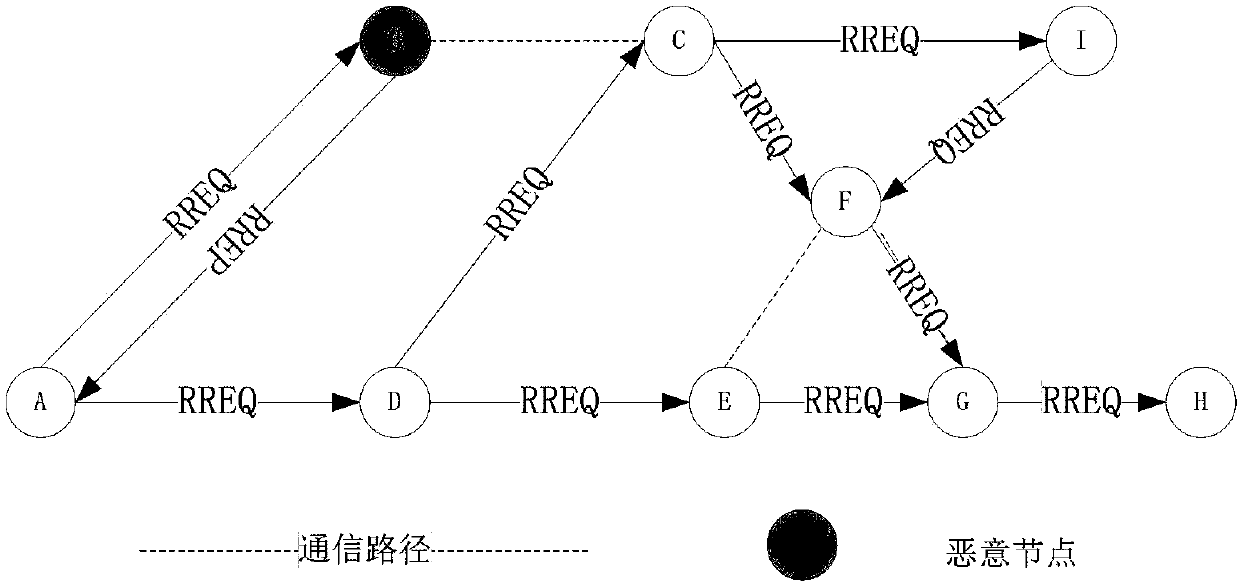
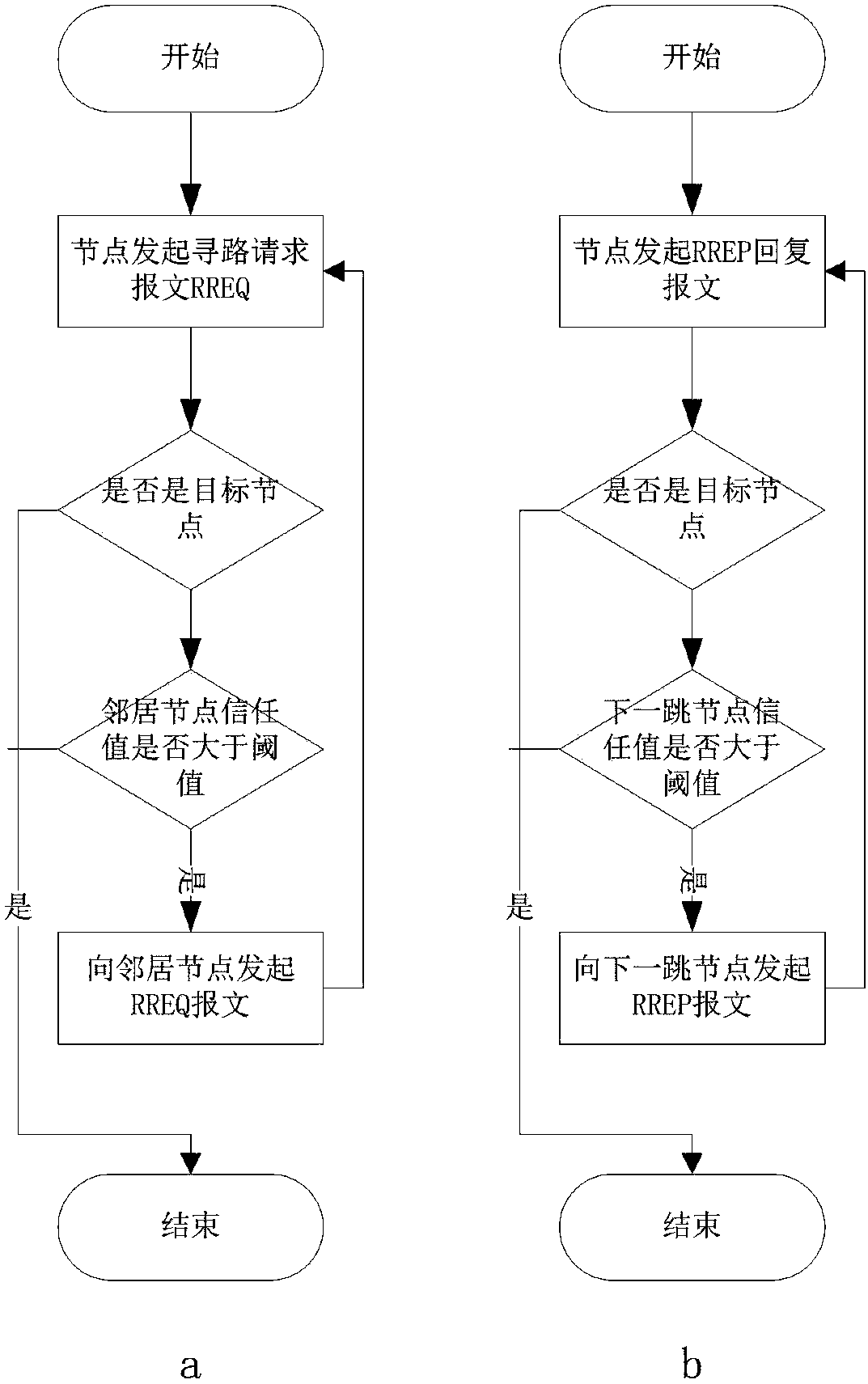
Ad Hoc network security trust method based on reference node strategy
A network security and reference node technology, which is applied in the field of AdHoc network security trust based on reference node strategy, can solve problems that cannot be solved fundamentally, the effect of message attack defense is not obvious, and the defense model has a single attack mode, etc. Achieve good defense effect, strong scalability and adaptability, and defense against various attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0072] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
[0073] The present invention comprises the following steps:
[0074] Step 1: Build a trust model
[0075] 1. Packet statistics strategy based on direct trust model
[0076] Direct trust (Direct_Trust) refers to the trust relationship obtained by nodes collecting communication packet loss rate information through a strategy based on packet statistics and evaluating through the Bayesian trust model. The evaluation of Bayesian trust model is to calculate the trust value of nodes in a probabilistic way according to the communication result set of observed nodes. The Bayesian model under direct trust evaluation is described as follows: the destination node collects message information through a strategy based on message statistics, and calculates the message loss rate. times; if the packet loss rate of the node is normal, then α=a+1, and if t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com