A wireless generation method of rfid key based on rabin encryption
A key generation and key technology, which is applied in the field of radio frequency identification, can solve problems such as easy leakage of shared keys, and achieve the effects of avoiding security problems, resisting replay attacks, and enhancing confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
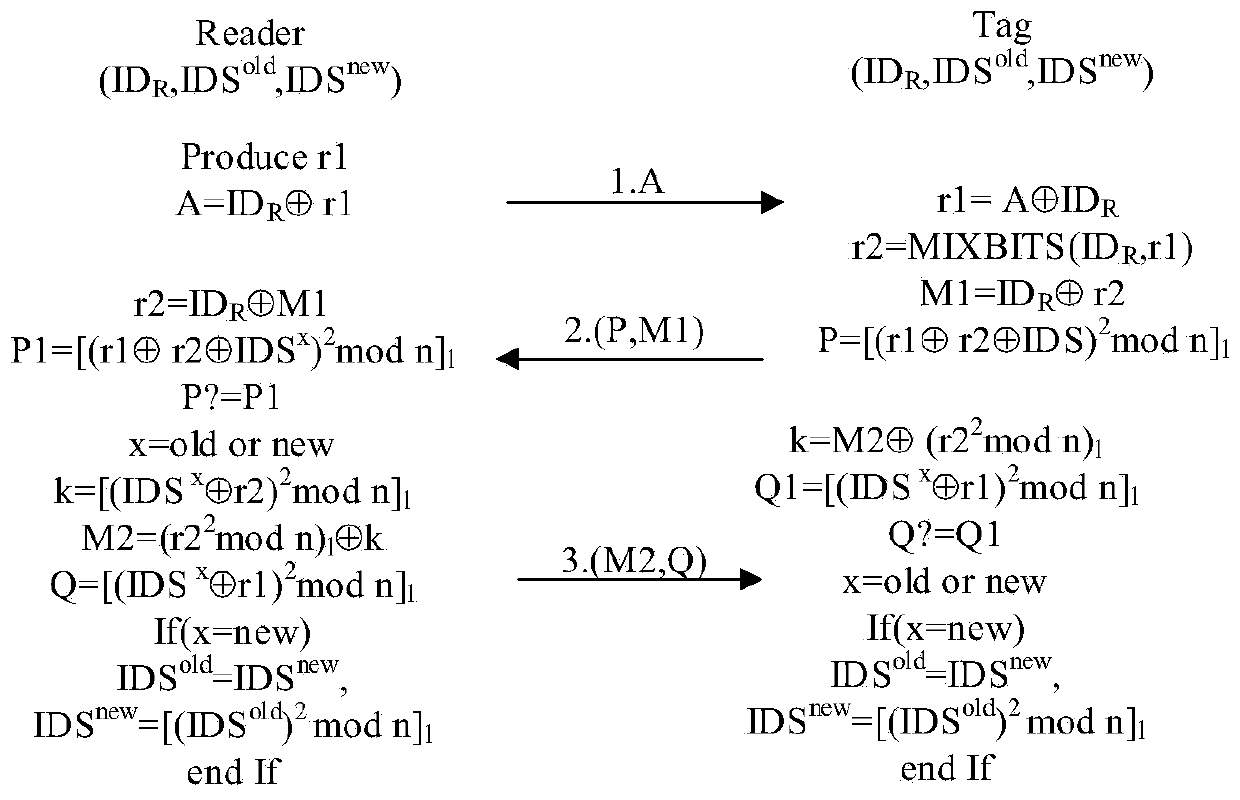
[0051] Generating a key for a single tag is a practical application scenario type: the reader generates a shared key for a single tag, that is, a single tag key generation. The single label key generation process is as follows:
[0052] (1) The reader-writer pre-generates the first random number r1, combined with the reader-writer ID R Generate encrypted information and send message A to said tag;
[0053] (2) After the tag receives the message A, based on the stored reader ID R The first random number can be obtained Utilize the MIXBITS function to generate the second random number r2=MIXBITS(ID R ,r1), combined with the reader ID R Generate encrypted information And use Rabin encryption to generate the first verification information And send the message combination one (P, M1) to the reader;
[0054] (3) After the reader / writer receives the message combination one (P, M1), it combines the ID stored by itself R get the second random number Based on the tag ps...
