A Group Key Agreement Method Based on Symmetric Cryptography
A technology of group key negotiation and symmetric cipher, applied in the field of group key negotiation, it can solve the problems of unaffordable special network, large computing and communication resources, limited capacity, etc., achieving fast encryption and decryption speed and high communication efficiency , the effect of reducing the consumption of resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
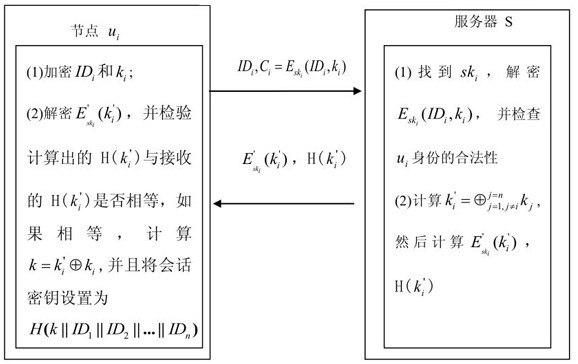
[0058] Embodiment one, such as figure 1 As shown, a group key agreement method based on the DES symmetric encryption algorithm establishes a session key among n communication nodes u with the assistance of a server S, and does not need to confirm the key. Each communication node u i (1≤i≤n) has an identity information ID i (1≤i≤n), each communication node u i A shared key sk shared with the server S is preset i (1≤i≤n); the communication node u is stored in the server S i with the shared secret sk i and identity information ID i mapping table.
[0059] Specific steps include:
[0060] Step 1. All communication nodes u send authentication information to the same server S;
[0061] Step 2. The server S receives the authentication information, and then authenticates all communication nodes u according to the authentication information;
[0062] Step 3. After the server S authenticates all communication nodes u, it broadcasts verification information to all communication ...
Embodiment 2
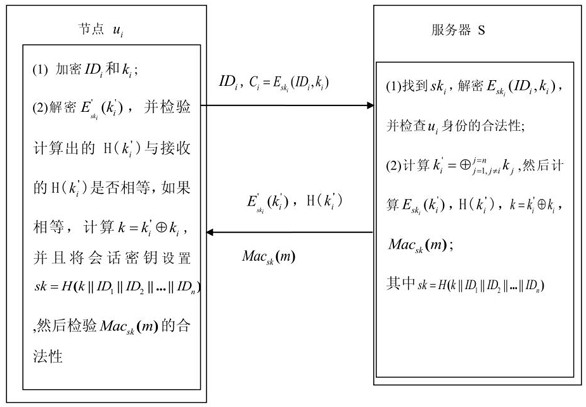
[0086] Embodiment two, such as figure 2 As shown, a group key agreement method based on the AES symmetric encryption algorithm establishes a session key among n communication nodes u with the assistance of a server S, and does not need to confirm the key.
[0087] The specific process of step 1 and step 2 is the same as that of the first embodiment.
[0088] The concrete process of described step 3 comprises:
[0089] Step 3.1B, server S calculates
[0090]
[0091]
[0092] sk=H(k||ID 1 ||ID 2 ||...||ID n );
[0093] Step 3.2B, server S according to k' i calculate and H(k′ i ),in is server S using communication node u i The shared secret key sk i and encryption algorithm E' to k' i Obtained after encryption, H represents the hash algorithm;
[0094] Step 3.3B, server S uses sk as the key to encrypt a communication data m using CBC mode to generate the authentication code Mac sk (m), the method of generation can be the method of the hash function cluster...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com