An information security risk assessment method for typical metallurgical process control systems
A control system and process control technology, which is applied in general control systems, control/regulation systems, testing/monitoring control systems, etc. It can solve the problem of large control system network topology and is in its infancy. The research has not been reported yet, and the single equipment cost is high
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
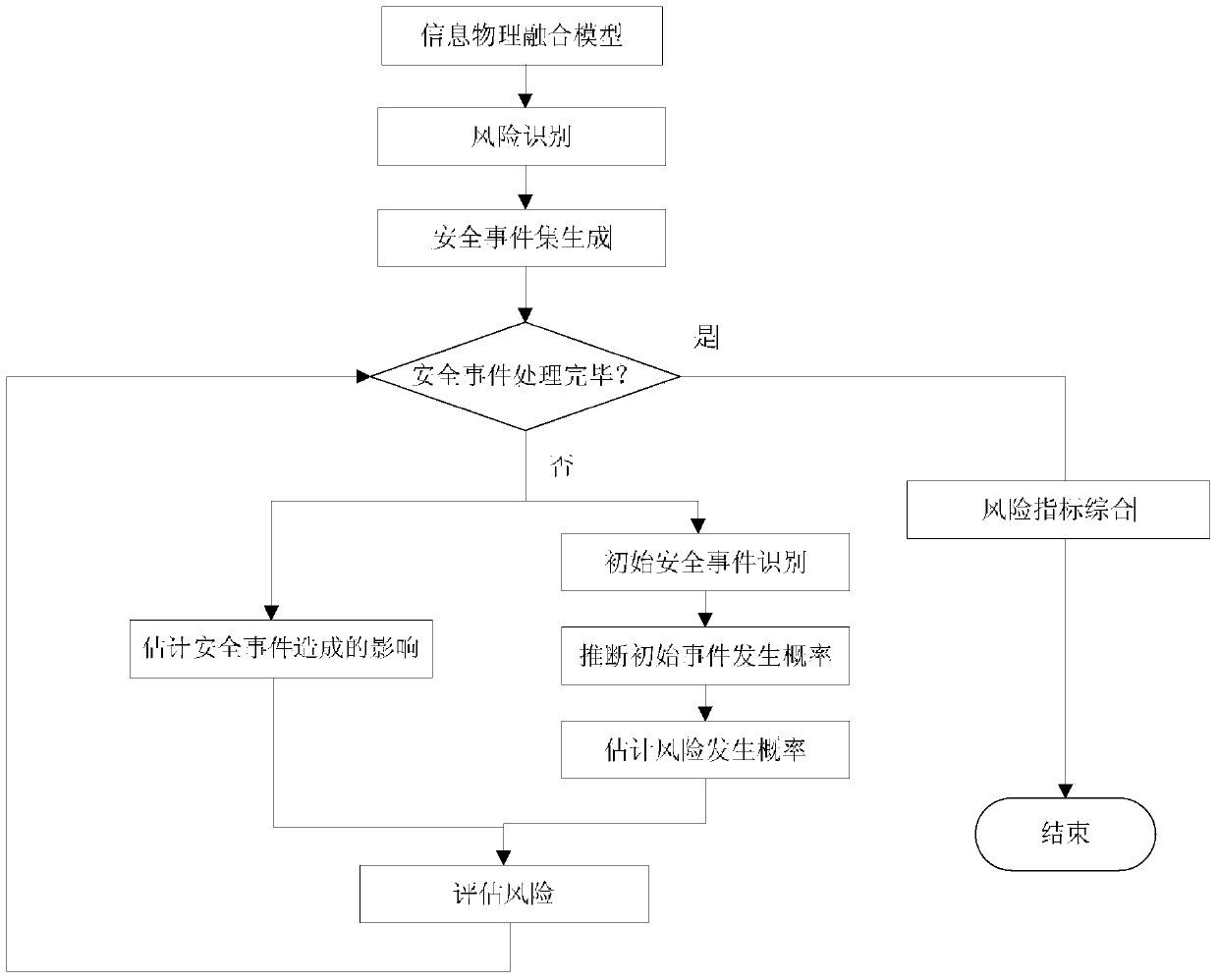
[0044] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments. Such as figure 1 shown, including the following steps:
[0045] (1) For the typical metallurgical process flow control system, the mathematical modeling of the control system based on cyber-physical fusion is carried out. Model method, in which the continuous dynamic model related to the metallurgical process flow is represented by a set of traditional linear or nonlinear differential equations / equations of state, and is realized with the Matlab Simulink toolbox; discrete events are represented by the Petri Net (PN) model, And use a Simulink toolbox PNL to implement, the PN discrete model can be integrated into the Simulink block diagram, and the synchronization state transfer of the petri Net model mainly depends on the triggering of external events. At the same time, the Petri Net model is extended to model the communication network component...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com