An http-digest-like aka identity authentication system and method based on a symmetric key pool
An identity authentication and key pool technology, applied in the field of end-to-end authentication and key negotiation, can solve problems such as low security performance, message cracking, encrypted communication security threats, etc., to improve security and complexity, simplify Message verification steps, the effect of reducing the risk of cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0073] Flow Description
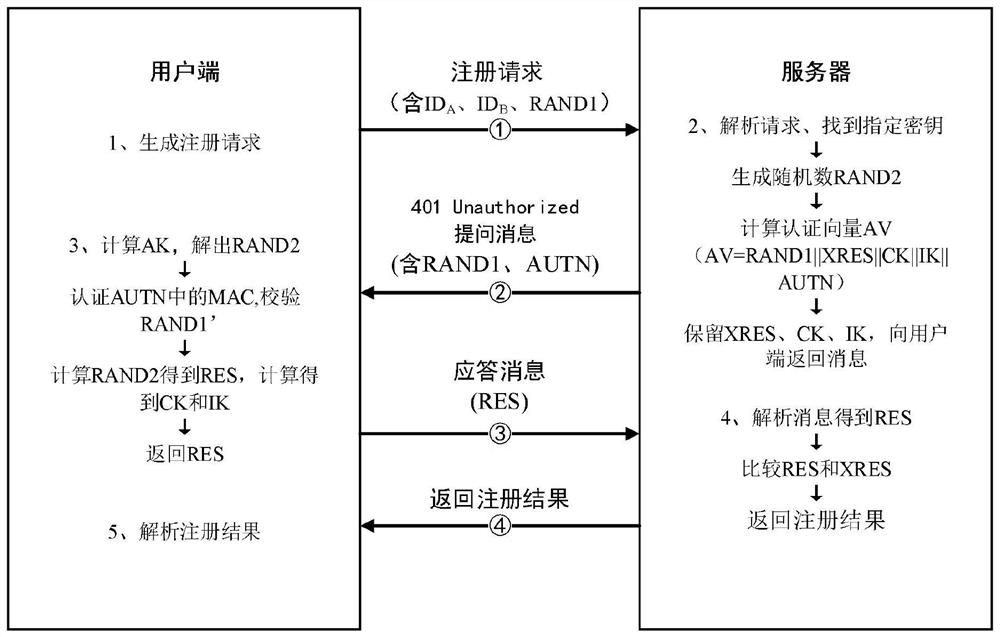
[0074] For the schematic diagram of the registration process in this embodiment, please refer to figure 2 ,include:
[0075] Step 1: The client initiates a registration request
[0076] The client initiates a registration request to the server as needed. The contents of the main header fields and fields are as follows:
[0077] REGISTER sip:home.mobile.biz SIP / 2.0
[0078] Authenticate:Digest
[0079] username="jon.dough@home.mobile.biz",
[0080] realm="home.mobile.biz",
[0081] nonce="",
[0082] uri="sip:home.mobile.biz",
[0083] response="",
[0084] ...
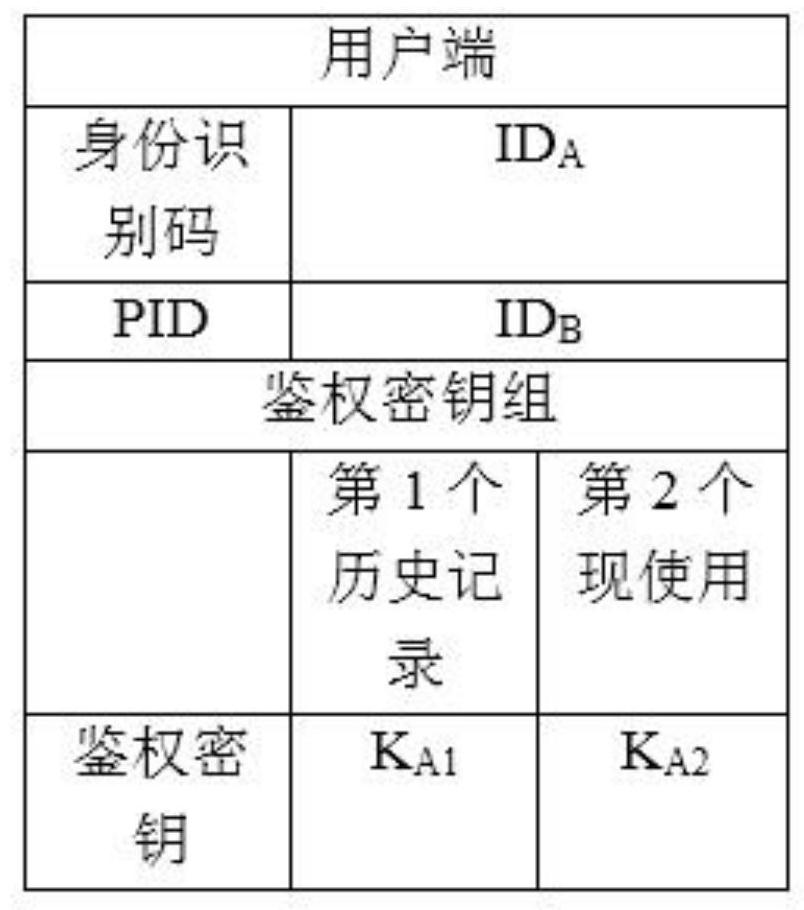
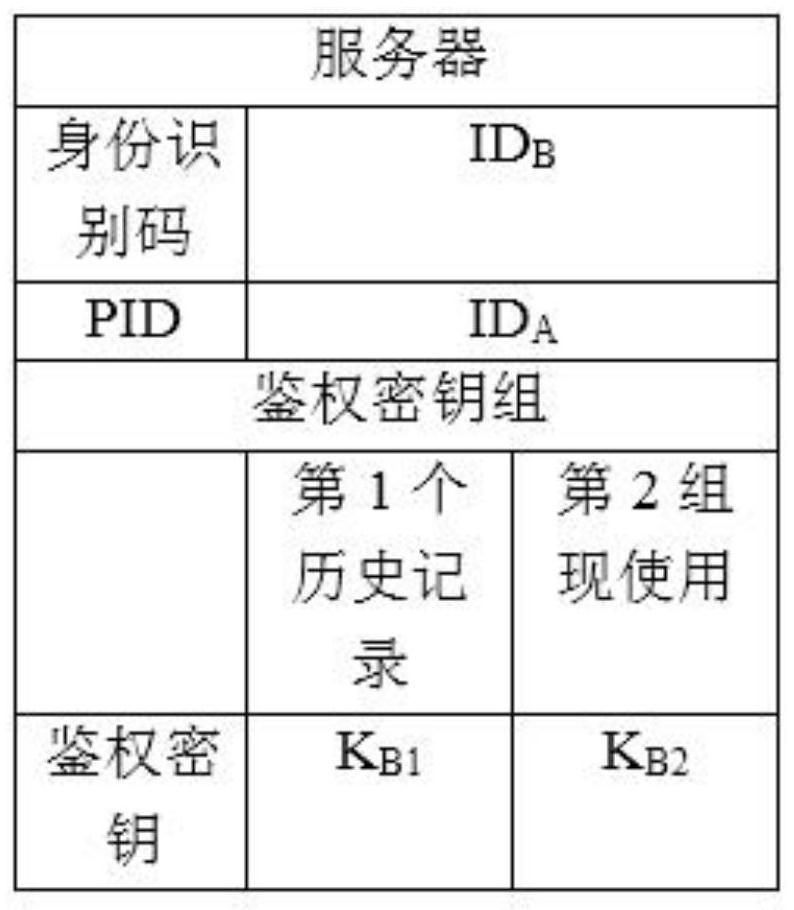
[0085] The values of the "response" and "nonce" fields are both set to null in the initial Registration Request message. This request contains the ID of the client A and the server's ID B And a random number RAND1 generated by the client, which has the function of this message identifier.
[0086] The random number RAND1 is preferably a quantum random number generated by a quan...
Embodiment 2
[0153] Flow Description
[0154] For the schematic diagram of the registration process in this embodiment, please refer to image 3 . The difference from Embodiment 1 lies in the way of generating the authentication response. include:
[0155] Step 1: The client initiates a registration request
[0156] The client initiates a registration request to the server as needed. The contents of the main header fields and fields are as follows:
[0157] REGISTER sip:home.mobile.biz SIP / 2.0
[0158] Authenticate:Digest
[0159] username="jon.dough@home.mobile.biz",
[0160] realm="home.mobile.biz",
[0161] nonce="",
[0162] uri="sip:home.mobile.biz",
[0163] response="",
[0164] ...
[0165] The values of the "response" and "nonce" fields are both set to null in the initial Registration Request message. This request contains the ID of the client A and the server's ID B And a random number RAND1 generated by the client, which has the function of this message identifie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com