Identity authentication system, device and method and identity authentication requesting device
An identity authentication device and identity authentication technology, applied in the field of identity authentication request device and identity authentication system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
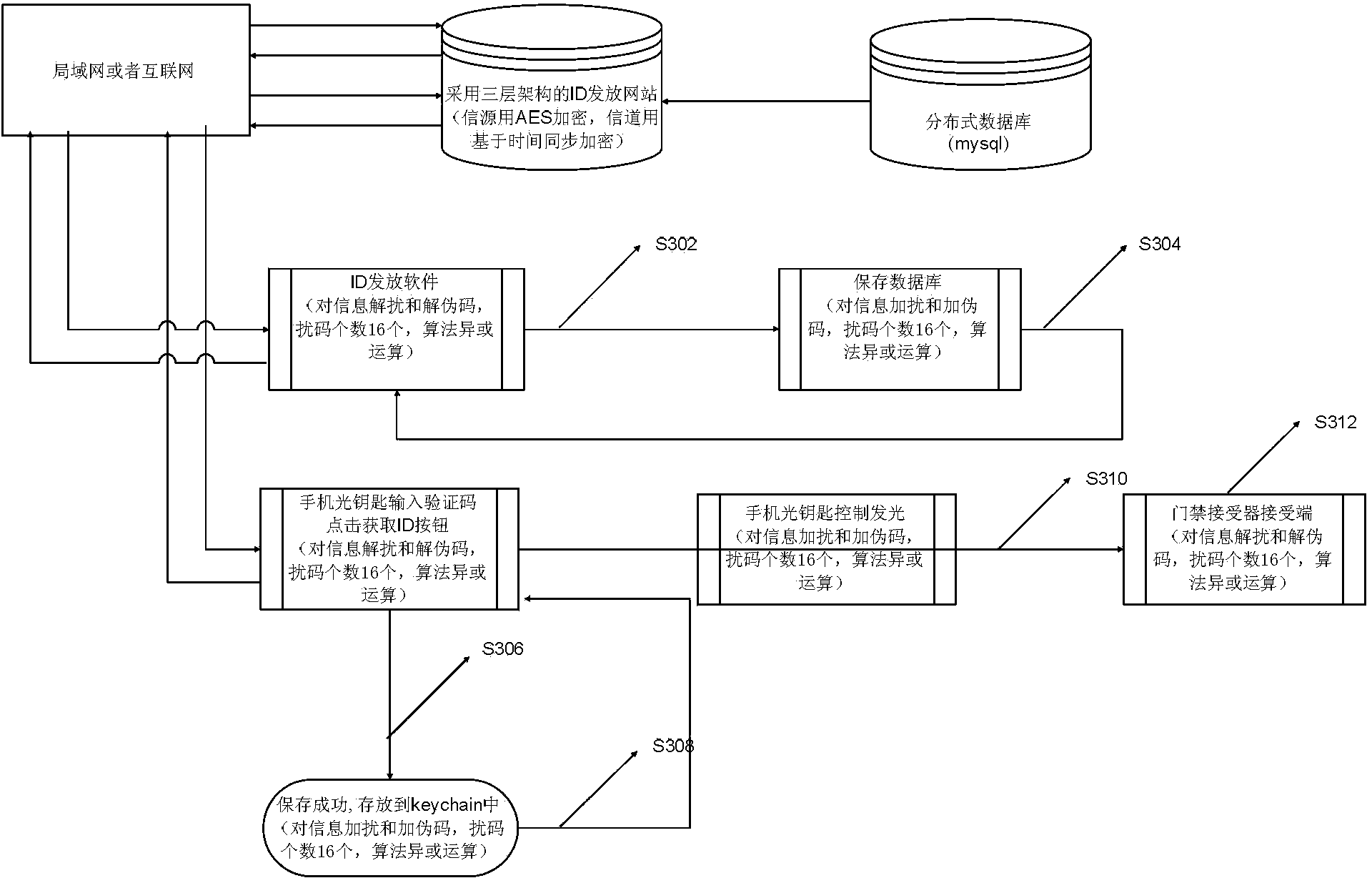
[0084] image 3 It is a flow chart of adding and descrambling information and adding and decoding pseudocodes by the identity authentication system according to the preferred embodiment 1 of the present invention, as shown in image 3 As shown, the process includes:
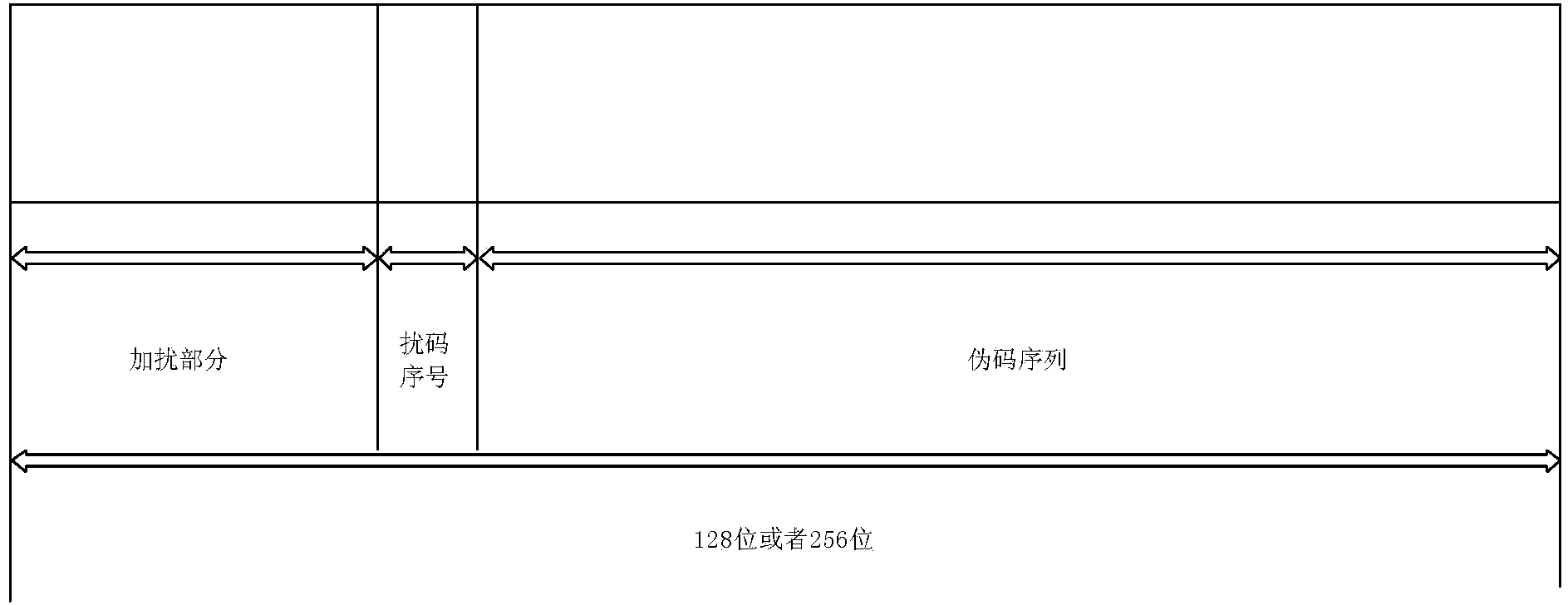
[0085] S302: After the ID issuance software obtains the ID number and verification code through the network, it performs scrambling and pseudo-code operations on the two types of information, obtains two ciphertexts, and saves them in the relevant records in the ID allocation table of the database. The security of the content of the data table, wherein the scrambling code group used is composed of 16 scrambling codes, the scrambling algorithm uses an XOR operation, and the length of the pseudo-code scrambling code is 128 bits.
[0086] S304: In order to facilitate viewing of the ID distribution situation, a table is designed to display the assigned ID serial number and verification code list, so that the ciphert...
Embodiment 2
[0093] Figure 4 It is a flow chart of adding and descrambling information and adding and decoding pseudocodes by the identity authentication system according to the second preferred embodiment of the present invention, as shown in Figure 4 As shown, the process includes:
