Automatic malicious code variation detection method
A malicious code and detection method technology, applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve the problem of increasing the time consumption of malicious code detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
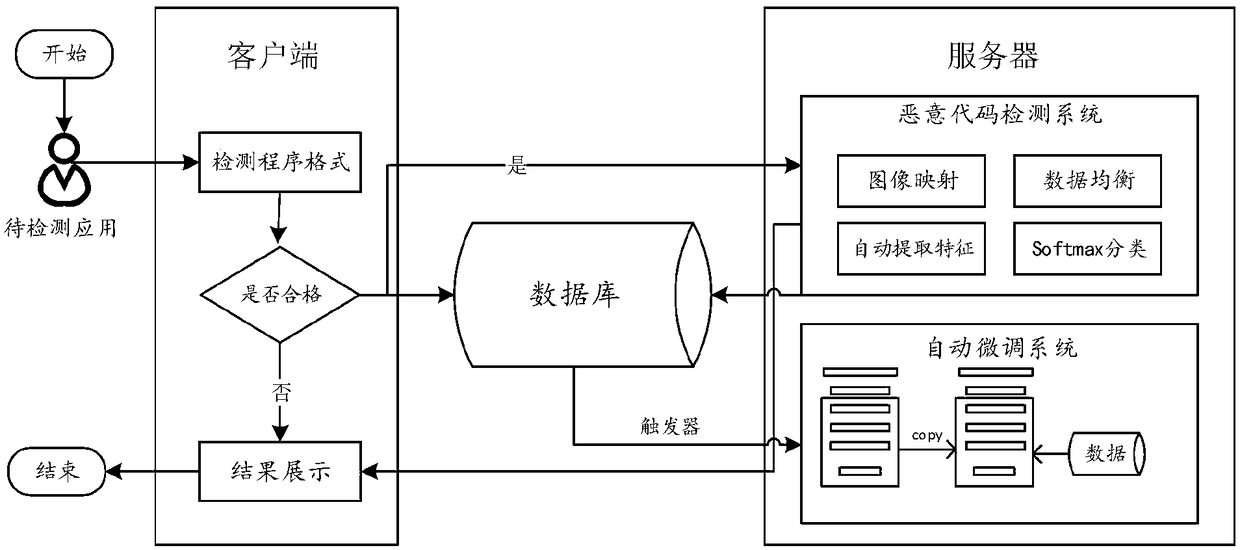
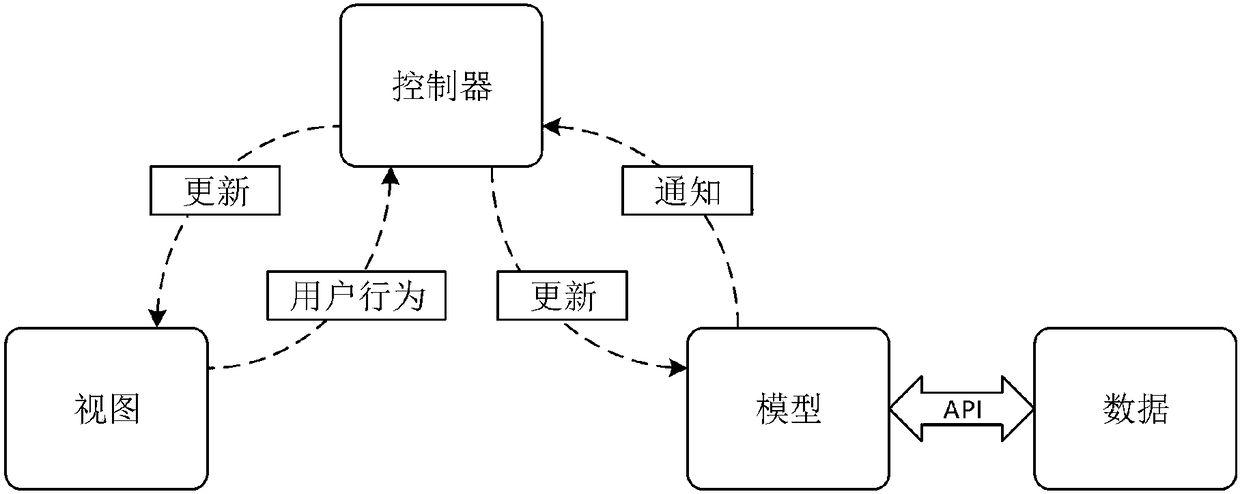
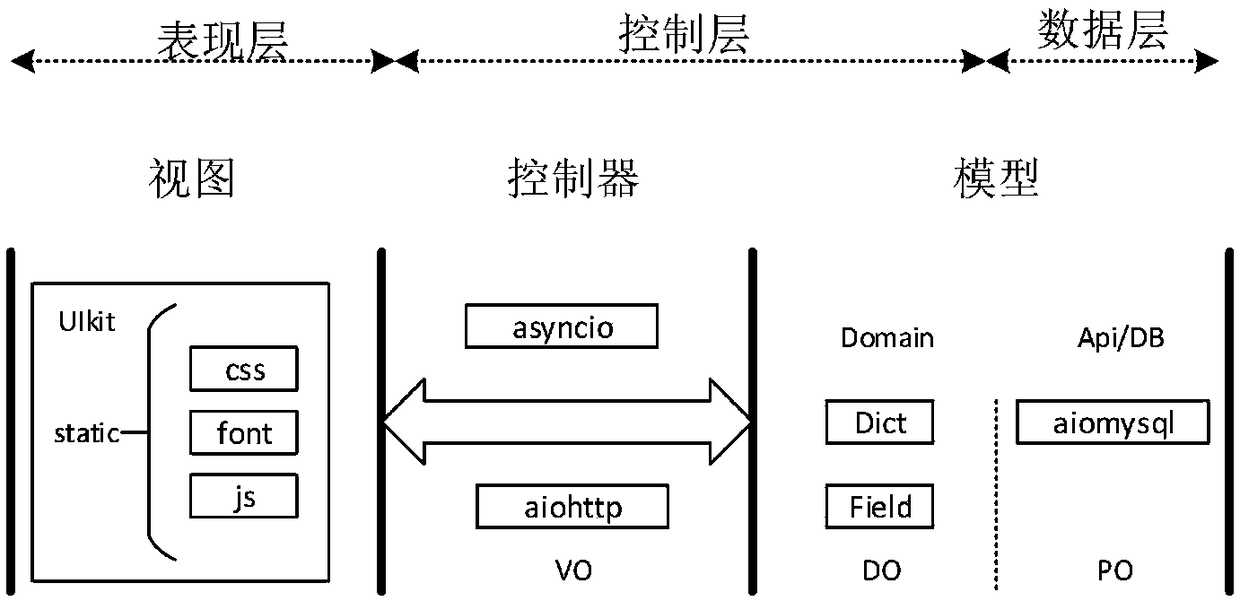
[0034] This section will introduce the specific embodiment of the present invention in detail. The implementation environment is ubuntu14.04 host, 8G memory, 1T hard disk. The development environment is python 3.5.3, the background database uses Mysql database, and the detection model used by the malicious code variant detection system is a model trained by using the malicious code variant detection method based on deep learning. The design pattern of the malicious code variant detection system adopts the MVC model, and the specific design pattern implementation diagram is as follows figure 2 shown.
[0035] MVC is a software design paradigm. It uses a method of separating business logic, data, and interface display to organize code, and gathers many business logics into one component. When it is necessary to improve and customize the interface and user interaction, it does not need to rewrite the business logic. , to reduce the encoding time. The emergence of MVC not onl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com