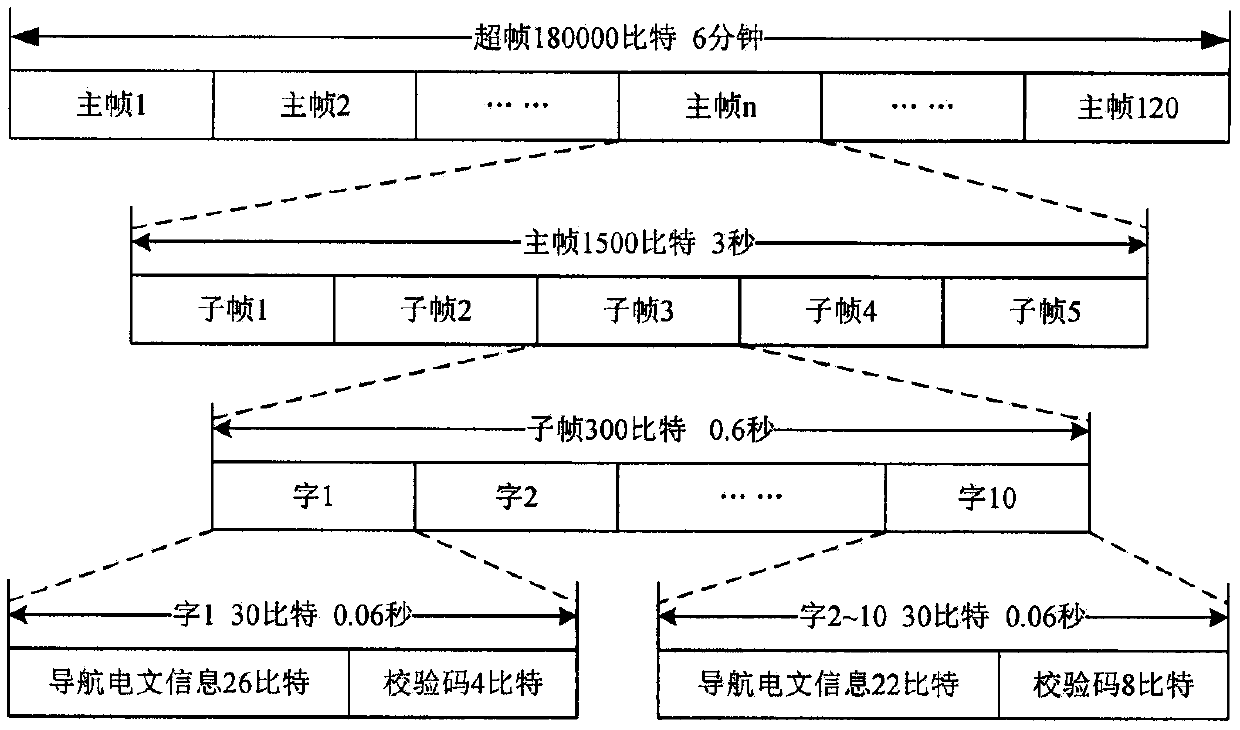
[0050] The scheme of the present invention adopts a simulation experiment, and the entity implementation process is divided into five steps. Firstly, the present invention utilizes a key generation module to generate a private key and a public key; secondly, the signature of the basic navigation message is generated by the private key, and is inserted into the corresponding reserved bit; again, the present invention encodes, interleaves and modulates the navigation message BCH into Satellite signals; the present invention then performs interference with zero-mean Gaussian noise on these signals. When the receiver receives these signals, they are demodulated, deinterleaved and BCH decoded to obtain the navigation message; finally the present invention extracts the signature from the navigation message and passes the public key verification. Specific process such as Figure 10 and Figure 11 shown.
[0051] In the present invention, the elliptic curve used by the ECDSA algori...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com