A method of improving public Wi-Fi network security based on wpa/wpa2 PSK multi-cipher
A security, multi-password technology, applied in the field of information security, can solve the problems of cumbersome use, high overhead, complicated encryption algorithms, etc., and achieve the effect of improving confidentiality, improving security, and avoiding theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
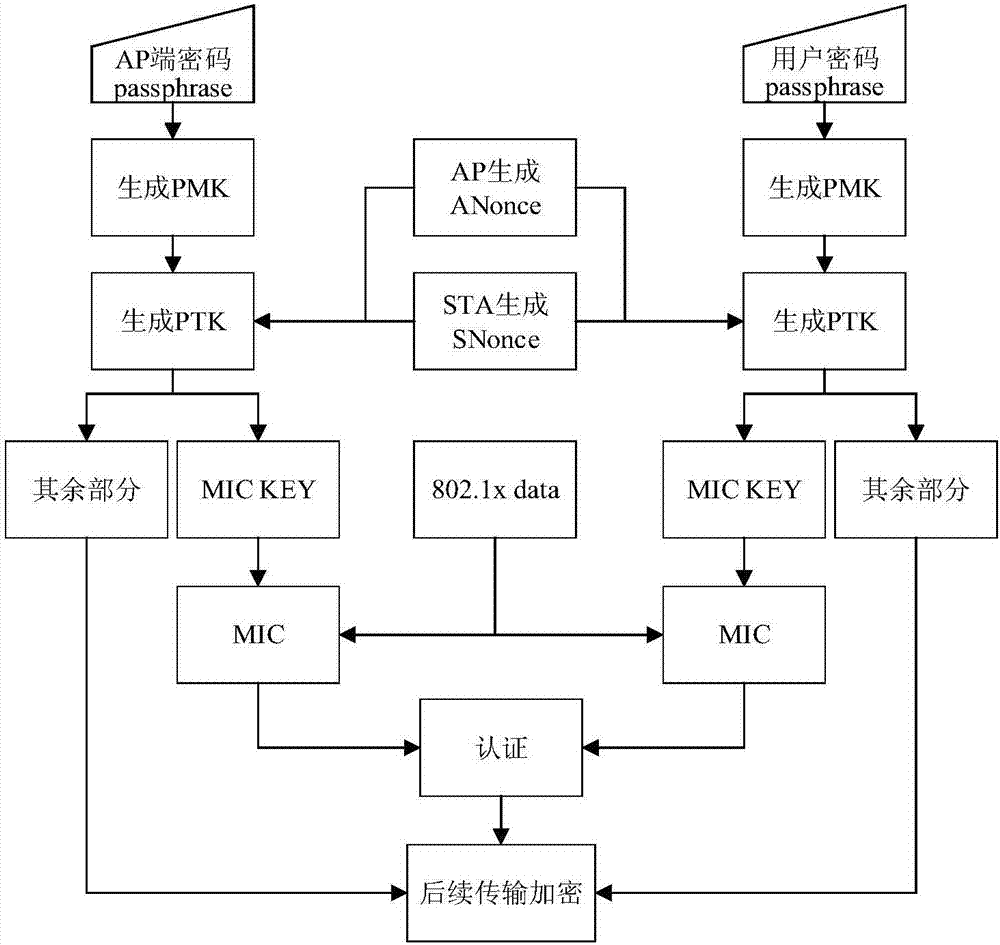
[0022] Specific implementation mode one: the process is as follows:
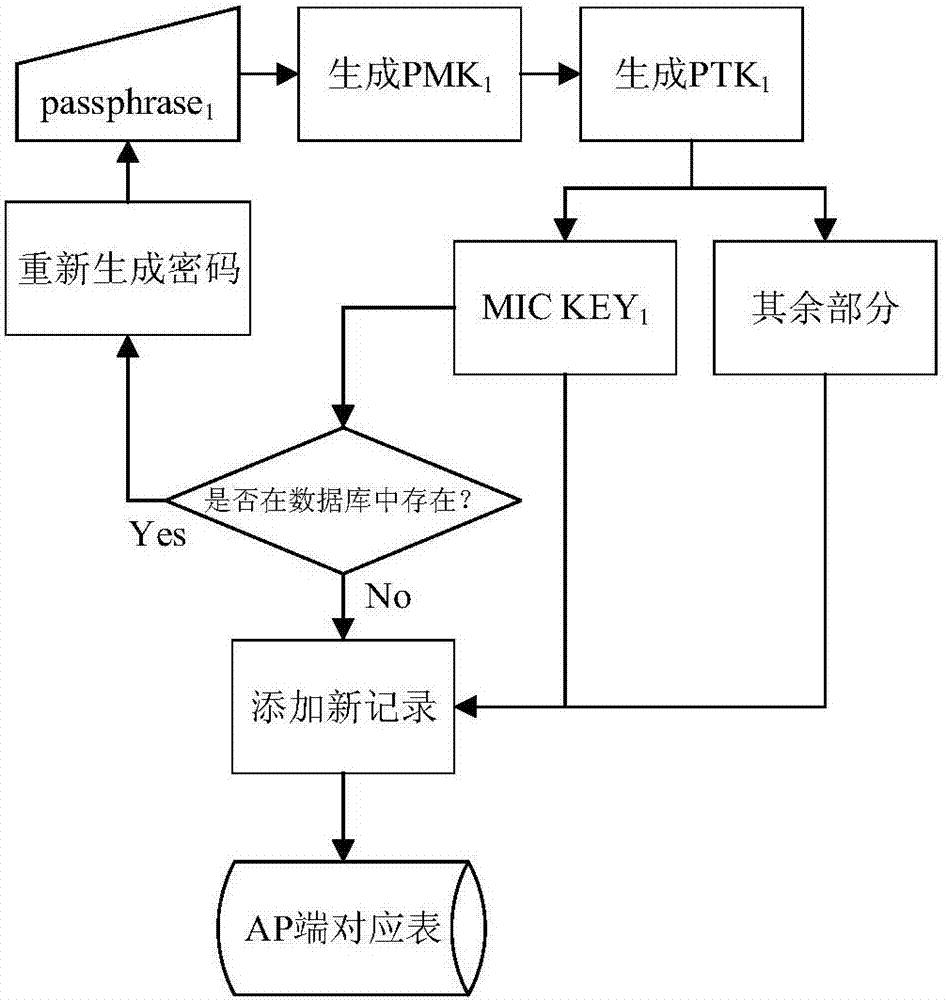
[0023] 1. Update the corresponding table data on the AP side, specifically including the following steps: The AP side randomly generates the user password passphrase 1 , the password is different for each client and is notified to the user in a private manner; the AP uses passphrase 1 Generate PMK 1 , reuse PMK 1 Generate PTK 1 ;PTK 1 Split into MIC KEY 1 and the rest, PTK 1 The first 16 bytes are MIC KEY 1 ;Retrieve the MIC KEY in field 1 of the corresponding table on the AP side 1 , if it exists, re-generate a new password randomly on the AP side; if it does not exist, the password is available, and then use the MIC KEY 1 As field 1, PTK 1 The remaining part is used as field 2 to generate a new record and store it in the corresponding table on the AP side to complete the update of the corresponding table data on the AP side. The corresponding table includes storing the MIC KEY 1 Field 1 and store...
