Threat intelligence response and disposal method and system based on virtual machine introspection
A processing method and virtual machine technology, applied in the information field, can solve problems such as security software attacks, poor protection efficiency, and high maintenance costs, and achieve fine-grained detection, easy maintenance, and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] Embodiments of the present invention will be described in further detail below in conjunction with the accompanying drawings.
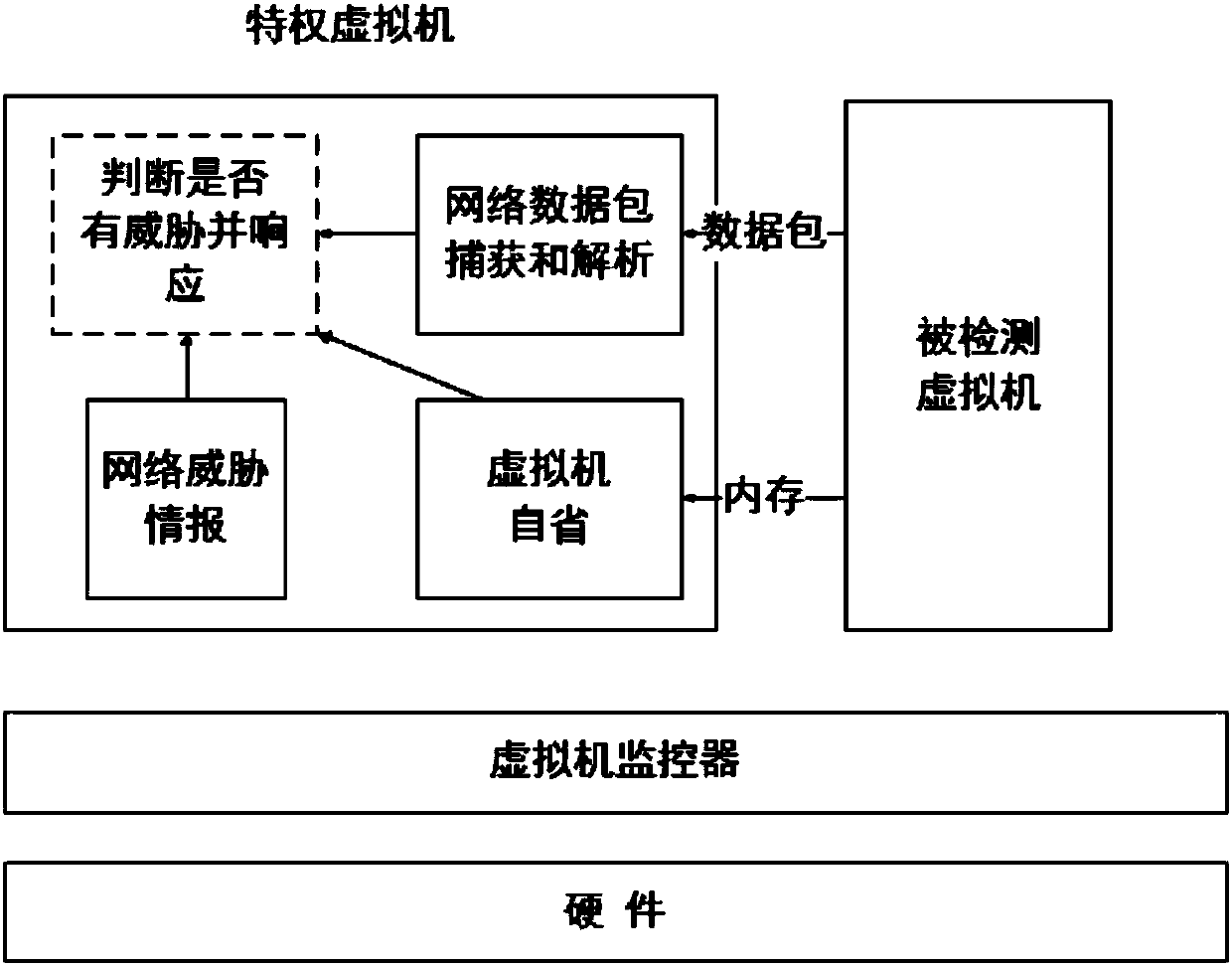
[0036] The threat intelligence response and disposal based on the introspection of the virtual machine in the present invention is realized on the framework shown in the accompanying drawing. Using the virtual machine introspection technology, the threat detection and response module is installed outside the detected virtual machine, completely transparent to the detected virtual machine. The present invention does not make any changes to the existing cloud architecture, and only uses the interface provided by the virtual machine monitor to simultaneously detect and respond to network threats on multiple virtual machines on the virtual machine monitor.
[0037] The threat intelligence response and processing method of the present invention includes the following steps:
[0038] Step 1. Deploy the threat detection and response module on a privi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com