Security authentication method and security authentication device
A security authentication and security technology, applied in the field of security authentication and security authentication devices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The technical solutions in the present application will be described below with reference to the accompanying drawings.
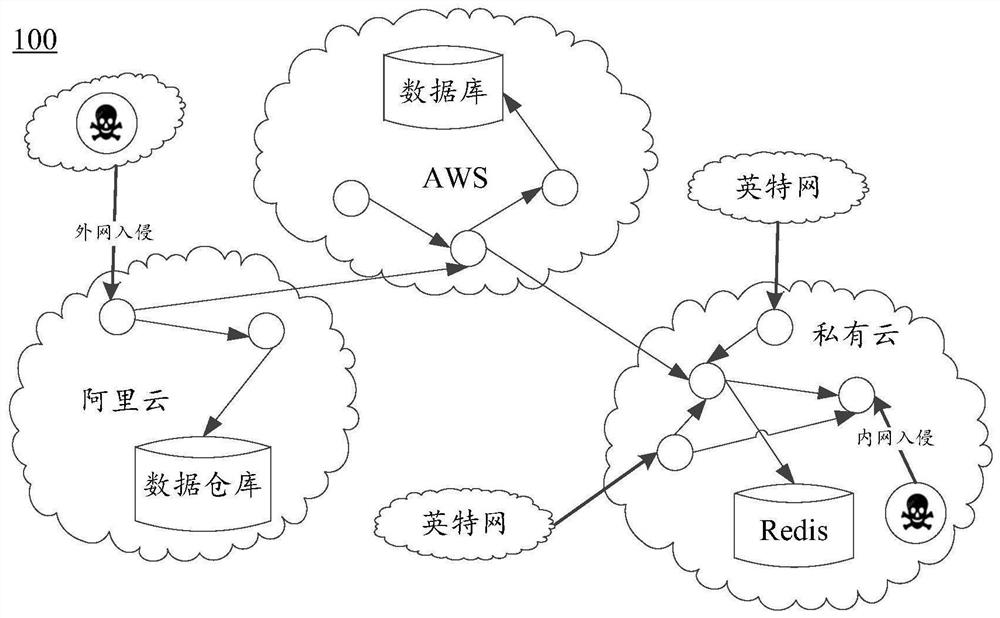
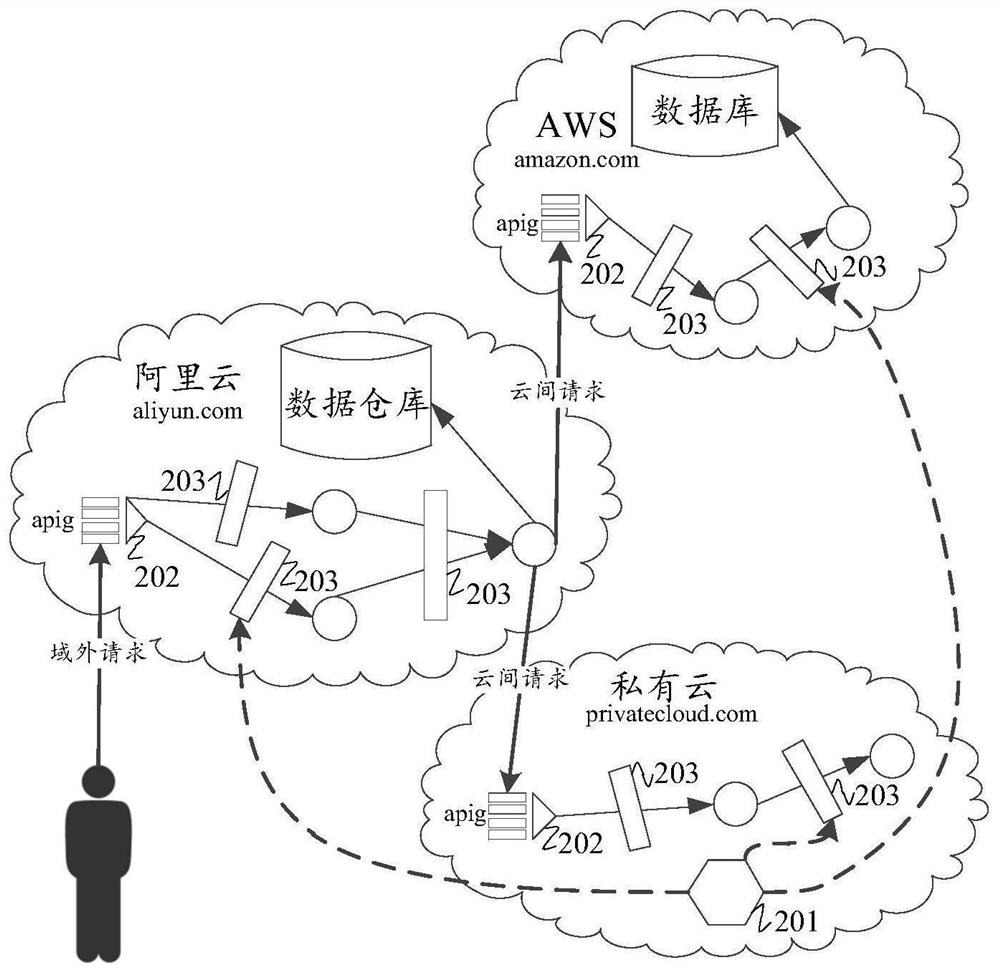
[0042] Cloud technology has been accepted by more and more enterprises, and major enterprises have gradually put their business systems in the cloud. The public cloud market at home and abroad has gradually formed a separate scale. They each have their own market strengths, provide different capabilities, characteristics, and pricing strategies. Therefore, enterprises have to face the problem of multi-cloud applications (multicloud) and hybrid cloud applications (hybrid cloud) in the process of migrating to the cloud.
[0043] Under this multi-cloud architecture, a business system is often composed of application systems distributed in different cloud providers or geographical locations. In addition, cloud applications are often a dynamic body, and the scale of the entire application system will dynamically scale with changes in customer needs. In ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com