General purpose computation, trusted computation and cryptographic computation integrated safety processor
A security processor, trusted computing technology, applied in computer security devices, computing, electrical digital data processing and other directions, can solve the problems of low reliability, reverse engineering attacks, weak security, etc., to achieve efficient transmission, defense against physical attacks , the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
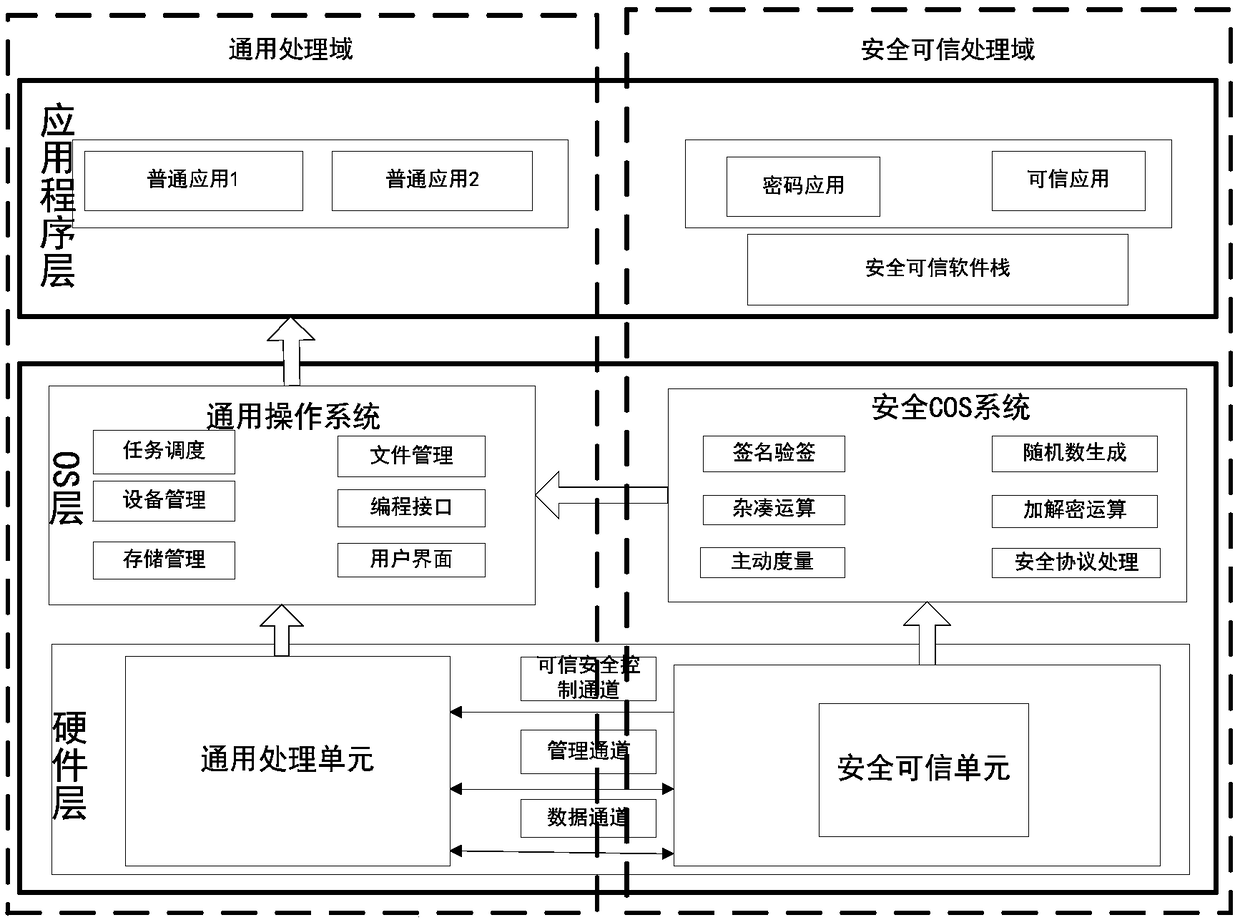
[0020] A security processor that integrates general computing, trusted computing, and cryptographic computing. The overall architecture is as follows: figure 1 Shown:
[0021] (1) Overall structure
[0022] The overall architecture of the integrated security processor is divided into two domains, the general processing domain and the secure and trusted processing domain, which are divided into three layers from top to bottom, namely the hardware layer, OS layer, and application layer, such as figure 1 shown.
[0023] (a) Hardware layer
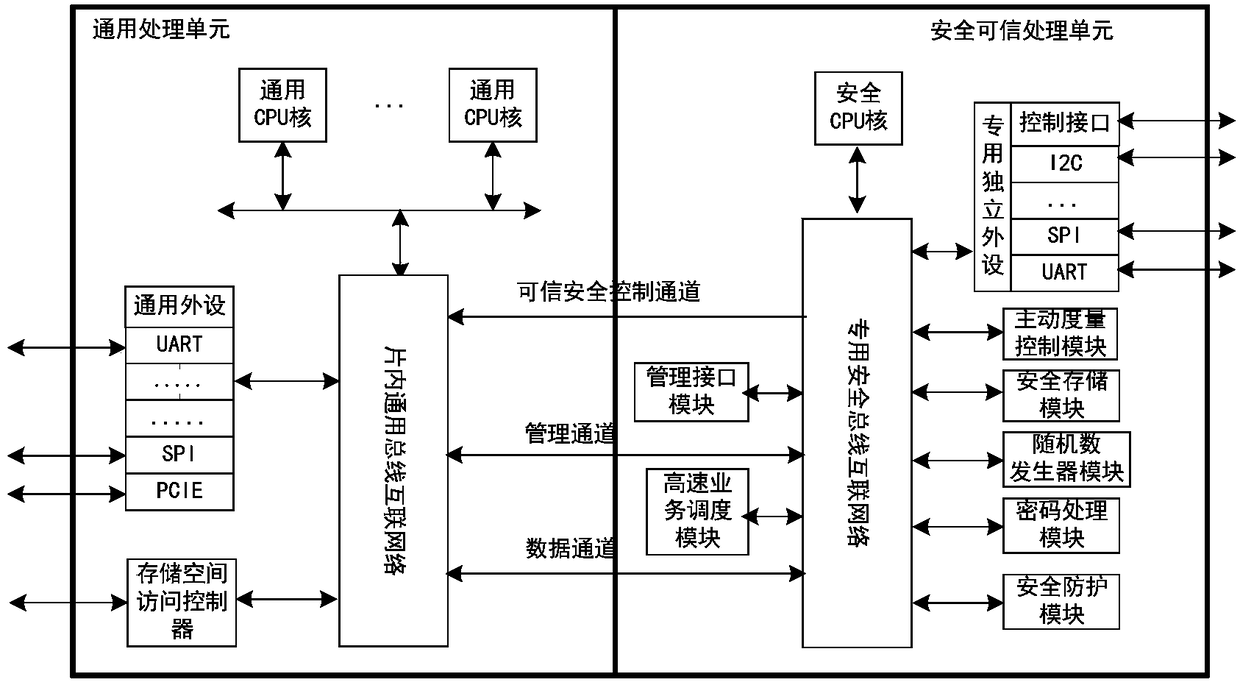
[0024] The hardware layer mainly includes a general-purpose processing unit and a security and trustworthy unit, which realize data interaction through data channels, management channels, and trusted security control channels.
[0025] A data channel, which is a dedicated channel for the safe and trusted unit to process high-speed data. The input and output data of the secure and trusted unit in the process of trusted computing and cryptog...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com