Identity information processing method, system and corresponding server
An information processing method and identity information technology, applied in the field of identity information processing methods, systems and their corresponding servers, can solve the problems of user privacy leakage, inability to be widely used, and citizens' low awareness of eID, and achieve privacy protection, The effect of improving authenticity and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
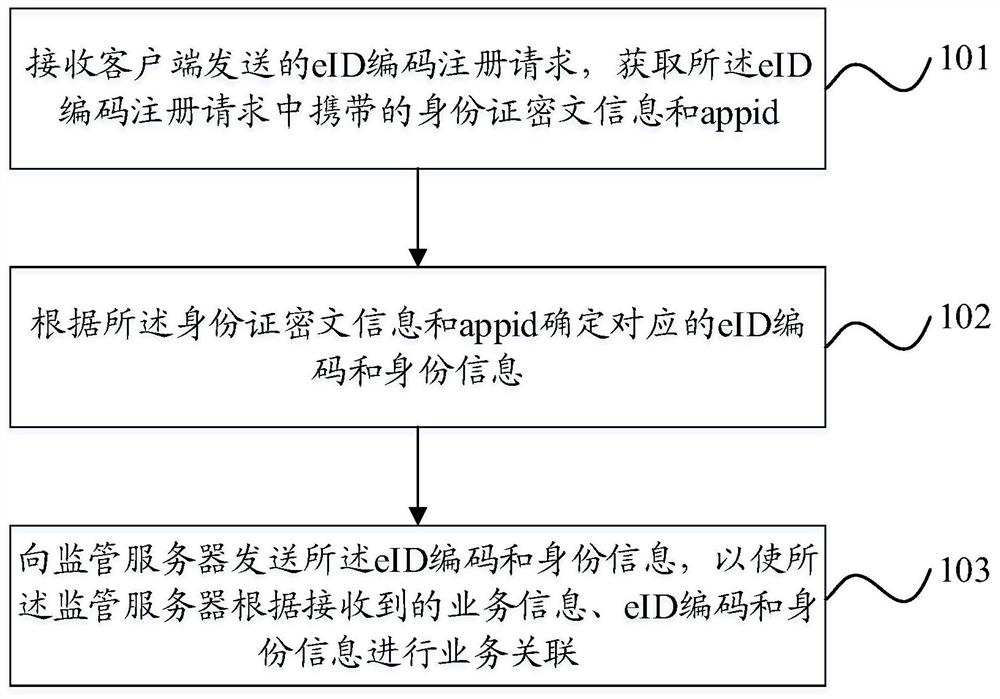
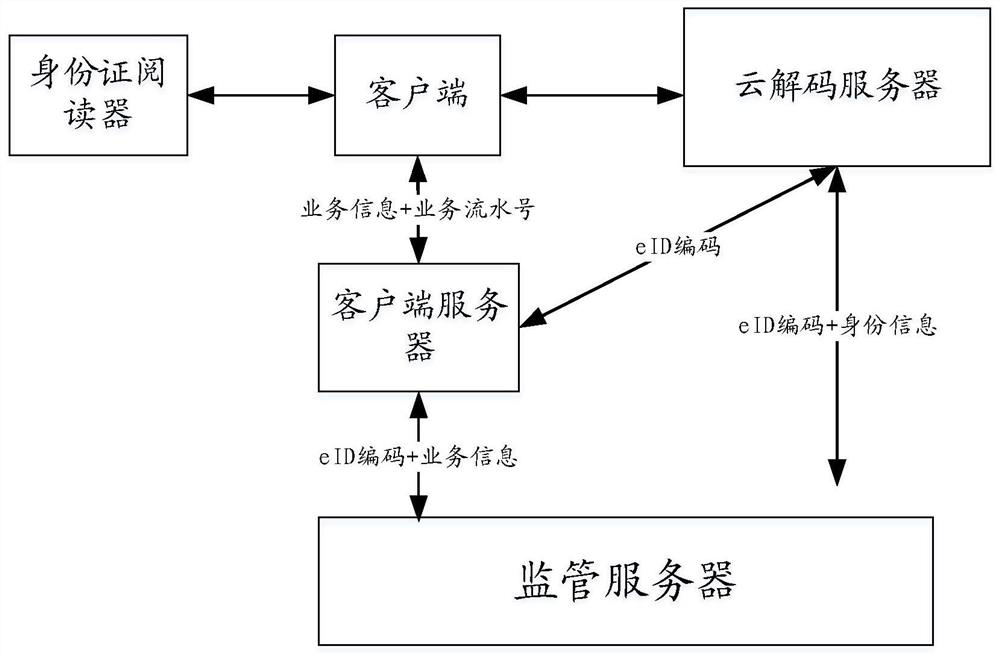
[0129] In this example, if Figure 3-4 As shown, it is a schematic diagram of the overall architecture relationship and business process steps of this embodiment, including the following steps:
[0130] Wherein, the cloud decoding server assigns an application ID (appid) to the client in advance; the cloud decoding server provides the client with a business serial number generation rule.
[0131] 1. The ID card reader detects that there is an ID card that can be read;
[0132] 2. The client requests the cloud decoding server to obtain the card reading instruction and receives the returned card reading instruction;
[0133] 3. The client sends the card reading command to the ID card reader to read the ID card information;
[0134] 4. The ID card reader sends the read undecoded ID card ciphertext information to the client, and the client sends the pre-assigned appid and received undecoded ID card ciphertext information to the cloud decoding server;
[0135] Among them, the ab...
Embodiment 2
[0143] In this example, if Figure 5-6 As shown, it is a schematic diagram of the overall architecture relationship and business process steps of this embodiment, including the following steps:
[0144] Wherein, the cloud decoding server assigns an application number (appid) to the client in advance.
[0145] 1. The ID card reader detects that there is an ID card that can be read;
[0146] 2. The client requests the cloud decoding server to obtain the card reading instruction and receives the returned card reading instruction;
[0147] 3. The client sends the card reading command to the ID card reader to read the ID card information;
[0148] 4. The ID card reader sends the read undecoded ID card ciphertext information to the client, and the client sends the pre-assigned appid and received undecoded ID card ciphertext information to the cloud decoding server;
[0149] Among them, the above 2-4 process needs to be executed multiple times, so as to complete the information co...
Embodiment 3
[0156] In this example, if Figure 7-8 As shown, it is a schematic diagram of the overall architecture relationship and business process steps of this embodiment, including the following steps:
[0157] Wherein, the cloud decoding server assigns an application number (appid) to the client in advance.
[0158] 1. The ID card reader detects that there is an ID card that can be read;
[0159] 2. The client requests the cloud decoding server to obtain the card reading instruction and receives the returned card reading instruction;
[0160] 3. The client sends the card reading command to the ID card reader to read the ID card information;
[0161] 4. The ID card reader sends the read undecoded ID card ciphertext information to the client, and the client sends the pre-assigned appid, received undecoded ID card ciphertext information and business information to Cloud Decoding server;
[0162] Among them, the above 2-4 process needs to be executed multiple times, so as to complete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com