NAT penetration-based video monitoring access strategy and realization method
A technology of access strategy and implementation method, which is applied in closed-circuit television systems, electrical components, transmission systems, etc., can solve problems such as inability to support equipment, difficulty in NAT penetration, and cumbersome configuration, so as to achieve simple and convenient equipment configuration and improve success The effect of probability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
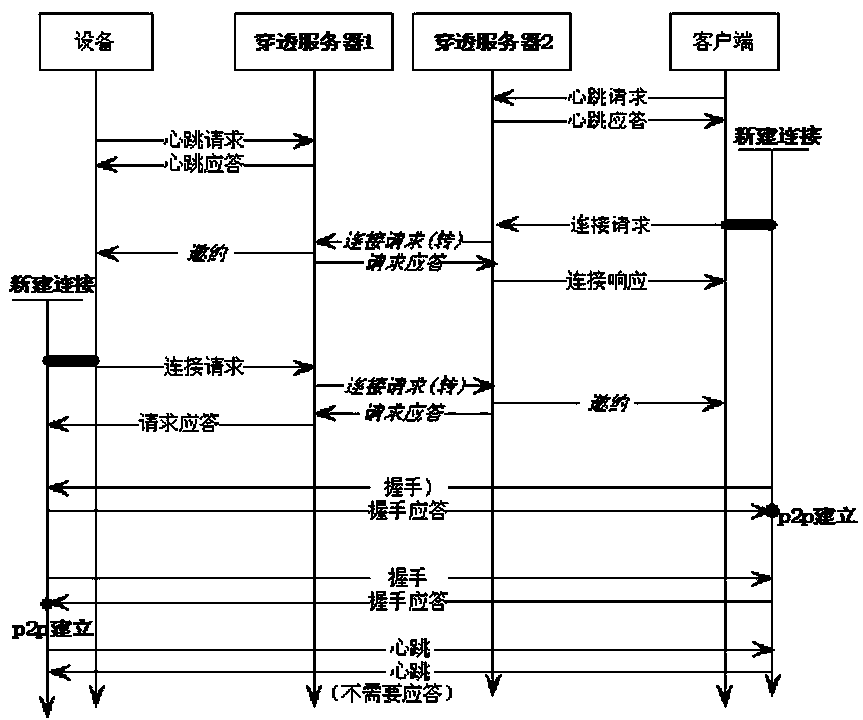
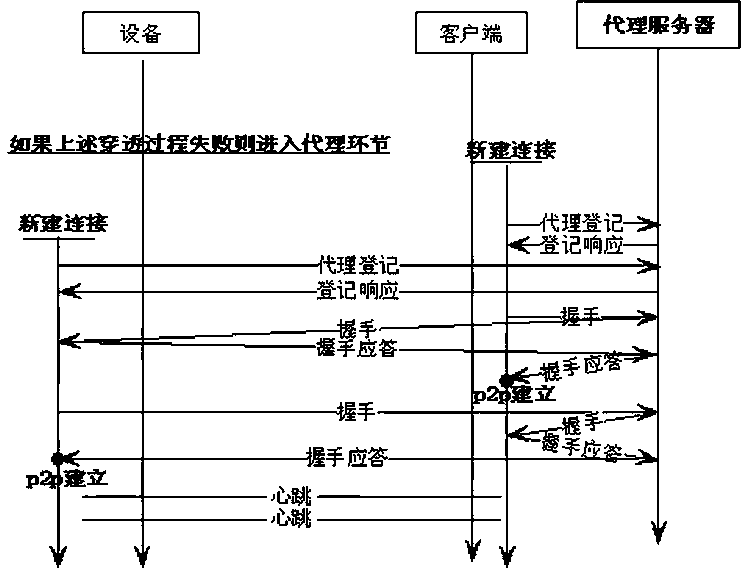
[0030] figure 1 Shown is a whole penetration flow chart of a NAT penetration-based video surveillance access strategy and implementation method of the present invention. This method is divided into the following steps through the flow chart: device registration, connection request, and handshake confirmation; the former step is the basis and trigger condition of the latter step.
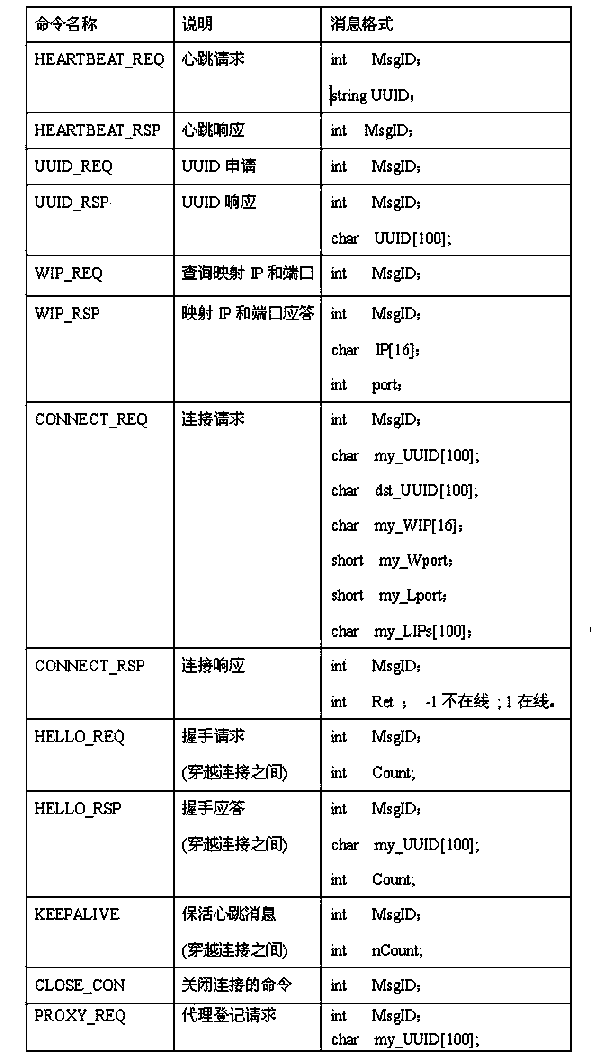
[0031] 1) Device registration: After the device is powered on and running, it will go to the DNS server to query the corresponding IP address information according to the domain name of the NAT server configured by the user. After obtaining, such as figure 1 As shown, a heartbeat request is sent to the server corresponding to the IP address (for example, penetration server 1). This information includes the serial number of the device. After the penetration server 1 receives the heartbeat request sent by the device, it first constructs a device information table according to the number and the exte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com