A monitoring system identity authentication method for mobile cloud computing
A monitoring system and identity authentication technology, applied in the field of network security, can solve problems such as hidden dangers and inability to provide reliable security guarantees, and achieve the effects of high security, low overhead, and small storage space.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
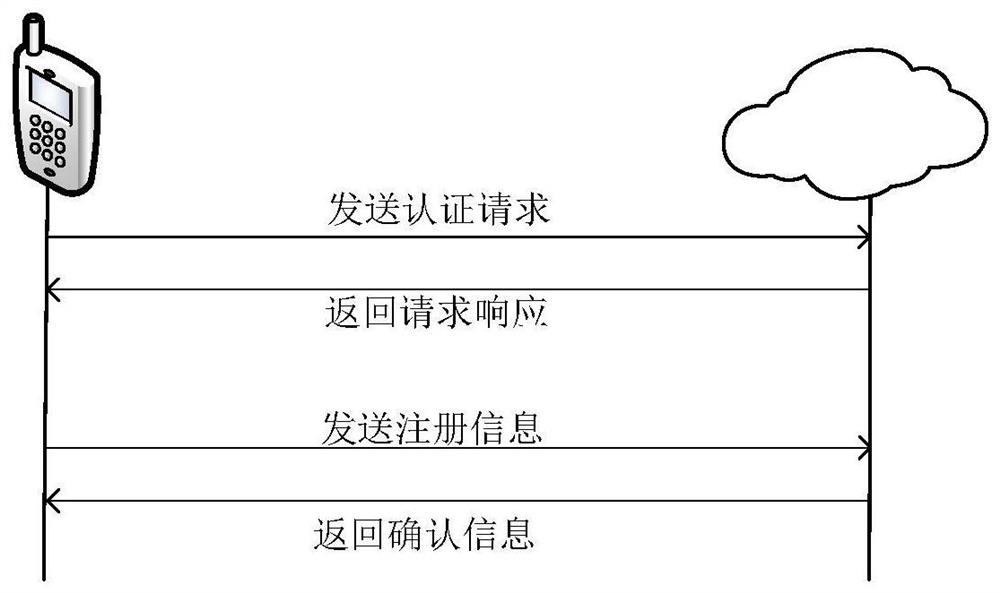
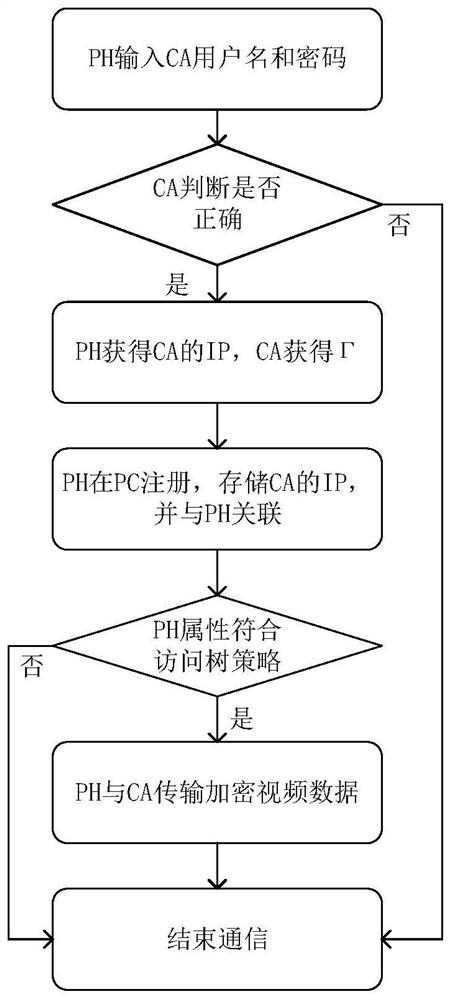
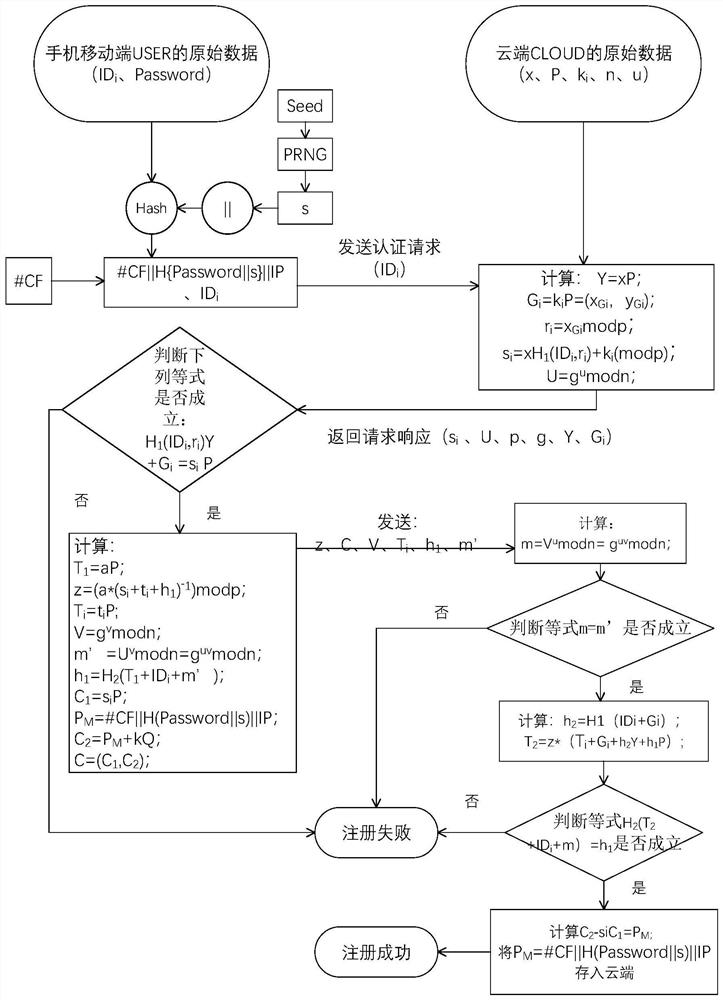
[0055] Such as Figure 1-4 As shown, a mobile cloud computing monitoring system identity authentication method, using the elliptic curve algorithm to design the authentication method, encrypts the user, the authentication method is used as a signature algorithm, and uses the Diffie–Hellman protocol to encrypt a random parameter at the same time, As a fresh value, it prevents replay attacks; the entities involved in this scheme are the cloud, mobile users, and cameras.
[0056] The Diffie-Hellman algorithm is a public key key exchange algorithm based on the difficulty of solving discrete logarithms, which can securely exchange encrypted keys on an insecure channel. Before this method appeared, both communicating parties needed to share the key through a secure channel, or a third party distributed the key, but now the commonly used channels are untrustworthy in the eyes of users, and the introduction of a trusted third party also needs to increase the communication cost. The D...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com