Cloud computing-based identity authentication fusion method
A technology of identity authentication and cloud computing, applied in the field of identity authentication, achieves great commercial and social value, good scalability, and solves security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
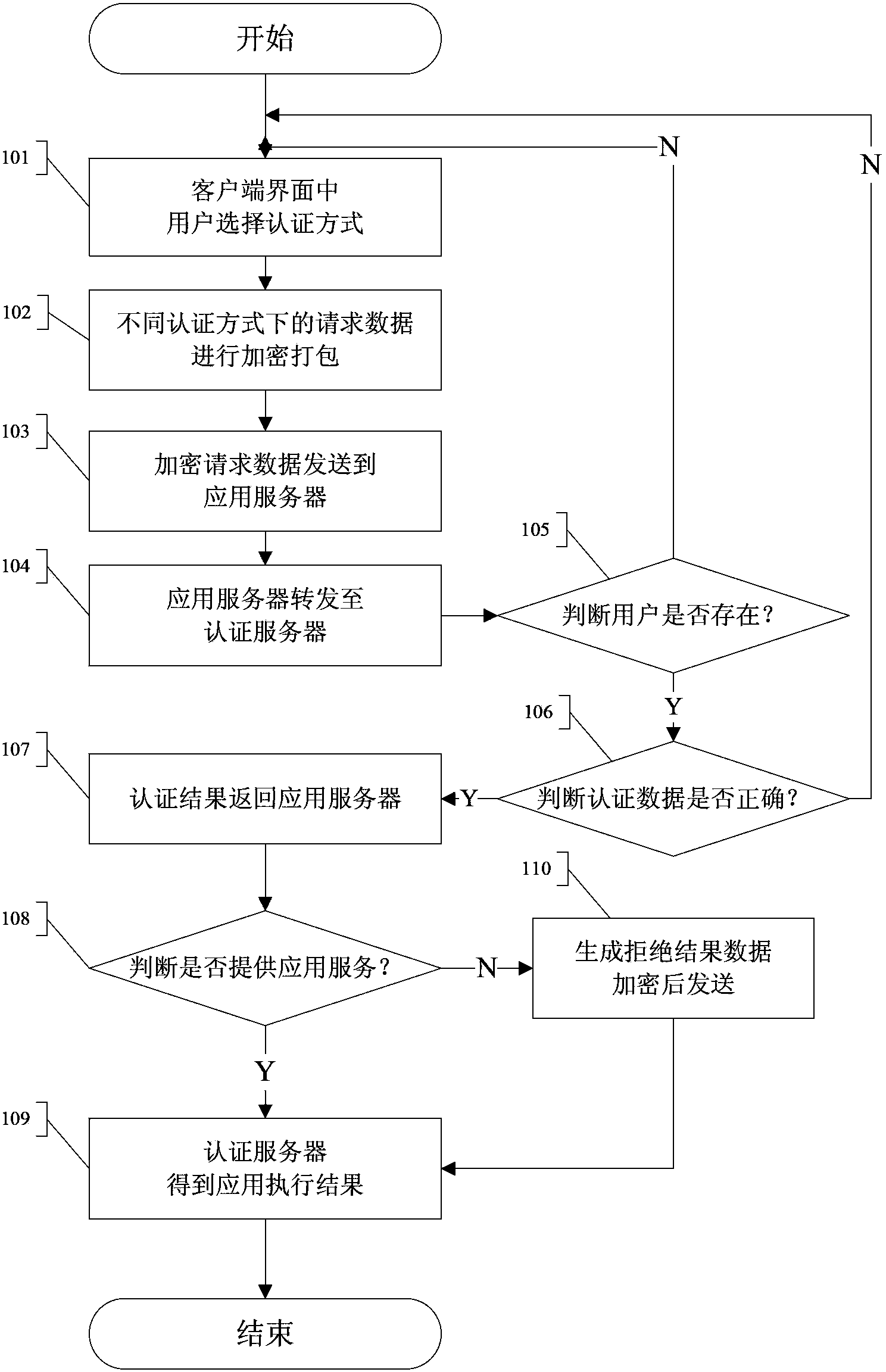
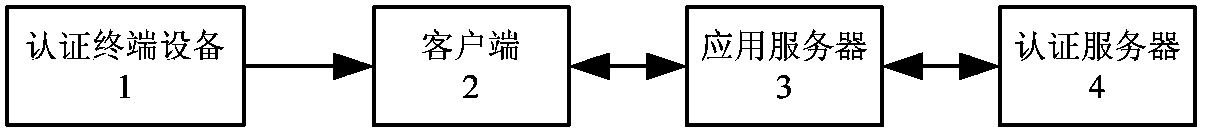
[0035] Such as figure 1 As shown in Fig. 1, a fusion identity authentication method based on cloud computing, this method adopts the unique distributed cluster management of cloud computing, integrates an infinite number of existing strong identity authentication methods through a unified standard interface, and provides users with a single entry The authentication interface, and users can independently choose authentication methods of different security levels according to their immediate needs, so as to realize the effective protection of network identity security through the public cloud and private cloud architecture in the cloud computing environment. The specific steps are as follows:
[0036] In step 101, the user independently selects an authentication method in the client, and then performs step 102;
[0037] In step 102, the request data under different authentication methods are automatically encrypted and packaged, and then step 103 is executed;
[0038] In step 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com