specific Embodiment approach 2
[0026] Specific implementation mode two: the AP informs the client device of the user password passphrase in a private manner 1 In this case, the private method can be a mobile phone text message or scan a two-dimensional code. For example, when you register your mobile phone number when you check into a hotel, you will randomly generate a password and send it to the customer with a short message. Shops, restaurants, etc. can set up a small screen at the front desk to display the randomly generated password. The QR code with SSID and passphrase will be regenerated and displayed or updated regularly every time STA connects.
specific Embodiment approach 3
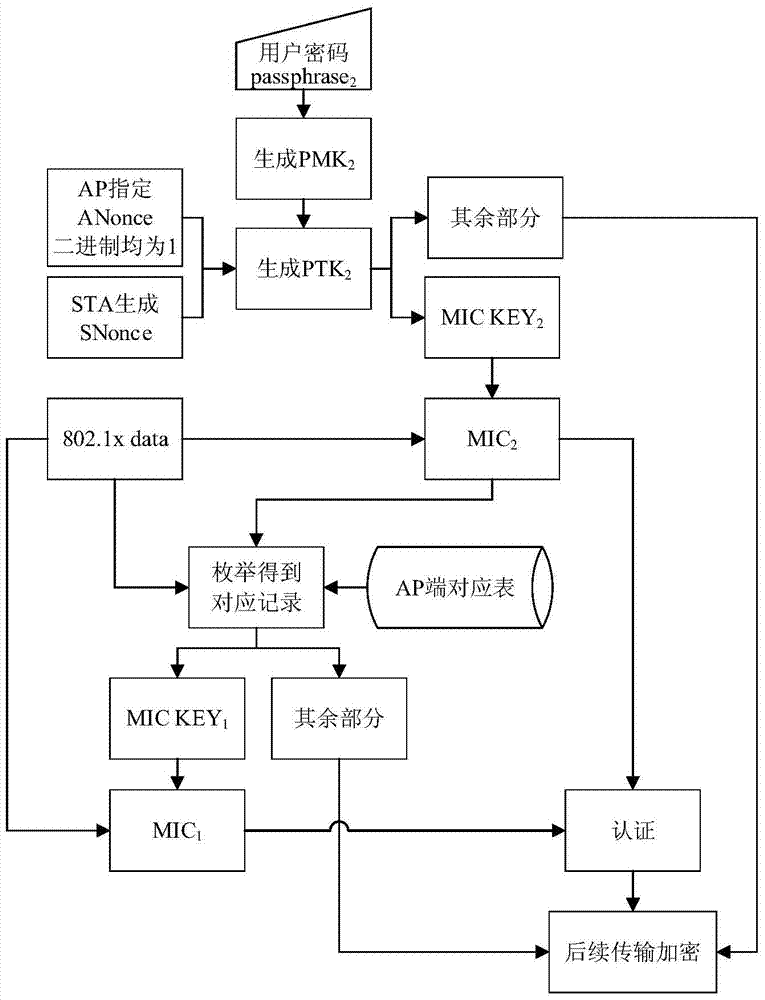
[0027] Specific implementation mode three: This implementation mode is characterized in that: the AP uses passphrase 1 Generate PTK 1 , the PTK 1 Divided into MIC KEY 1 and the rest, the MIC KEY 1 Use it as field 1, and use the rest as field 2 to establish the AP-side correspondence table or complete the data update of the AP-side correspondence table. This method is relatively simple and easy to implement. In this way, the data stored on the AP side can only complete authentication verification and transmission encryption, and cannot reverse the passphrase, thereby preventing user password leakage caused by database leakage.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com