Embodiment 2
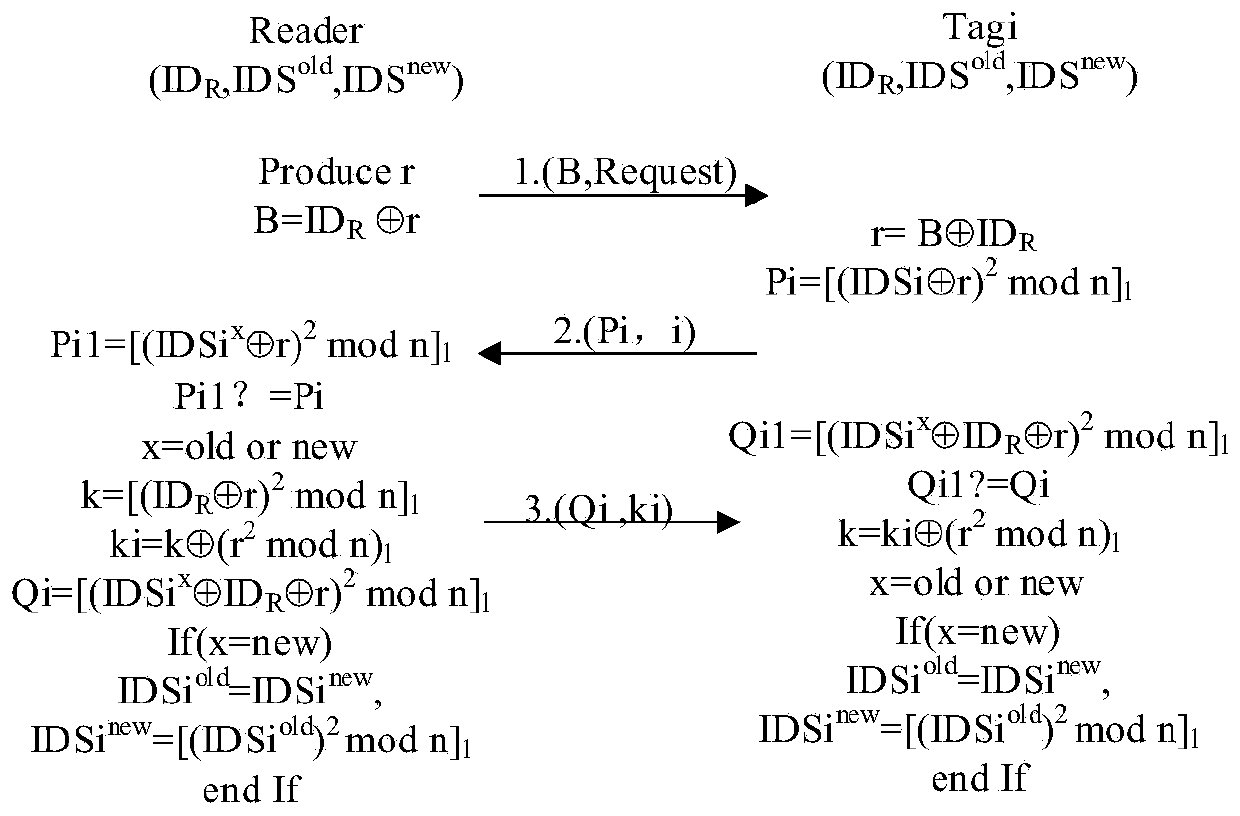
[0057] Generating a unique shared key for a group of tags This type of application scenario: the reader generates a unique shared group key for a group of tags at the same time, that is: group key generation. The group key generation process is as follows:
[0058] (1) The reader generates a random number r in advance, combined with its own ID R Generate encrypted information And broadcast a "key generation request Request" and information B to the whole group of tags to notify all tags to start group key generation;
[0059] (2) After the tag in the group receives the message combination four (B, Request), it combines the stored reader ID R Can get random number And calculate the sixth verification information And send the message combination five (Pi, i) to the reader;
[0060] (3) After the reader-writer receives the message combination five (Pi, i), based on the i-th tag pseudonym IDSi stored in the reader-writer new Or the previous round of label pseudonym IDSi ...
