Fraud user detecting method, fraud user detecting device and fraud user detecting system
A detection device and detection method technology, applied in the field of communication, can solve problems such as switch failure, affecting system stability, and large traffic volume, and achieve the effect of reducing losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0045] The embodiment of the present invention provides a method for detecting a fraudulent user. The method for detecting a fraudulent user is as follows: according to the set fraud identification rules, extract the information from the user's trial call bill or short message calling bill within the detection period. The data is analyzed to identify fraudulent users.
[0046] Wherein, the call trial record is generated when the ringing time of the call is less than a preset value and the call is not in a talking state.
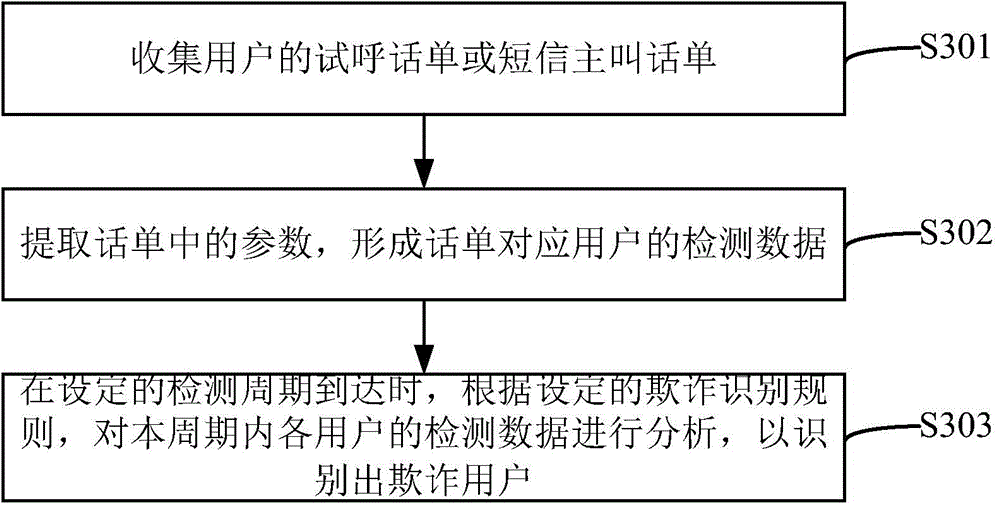
[0047] The detailed implementation process is as image 3 shown, including:
[0048] Step S301, collecting the user's trial call bill or short message calling bill;
[0049] Step S302, extracting parameters in the bill to form detection data corresponding to the user in the bill;
[0050] Step S303, when the set detection period arrives, analyze the detection data of each user in this period according to the set fraud identification rules, so as to identif...
Embodiment 2
[0087] The invention provides a fraud detection device, which can be an independent third-party device or a module integrated in MSC Server. In consideration of not affecting the working efficiency of the MSC Server, the fraud detection device of the present invention is preferably an independent third-party device. When it belongs to an independent third-party device, add a communication interface on the fraud detection device and MSCServer, so that the fraud detection device can receive the trial call bill and SMS caller bill sent by MSCServer, as well as the detected fraudulent user The MSC Server is notified, so that the MSC Server restricts the call or short message service of the fraudulent user.
[0088] like Figure 7 As shown, the fraud detection device described in this embodiment includes:
[0089]The fraudulent user identification module 710 is configured to analyze the data extracted from the user's call attempt or SMS caller in the detection period according to...
Embodiment 3
[0102] An embodiment of the present invention provides a detection system for fraudulent users, including: MSCServer and the fraud detection device described in Embodiment 2;
[0103] MSCServer is used to generate call trial bills and short message calling bills for the user, and send the trial call bills and short message calling bills to the fraud detection device.
[0104] Further, the fraud detection device is further configured to send the number of the fraudulent user and the service restriction policy set for the fraudulent user to the MSCServer;
[0105] MSCServer adds the fraudulent user's number to the blacklist, and restricts the fraudulent user's service according to its corresponding service restriction policy.
[0106] To sum up, by adopting the system of the present invention, it is possible to timely discover and limit the use of mass message senders to send fraudulent short messages, or to use group calls to harass users in the entire number segment of the ope...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com