Secure network establishment method and system based on secure module
A security module and security network technology, which is applied in the field of SE-based security network construction, can solve problems such as high security, higher user knowledge requirements, and insufficient security, so as to reduce operating costs, ensure safe transmission, and reduce the risk of leakage Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
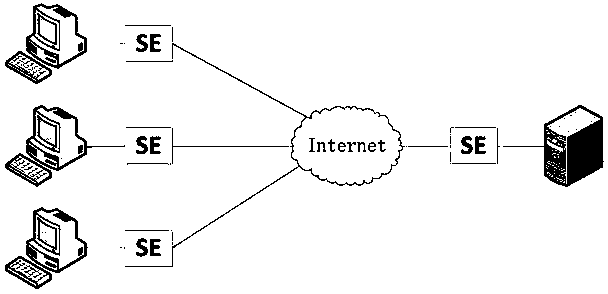
[0038] Such as figure 1 As shown, a security network construction system based on the SE security module includes a client and a server, and the system also includes:
[0039] The security module SE is set between the client / server and the network, and is used to encrypt or decrypt the message data transmitted between the client and the server;
[0040] The distribution module is used to distribute a key to the security module according to the distribution factor.
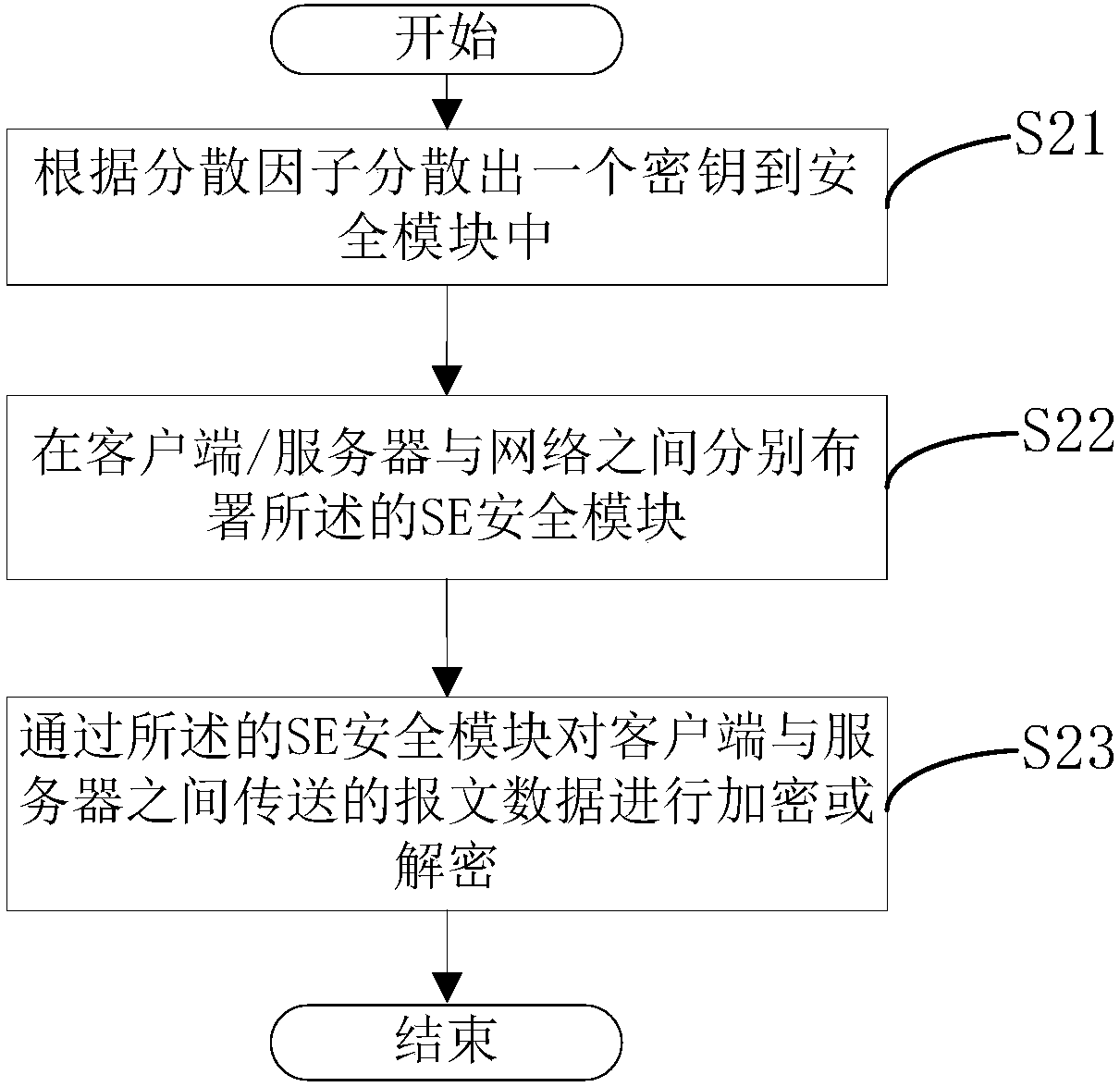
[0041] Such as figure 2 As shown, a method for building a secure network based on a security module includes the following steps:
[0042] (1) disperse a key into the security module according to the dispersal factor, step S21;
[0043] (2) Deploy the security modules respectively between the client / server and the network, step S22;
[0044] (3) Encrypt or decrypt message data transmitted between the client and the server through the security module, step S23.
[0045] In the present embodiment, in step (1), ...
Embodiment 2
[0068] In this embodiment, the IPv4 message before encryption is as follows Figure 5 Shown (refer to rfc791).
[0069] in:
[0070] data is plain text
[0071] After encryption, Total Length and Header Checksum should be modified according to the specification.
[0072] The encrypted message such as Figure 6 shown.
[0073] in:
[0074] 1) The overall structure conforms to international standards (refer to rfc791).
[0075] 2) The Data field contains the following contents: dispersion factor, plaintext length, ciphertext (including plaintext padding characters), signature (optional).
[0076] 3) The value of Total Length is the original plaintext length + dispersion factor length + plaintext padding characters.
[0077] 4) Header Checksum is recalculated with the new value (refer to rfc791).
[0078] It can be seen from the above embodiments that the method and system of the present invention can ensure the security of data in network transmission through the encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com