A lightweight RFID mutual authentication method on elliptic curves
An elliptic curve, mutual authentication technology, applied in the field of RFID mutual authentication technology, can solve problems such as label information privacy, achieve the effect of protecting identity information and realizing mutual authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
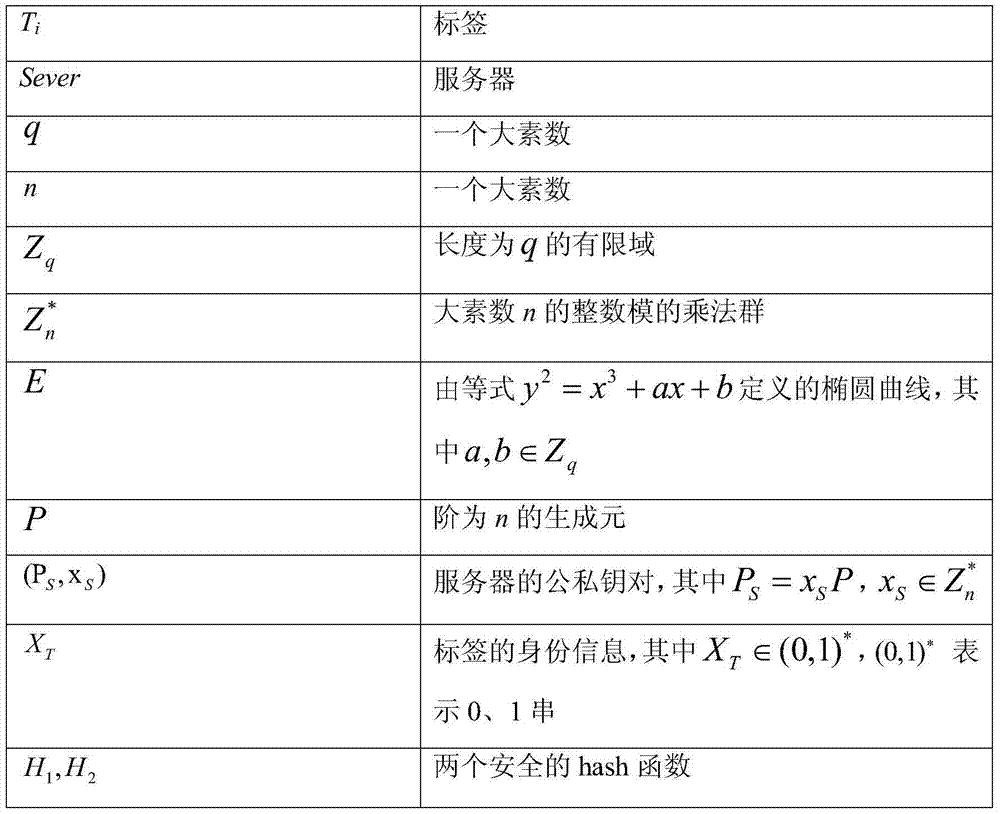
[0020] The symbols used in the implementation are described in the table below:
[0021]
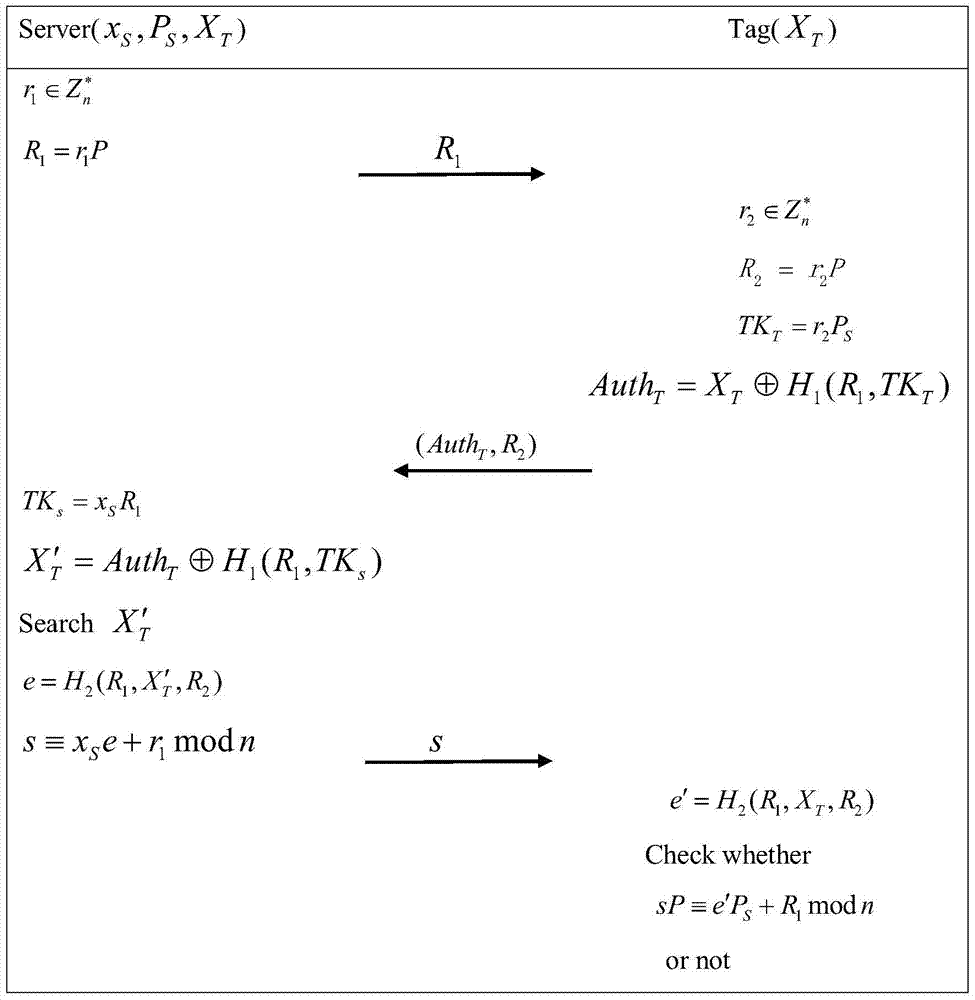
[0022] In this scheme, there is no trusted third party as the issuing institution. Only server, reader and tag. The server generates the public-private key pair of the reader and the tag. Furthermore, the communication channel between reader and server is secure. So in this solution, we write the communication between the tag and the reader as the communication between the tag and the server.
[0023] (1) System initialization: the server generates its public-private key pair, tag identity information and two secure hash functions. The identity list of all legal labels is stored in the server.
[0024] The server chooses q, n two large prime numbers, and two hash functions H 1 with H 2 , an n-order generator P;
[0025] The server determines the elliptic curve E to be y 2 =x 3 +ax+b, where the elliptic curve constant a,b∈Z q ,Z q is a finite field of length q;
[0026] The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com