Embodiment 3
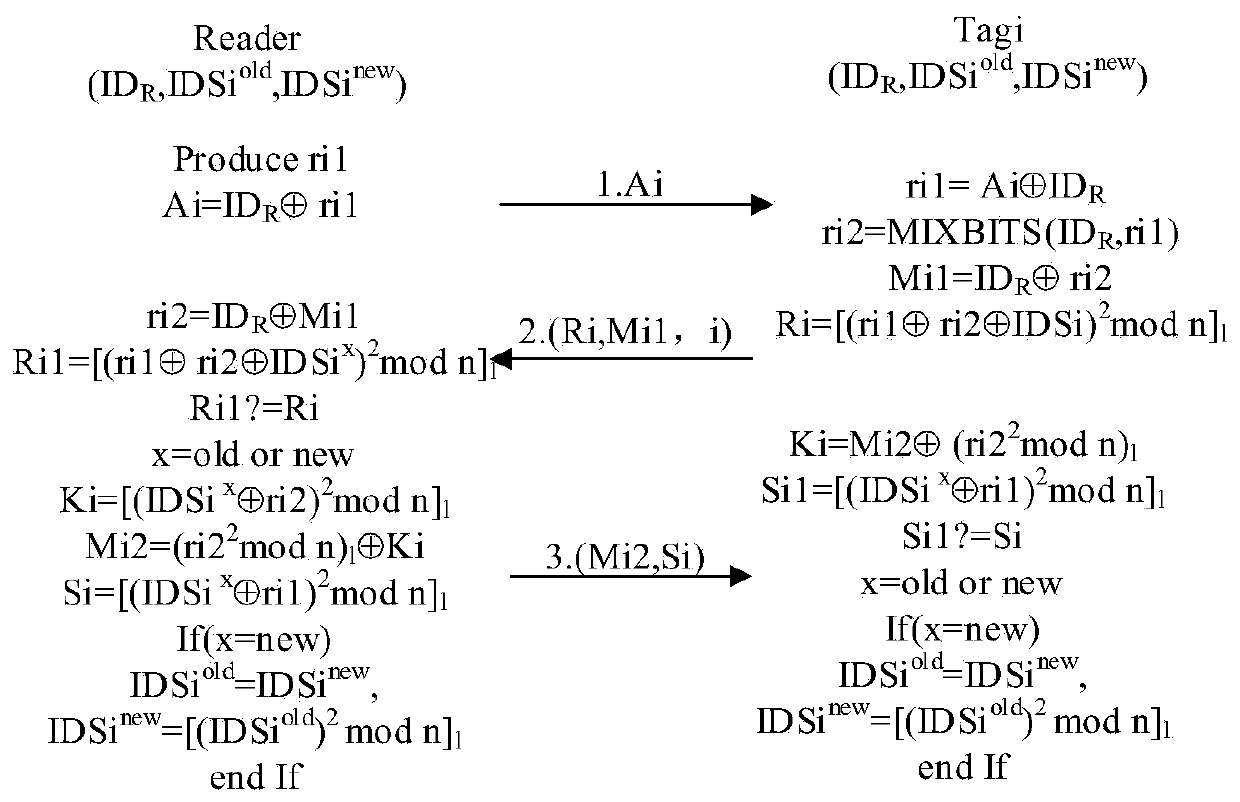
[0063] The application scenario of generating keys simultaneously and independently for a large number of different tags: the reader generates individual keys for a large number of different tags simultaneously and independently, that is: batch key generation. The batch key generation process is as follows:
[0064] (1) The reader-writer generates a random number ri1 for the batch tags in advance, and combines the reader-writer ID R Generate encrypted information and send a message Ai to the tag;
[0065] (2) After the tag receives the message A, based on the stored reader ID R Can get random number Utilize the MIXBITS function to generate the second random number ri2=MIXBITS(ID R ,ri1), combined with the reader ID R Generate encrypted information And use Rabin encryption to generate the eleventh verification information And send the message combination eight (Ri, Mi1, i) to the reader;
[0066] (3) After the reader / writer receives the message combination eight (Ri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com