[0094] S402: After the ID issuance software obtains the ID number and verification code through the network, it performs scrambling and pseudo-code operations on the two types of information, obtains two ciphertexts and saves them in the relevant records in the ID allocation table of the database, ensuring The security of the content of the data table, wherein the scrambling code group used is composed of 64 scrambling codes, the scrambling algorithm uses an XOR operation, and the length of the pseudo-code scrambling code is 128 bits.
[0095] S404: In order to check the status of ID issuance conveniently, a table is designed to display the assigned ID serial number and verification code list, so that the...
Embodiment 3
[0102] Figure 5 It is a flow chart of adding and descrambling information and adding and decoding pseudocodes by the identity authentication system according to the third preferred embodiment of the present invention, as shown in Figure 5 As shown, the process includes:
[0103] S502: After the ID issuance software obtains the ID number and the verification code through the network, it performs scrambling and pseudo-code operations on the two types of information, obtains two ciphertexts, and saves them in the relevant records in the ID allocation table of the database. For the security of the content of the data table, the scrambling code group used is composed of 128 scrambling codes, the scrambling algorithm uses an XOR operation, and the length of the pseudo-code scrambling code is 256 bits.
[0104] S504: In order to facilitate viewing of ID issuance, a table is designed to display the assigned ID serial number and verification code list, so that the ciphertext in the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com