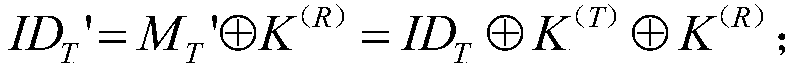A RFID security authentication method based on superprime
A technology of security authentication and super prime numbers, applied in secure communication devices and key distribution, to achieve the effects of long cycle, freshness assurance and security improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
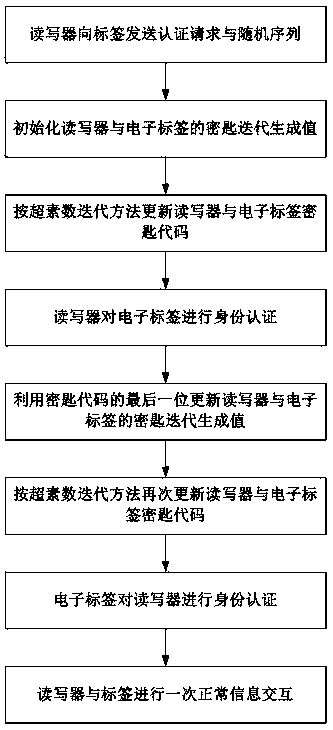
[0033] Such as figure 1 Shown, a kind of RFID security authentication method based on superprime number, this method comprises following sequence
[0034] A step of:
[0035] (1) The reader sends a query message Query authentication request and a random sequence R to the tag 0 ;
[0036] (2) Initialize the key iteratively generated value Z of the reader and electronic tag 1 (R) and Z 1 (T) :Z 1 (R) =K p (R) , in with Taken from the master control keys in the reader-writer and the electronic tag security module respectively, the superscripts (R) and (T) represent the attributes of the reader-writer and the electronic tag respectively, and the subscript P represents the master control attribute;
[0037] (3) Utilize the superprime iteration method to update the real-time key code K of the reader (R) ={Z 1 (R) Z 2 (R) …Z I (R)} and label real-time key K (T) ={Z 1 (T) Z 2 (T) …Z I (T)}, where the superscripts (R) and (T) respectively represent the att...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com