A security authentication method, device and system
A security authentication and authentication failure technology, applied in the field of information security, to achieve the effect of solving security authentication problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
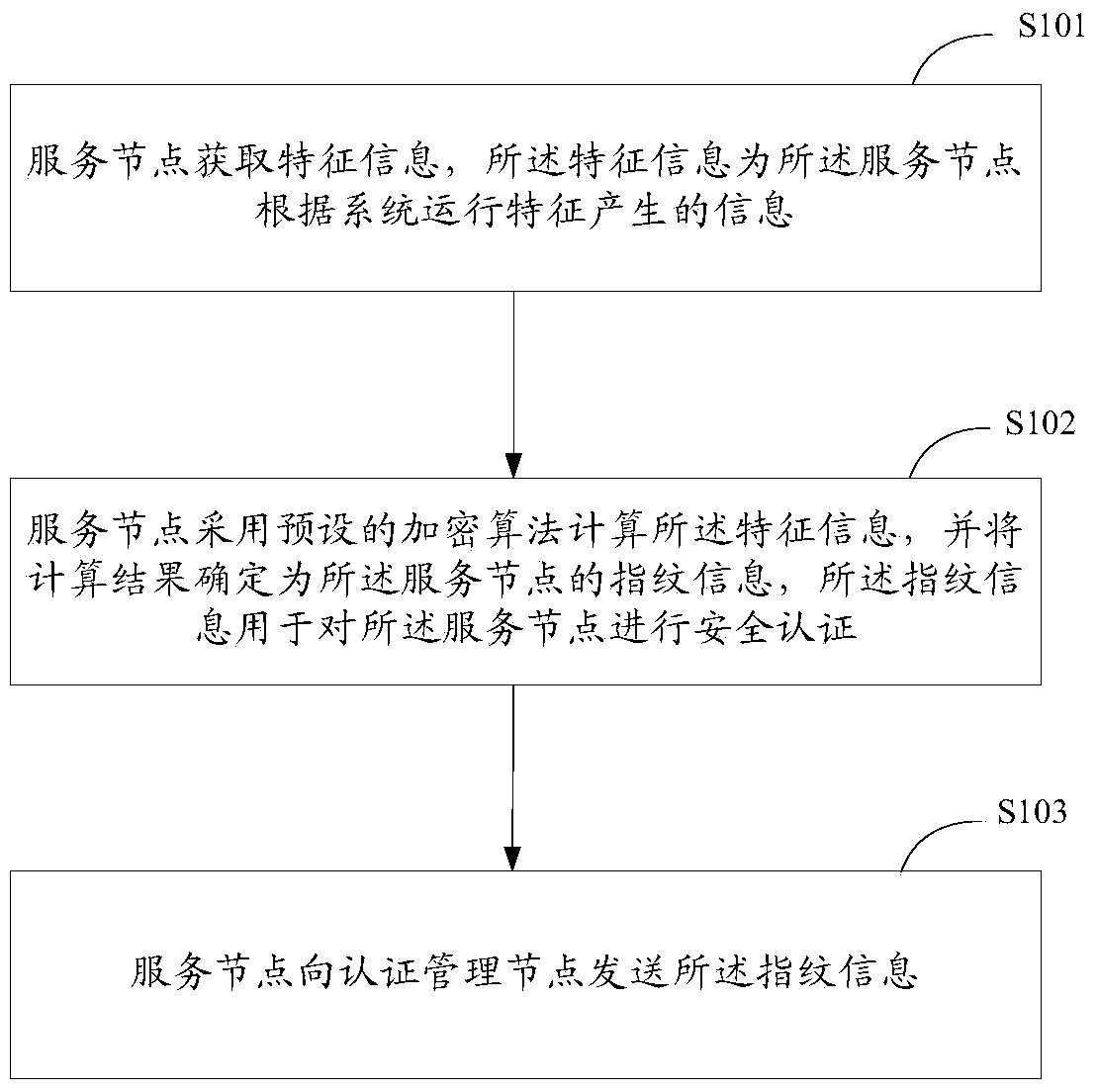
[0060] figure 1 A schematic flow chart of the first embodiment of the security authentication method provided by the present invention, as shown in figure 1 The shown flow of the first embodiment of the security authentication method provided by the present invention includes:
[0061] S101. The service node acquires characteristic information, where the characteristic information is information generated by the service node according to system operation characteristics.
[0062] Specifically, the service node needs to obtain characteristic information according to its own operating characteristics, including static information and dynamic information of the service node.
[0063] Among them, the static information includes the current user name and specific software information. The current user name is the user name of the service node that currently has certain permissions, and the specific software is the custom-developed software or other software loaded on the service n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com